1 Introduction
This chapter examines how a cyberattack (i.e., a cyber-enabled malicious activity) that has consequences similar to a kinetic or physical attack (causing serious loss of life or physical damage) could be encompassed within the crimes that may be prosecuted before the International Criminal Court (ICC). The chapter overviews when and how such a cyberattack could fall within the ambit of the ICC’s crimes – genocide, crimes against humanity, war crimes, and the crime of aggression. The chapter additionally acknowledges some of the limitations as to which attacks would be encompassed, given, particularly, the gravity threshold of the ICC’s Rome Statute, as well as the hurdle of proving attribution by admissible evidence that meets the standard of proof beyond a reasonable doubt. Notwithstanding such limitations, there is still potential for use of the Rome Statute to encompass a limited subset of cyberattacks. Increased awareness of this previous largely overlooked potential could possibly contribute to deterring such crimes, as could prosecution of those cases of cyberattacks that meet the standard of proof by required by the ICC Rome Statute. While it is very difficult to measure the deterrent impact of tribunals and international criminal law, whatever possible deterrence that can be created is certainly worth maximizing. This chapter explores how international criminal law could potentially contribute to the goal of reaching a state of “cyber peace.” Admittedly, the Rome Statute would not encompass the vast number of cybercrimes that occur, as it would only cover the more severe cyberattacks, such as those inflicting serious loss of life or significant physical damage; however, the Rome Statute does have applicability in this area to cover at least a limited subset of cyber operations, and this potential should be explored and utilized. The ICC can only help contribute to deterrence and cyber peace if the ability of the ICC to prosecute certain cyberattacks becomes acknowledged and well known.
2 Background
Cyberattacks can take a variety of forms including those aimed at data theft (stealing corporate information) (Griffiths, Reference Griffiths2015; as cited in Jensen, Reference Jensen2017, p. 736, n. 6), extortion, the spreading of false information (Greenfield, Reference Greenfield2013; as cited in Jensen, Reference Jensen2017, p. 736, n. 7), manipulation of elections (Hathaway et al., Reference Hathaway, Crootof, Levitz, Nix, Nowlan, Perdue and Speigel2012, p. 819; Ohlin, Reference Ohlin2020), breach of government computers in an effort to steal state secrets (O’Hare, Reference O’Hare2016; as cited in Jensen, Reference Jensen2017, p. 737, n. 8,), as well as denial of service attacks (U.S. Department of Homeland Security and the Cybersecurity and Infrastructure Security Agency [CISA], 2019). Such attacks sometimes proliferate beyond their intended targets to impact information technology (IT) systems around the globe, as with the infamous NotPetya attack (Greenberg, Reference Greenberg2018; Efrony & Shany, Reference Efrony and Shany2018, pp. 628–631). Further, the software code used in cyberattacks may also be “repurposed” by others (Bellovin et al., Reference Bellovin, Landau and Lin2017). Fortunately, to date, cyberattacks and cybercrimes have not resulted in widespread devastation causing loss of life and, to the extent physical damage has resulted, such damage has occurred more to data, computer hardware and software and, in one instance, to centrifuges at a nuclear facility (the Stuxnet attack). Cyberattacks have also caused massive economic losses (Greenberg, Reference Greenberg2018) and compromised the personal information of millions of individuals (Jensen, Reference Jensen2017, p. 737).
The use of cyber technology to date, however, makes clear that a much more catastrophic cyberattack could occur. States (on their own, or in conjunction with nonstate actor/hacker groups) now have the capacity to combine cyber weapons with conventional weapons into a “blended attack,” such as occurred in Ukraine (Greenberg, Reference Greenberg2018) and Georgia (ICC Forum, 2018). A number of war crimes that could be committed during a conventional armed conflict could now, potentially, also be committed through the use of cyberattacks or through both cyber and conventional means. Absent a state of armed conflict, cyberattacks meeting the requirements of, inter alia, a widespread or systematic attack against a civilian population could fall within the ambit of “crimes against humanity.” For example, the technological capacity to disable air traffic controls exists, causing a “cyber 9/11” – perpetrated, for example, by nonstate actors (cyber criminals or bands of hackers). A cyberattack could similarly target computer systems that control train traffic, nuclear facilities (Greenberg, Reference Greenberg2017a), hospitals (Glaser, Reference Glaser2017; Mačák et al., Reference Mačák, Gisel and Rodenhäuser2020), power grids (Greenberg, Reference Greenberg2017b, Reference Greenberg2018), and other critical infrastructure – or, for example, a dam located upstream from a major city (Berger, Reference Berger2016). It is this narrow subset of cyberattacks – causing serious loss of life and/or physical destruction – not the vast number of cybercrimes being perpetrated – that this chapter addresses.
While one hopes that a large-scale cyberattack, or even a more limited one that causes serious loss of life or damage to physical objects, will never reach fruition, it is simultaneously helpful to acknowledge that should such an attack occur, it potentially could be covered by one or more of the crimes provided for under the ICC’s Rome Statute. States, particularly Rome Statute States Parties, could also incorporate Rome Statute crimes into their domestic criminal codes and statutory law (if they have not already done so), and/or develop additional laws criminalizing cyberattacks and/or cybercrimes. Should they do so, domestic definitions of the crimes could be more broadly formulated than their Rome Statute counterparts and have greater jurisdictional reach; thus, the limitations of the Rome Statute discussed in this chapter do not necessarily carry over to domestic jurisdictions. While the international community could also create a new international criminal tribunal to deal exclusively with cybercrime and cyberattacks, in light of the apparently unwillingness to create new criminal tribunalsFootnote 1 this chapter focuses on the permanent international criminal tribunal that already exists, the ICC.
3 Maximizing the Potential for Cyber Peace through Deterrence
The goal of the present chapter is not only to make the case for ICC cyber prosecutions should a horrific attack occur but to increase awareness of the potential for ICC prosecutions in order to maximize the potential for deterrence as a means to contribute to achieving a state of “cyber peace” (see Shackelford, Reference Shackelford2017, p. 8, defining “cyber peace”). It is important that the cyber domain is not seen as unfettered by the rule of law, when it is in fact subject to numerous bodies of international law (UK Government, 2018; Koh, Reference Koh2012, p. 3), including international humanitarian law (aka the laws of war) (Schmitt, Reference Schmitt2017, Rule 80; “The Paris Call,” 2018), international human rights law (Schmitt, Reference Schmitt2017, Rule 35), as well as the use of force norms contained within the UN Charter as supplemented by customary international law (Schmitt, Reference Schmitt2019 (citing position of France, and the UK Government, 2018, noting also that Russia and China accept that the UN Charter applies in cyberspace)). The more well acknowledged it is that international humanitarian law and international human rights law apply in the cyber domain, the easier it is to make the case that certain cyberattacks are covered under international criminal law. Even if the application of current bodies of international law to cyberattacks may not prove an “elegant fit,” it is imperative to utilize the laws that exist and/or develop additional laws (cf. Rona, Reference Rona2003, p. 60, arguing International Humanitarian Law (IHL) should apply to the “war on terror” even if “not an elegant fit”).
Significant academic literature exists on the subject of whether international criminal law can play a deterrent role and whether the existence of the various ad hoc and hybrid criminal tribunals has contributed to deterrence and/or the ICC can do so.Footnote 2 Various scholars take a pessimistic stance as to the potential of tribunals to deter atrocity crimes (McAllister, Reference McAllister2019–20, p. 85, n. 2, categorizing scholars as “deterrence pessimists”). Yet, increasingly, there are scholars whose studies yield positive results (McAllister, Reference McAllister2019–20, p. 85, n. 4, categorizing scholars as “deterrence optimists”). For example, a recent study, based on over 200 interviews, demonstrates that Macedonian Armed Forces, during the 2001 conflict in Macedonia, considered the existence of the International Criminal Tribunal for the former Yugoslavia (ICTY) when deciding their actions (specifically, whether any could be viewed as war crimes), and this deterred violence against civilians (McAllister, Reference McAllister2019–20; see also Schense & Carter, Reference Schense and Carter2017). Similar studies show some deterrence created by the existence of the ICC (Jo & Simmons, Reference Jo and Simmons2016; Hillebrecht, Reference Hillebrecht2016; Human Rights Watch, 2009, Ch. IX).
It is worth noting that domestic criminal law also does not fully deter domestic crimes; yet states nonetheless criminalize crimes, from murder to insider trading. So too with international criminal law. As Brierly observes: “States often violate international law, just as individuals often violate municipal law” (Brierly, Reference Brierly1944, pp. 4–5). Clearly, the field of international justice has not yet fully deterred crimes such as genocide, crimes against humanity, or war crimes, as these crimes still occur far too often. Furthermore, it is also notoriously hard to prove a negative – that is, that crimes have not occurred due to the deterrent impact of tribunals or international criminal law – so there could actually be more deterrence than can be conclusively demonstrated. Yet, the case that one should not criminalize atrocity crimes is generally not made; clearly, whatever role deterrence can play is worth maximizing, and if international criminal laws and tribunals are incapable of deterring or not fully capable of doing so, then at least the laws exist whereby the crimes may be prosecuted. In short, international criminal law is one of the tools at the disposal of those working in the field of international justice, and while it may not fully deter, any deterrence potential is useful. As Guido Acquaviva writes: “international criminal institutions” that “strengthen[] the rule of law and pursu[e] individual criminal responsibility” “can increase awareness of the primary rules … among the general public and … foster compliance with the law and therefore, indirectly, general deterrence” (Acquaviva, Reference Acquaviva2014, p. 786).
The United States, for instance, suggests that the prosecution of cyberattacks can change behavior. Kristen Eichensehr explains:
One of the most often-cited purposes of public attributions [of cyberattacks] is macro-level deterrence. The idea is that public naming-and-shaming of state-sponsored actors will cause the named states (and potentially other states that might be watching) to refrain from future attacks. For example, in announcing an indictment of Iranian hackers for [Distributed Denial of Service (“DDOS”)] attacks on U.S. financial institutions, then-FBI Director James Comey explained, “By calling out the individuals and nations who use cyber attacks to threaten American enterprise, as we have done in this indictment, we will change behavior.” U.S. officials made similar claims about the cyber sanctions executive order. In announcing the new sanctions regime, the Obama Administration’s Cybersecurity Coordinator, Michael Daniel called it “a new way of both deterring and imposing costs on malicious cyber actors wherever they may be.”
Eichensehr notes that: “After the first U.S. attribution-by-indictment – the charges against Chinese [People’s Liberation Army] officers for intellectual property theft – sources indicated that the Chinese military substantially scaled down its economic espionage activities. But at the same time, [Eichensehr admits] state-sponsored hacks of many kinds have continued after indictments” (Eichensehr, Reference Eichensehr2020, p. 553). Eichensehr also discusses what she calls “micro-level deterrence” against particular individuals who are deterred from future violations through indictment or the imposition of sanctions (Eichensehr, Reference Eichensehr2020, pp. 554–555). Certainly, the potential for deterrence is maximized through the use of international criminal law, which has the potential to contain far more stringent sanctions than simply “naming and shaming” – that is, simply publicly attributing the source of the cyberattack.
That said, as mentioned, the ICC cannot play a role in deterring cyberattacks unless actors (both state and nonstate actors) realize that certain cyberattacks, even if only a limited subset of them, could constitute Rome Statute (or other) crimes. In this respect, one welcome initiative is the convening of the “Council of Advisers on the Application of the Rome Statute to Cyberwarfare,” a group of expert participants convened by the Permanent Mission of Liechtenstein to the United Nations and co-organized by Argentina, Austria, Belgium, Costa Rica, the Czech Republic, Estonia, Luxembourg, Portugal, Spain, and Switzerland, as well as the Global Institute for the Prevention of Aggression (“Council of Advisers,” 2021). The goal of the group is to increase awareness of the potential for the Rome Statute to cover certain cyberattacks through its meetings and the eventual release of a report (see also Digital Watch discussing the Open Ended Working Group on Cybersecurity at the UN). (The author serves on the Council of Advisers.)
It is not claimed that this increased knowledge will fully deter cyberattacks that could be encompassed by the Rome Statute; in particular, one would expect less deterrence in situations where no ICC jurisdiction exists, and where one would not anticipate the Security Council referring a situation to the ICC (see the Rome Statute, 1998, Arts. 12(2)(a)–(b), 13(b), 15bis, 15ter on jurisdiction).Footnote 3 For example, it would be naïve to anticipate referral by the Security Council of a situation to the ICC (which is permitted, Rome Statute, 1998, Arts. 13(b), 15ter), if a permanent member of the Security Council is involved in a cyberattack. (The permanent members hold veto power over substantive Security Council votes, UN Charter, Art. 27(3)). Additionally, it might be difficult to deter informal or rogue bands of hackers who might remain unaware of any expert report on cyberattacks (or even the ICC’s existence), and perhaps would not be deterred regardless. An additional argument could be made that the ICC would have to become a more effective institution before it creates significant deterrence – for example, it has a significant number of outstanding arrest warrants (see ICC Warrant/Summonses, n.d.). Furthermore, that the ICC tends to focus its prosecutions on higher-level perpetrators further suggests that “ordinary hackers” would not necessarily fall within its focus absent an egregious cyberattack, and so decreases any deterrence potential to “ordinary hackers.” Yet, the ICC is not limited to prosecuting only those bearing the “greatest responsibility” for statutory crimes, as was, for example, the Special Court for Sierra Leone (Special Court Statute, Art. 1.1); thus, if a particularly egregious cyberattack were to occur, an “ordinary hacker” could potentially attract the ICC Prosecutor’s focus, including, potentially, all who aided and abetted the crime or who acted with the “common purpose” of committing the crime.Footnote 4 Notwithstanding, as mentioned, the initial first step in attempting to maximize deterrence – and thereby potentially contributing to the goal of achieving a state of cyber peace – is most certainly to create broader awareness of the ICC’s potential to prosecute a limited subset of cyberattacks.Footnote 5
The section below briefly considers two initial overarching considerations that restrict the cyberattacks the ICC might be able to prosecute. The following section provides a brief overview of how certain cyberattacks could fall within the Rome Statute’s substantive crimes – war crimes, crimes against humanity, genocide, and the crime of aggression. A more expansive discussion of both topics can be found in my forthcoming article “The Criminalization of Cyberattacks under the International Criminal Court’s Rome Statute” (Trahan, forthcoming) and the upcoming Report of the Council of Advisers on the Application of the Rome Statute to Cyber Warfare (forthcoming).
4 Overarching Considerations as to ICC Prosecutions
Some of the limiting factors in terms of prosecuting cyberattacks before the ICC include (1) the Rome Statute’s “gravity” threshold and (2) the need to prove attribution through admissible evidence that could satisfy the standard of proof beyond a reasonable doubt. While they are beyond the scope of the present chapter, additional limiting factors include the need to satisfy jurisdiction; the ICC’s “intent” requirement (which excludes responsibility for unforeseen consequences and severely restricts it even as to foreseeable consequences);Footnote 6 and the prohibition in the Rome Statute on expanding definitions of crimes by analogy, with ambiguity construed to favor the defense (Rome Statute, 1998, Art. 22(2)). (For a discussion of all three topics, see Trahan, forthcoming.)
5 The ICC’s Gravity Threshold
For a case to be “admissible” before the ICC, Article 17 of the Rome Statute requires that it be of “sufficiently gravity to justify … action by the Court” (Rome Statute, 1998, Art. 17(1)(d)). Article 53 further states that the Prosecutor may only initiate an investigation or proceed with a case if it “would be admissible under Article 17” (Rome Statute, 1998, Arts. 53(1)(b), 53(2)(b)). These provisions raise the question of which cyberattacks would be considered more grave and which less grave, or of marginal gravity. The ICC’s cases to date have focused on rather large-scale crime scenes, with the “smaller” crime scenes probably being the killing of twelve peacekeepers, at issue in the Abu Garda case (see Whiting, Reference Whiting2015),Footnote 7 and the destruction of nine mausoleums and one mosque at issue in the Al Mahdi case (Prosecutor v. Al Mahdi, Case Information Sheet, 2018). Both cases involved the killing of persons or the destruction of physical objects.Footnote 8
In terms of evaluating the gravity of cyberattacks, a useful starting point for analysis is Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations (Tallinn 2.0). Admittedly, there are divergent views among states and experts as to the weight to accord the Tallinn Manual (Efrony & Shany, Reference Efrony and Shany2018), and in any event they are not binding on the ICC, yet they can at least provide a useful starting point.
In Tallinn 2.0, the experts focused on what constitutes an “armed attack” committed through cyber means. They engaged in this analysis because an “armed attack” can justify self-defense under Article 51 of the UN Charter (see UN Charter, Art. 51); they were not engaging in this analysis in relationship to the ICC. Tallinn 2.0 takes the position that “a cyber operation that seriously injures or kills a number of persons or that causes significant damage to, or destruction of, property would satisfy the scale and effects requirement” and thus constitute an “armed attack” (Schmitt, Reference Schmitt2017, Rule 71, para. 8.) This would provide one possible standard by which to evaluate the gravity of cyberattacks. Namely, only if a cyberattack seriously injures or kills a number of persons or causes significant damage to, or destruction of, property, would that satisfy Rome Statute gravity.
The experts additionally suggested various criteria that “States are likely to consider” as to when a cyber operation constitutes a “use of force” (relevant to considering when Article 2(4) of the UN Charter is violated, see UN Charter, Art. 2(4)). These criteria included severity, immediacy, directness, invasiveness, and measurability of effects (Schmitt, Reference Schmitt2017, Rule 69, para. 9 (a)–(e)). These would appear useful criteria to consider in making the gravity evaluation. Additional factors that could prove useful for consideration include those identified in ICC case law (see, e.g., Prosecutor v. Al Hassan, 2020, paras. 59, 89, 90) and by the Prosecutor (see “Policy Paper on Preliminary Examinations,” 2013, paras. 62, 64–65).
Another interesting consideration is whether loss of life or physical destruction is always the most grave of harms? For instance, France takes the position that operations that penetrate military systems to weaken French defensive capabilities, even if this does not produce physical effects, would constitute a “use of force” (Droit International, 2019, as cited in Schmitt, Reference Schmitt2019).Footnote 9 Similarly, the Netherlands takes the view that a catastrophic systems attack that causes very serious economic impact could constitute an “armed attack” (Schmitt, Reference Schmitt2019, quoting the Dutch Minister of Defence). While neither country is opining on whether such conduct would meet Rome Statute gravity, it is worth considering whether it should do so. The author suggests that here one might differentiate between penetration of military systems and catastrophic systems attacks that cause serious injuries or fatalities to persons, or significant damage to or destruction of property, from those that do not. Another interesting question is whether the destruction of “data” should be encompassed, or whether the “property” destroyed would need to be physical property (see, e.g., Biller and Schmitt, Reference Schmitt2019; Mačák, Reference Mačák2015; Horowitz, Reference Horowitz2020, considering destruction of data).
The ICC might wish to examine these issues and consider issuing a policy paper on application of the Rome Statute to cyberattacks (including the topic of gravity). At the same time, in terms of increasing deterrence potential, there could also be some advantages flowing from ambiguity. Thus, this author suggests that one possible gravity threshold for ICC prosecution could be where a cyberattack causes serious injuries or fatalities to persons or significant damage to or destruction of property; at the same time, perhaps one would not want to close the door to other large-scale or invasive attacks that do not meet this definition. Also, as the ICC Appeals Chamber explains in the Al Hassan case, the gravity requirement does not “oblige the Court to choose only the most serious cases, but merely [obliges] it not to prosecute cases of marginal gravity” (Prosecutor v. Al Hassan, 2020, para. 59).
The ICC’s pursuing of a case where a cyberattack of sufficient gravity occurs would be significant in itself, and make clear that the Rome Statute does encompass cyberattacks. Roscini writes: “the Prosecutor might decide to select certain situations and cases involving the commission, instigation, or facilitation of international crimes through cyber conduct because of their impact or to deter them in the future, even if they resulted in a lower number of victims than in other cases” (Roscini, Reference Roscini2019, p. 271).Footnote 10 This “expressivist” approach – pursuing prosecutions that further protected values and thereby sending a message to achieve a given result – is indeed an important and legitimate aspect of prosecutorial strategy (Cross, Reference Cross2020, pp. 67–68).
6 Proving Attribution through Admissible Evidence that Establishes Proof Beyond a Reasonable Doubt
An additional limiting factor – true for all ICC crimes – would be that all the elements of the crime would need to be proven through admissible evidence that could eventually satisfy the requirement at trial of proof beyond a reasonable doubt (Rome Statute, 1998, Art. 66(3)). This includes the issue of attribution (who conducted the cyberattack), sourcing it not just to a state (or nonstate actor/hacker group working for the state) but potentially to a particular “computer, … to identify the person who operated the computer, and more importantly to identify the real ‘mastermind’ behind the attack ….” (Tsagourias, Reference Tsagourias2012, p. 233). This could pose significant challenges (Dederer & Singer, Reference Dederer and Singer2019, p. 438 (citing sources)).
Compounding difficulties, cyberattackers sometimes go to lengths to conceal cyber operations (Hathaway et al., Reference Hathaway, Crootof, Levitz, Nix, Nowlan, Perdue and Speigel2012, p. 843), and states sometimes deliberately hide their attack as perpetrated by another state (“false-flagging”). For example, this happened when “Russian hackers piggy-backed on an Iranian cyber-espionage operation,” thereby hacking into “government and industry organizations in dozens of countries while masquerading as attackers from the Islamic Republic [of Iran]” (Stubbs & Bing, Reference Stubbs and Bing2019). Or states can hide behind nonstate actors to mask their operations (Dederer & Singer, Reference Dederer and Singer2019, p. 438; Hathaway et al., Reference Hathaway, Crootof, Levitz, Nix, Nowlan, Perdue and Speigel2012, p. 854). Even when that is not the case, because cyberattacks can be perpetrated through a single computer or network of computers located far from where the consequences impact, they can be extremely difficult to attribute (Dederer & Singer, Reference Dederer and Singer2019, p. 431; Brenner, Reference Brenner2011, p. 32). The attacks can also be concealed by feigning that operating systems are functioning normally (Rowe, Reference Rowe2007; Hathaway et al., Reference Hathaway, Crootof, Levitz, Nix, Nowlan, Perdue and Speigel2012, p. 828).
Furthermore, if attribution is to be made, this raises questions as to who would be in a position to do so. Would this be practical for the ICC to do itself? And, if not, what are the implications of relying on state cooperation in this regard? In addition to attribution, all of the evidence in the case would require “authentication,” and this (and simply having the knowledge to assemble a cyberattack case) would require significant technical expertise. Relying on state cooperation also carries pitfalls in that states may be more likely to cooperate when it suits their self-interests (e.g., they have suffered from a cyberattack), and not cooperate when it does not serve their interests (e.g., they were the perpetrator or linked to the perpetrator). Thus, there will be significant challenges in terms of attribution, authentication, and development of the necessary expertise to establish both. Building ICC expertise will require both the hiring of staff, and/or use of outside experts, and development of relevant policies.
Thus, the above discussion suggests the potential applicability of the Rome Statute to a limited subset of cyberattacks: (1) if they meet the Rome Statute’s gravity threshold and (2) where attribution could be proven beyond a reasonable doubt. As mentioned, other limiting factors include whether jurisdiction exists; whether the “intent requirement” can be proven (which appears to exclude responsibility for unforeseen consequences and limit responsibility even for foreseen consequences);Footnote 11 and whether the crimes can be applied without drawing on analogies, with ambiguity construed to favor the defense (Trahan, forthcoming).
7 The Rome Statute’s Substantive Crimes
Despite the limitations suggested above, the next section outlines the key elements of the Rome Statute’s four core crimes – genocide, war crimes, crimes against humanity, and the crime of aggression – and suggests how a limited subset of cyberattacks might fall within the definitions of each.Footnote 12 Again, domestic jurisdictions, even ones that incorporate these crimes into their domestic criminal codes, could adopt broader definitions of the crimes; thus, the elements of the crimes discussed below would not necessarily apply in domestic jurisdictions, which also might have or develop broader criminal statutes covering cyberattacks and/or cybercrimes.
8 Cyberattacks as War Crimes under the Rome Statute
As mentioned, the rules of international humanitarian law apply in the cyber domain (Schmitt, Reference Schmitt2017, Rule 80; “The Paris Call,” 2018). Thus, for example, Tallinn 2.0 explains that in a state of armed conflict, cyberattacks may not target civilians (Schmitt, Reference Schmitt2017, Rule 80), may not be indiscriminate (Schmitt, Reference Schmitt2017, Rule 105), and may not cause excessive “collateral damage” (Schmitt, Reference Schmitt2017, Rule 113). Tallinn 2.0 expressly acknowledges that when such IHL rules are violated, “[c]yber operations may amount to war crimes and thus give rise to individual criminal responsibility under international law” (Schmitt, Reference Schmitt2017, Rule 84).
Under the Rome Statute, “[the] Court shall have jurisdiction in respect of war crimes in particular when committed as a part of a plan or policy or as part of a large-scale commission of such crimes” (Rome Statute, 1998, Art. 8(1)). Additionally, all of the contextual elements for war crimes would need to be proven – such as the existence of an “armed conflict” (whether international or noninternational), a “nexus” between the cyberattack and the armed conflict (ICC, “Elements of Crimes,” 2011), and that the perpetrator was aware of the factual circumstances that established the existence of the armed conflict (ICC, “Elements of Crimes,” 2011). There would also be the elements for the specific underlying war crime(s), as well as – as explained above – the need to prove attribution (linking a specific perpetrator), intent, and jurisdiction. As to specific war crimes, note that the Rome Statute contains different lists of war crimes depending on whether the crimes were committed during international armed conflict or noninternational armed conflict (compare Rome Statute, 1998, Art. 8.2(a)–(b) with Art. 8.2(c), (e)).
As to the requirement of armed conflict, under the generally accepted definition from the ICTY’s Tadić case, “an armed conflict exists whenever there is a resort to armed force between States or protracted armed violence between governmental authorities and organized armed groups or between such groups within a State” (Prosecutor v. Tadić, 1995, para. 70). The Rome Statute (and IHL) particularly exclude “situations of internal disturbances and tensions, such as riots, isolated and sporadic acts of violence or other acts of a similar nature” (Rome Statute, 1998, Art. 8(2)(d)). An international armed conflict is one in which two or more states are parties to the conflict (Rona, Reference Rona2003, p. 58; Common Article 2 to the 1949 Geneva Conventions). Noninternational armed conflict is defined as “armed conflict not of an international character” (Common Article 3 to the 1949 Geneva Conventions). For noninternational armed conflict, the operations must also have reached a minimum level of intensity and a nonstate armed group must have achieved a certain level of organization (Prosecutor v. Tadić, 1995, para. 70).Footnote 13
The cyberattacks on Eastern Ukraine provide a possible example of war crimes perpetrated using, at least partly, cyberattacks. The attacks there were “blended attacks,” perpetrated through cyber and physical/kinetic means. In addition to the armed conflict that killed more than 10,000, the hacking into dozens of governmental organizations and companies through a “scorched-earth” cyberattack, which penetrated victims ranging from media outlets to railway firms and hospitals, caused hundreds of thousands of homes to lose electricity and shut down at least three regional utilities (Greenberg, Reference Greenberg2018; Bezhan, Reference Bezhan2016; Efrony & Shany, Reference Efrony and Shany2018, pp. 624–626). Both the United States and the United Kingdom believe that the cyberattacks on Ukraine were perpetrated by Russia’s military intelligence service, commonly known by the Russian acronym GRU (Warrell et al., Reference Warrell, Seddon and Manson2020).
The cyberattack, conducted during a state of armed conflict could, if all the elements of the crimes were able to be proved through admissible evidence, potentially constitute the war crime of intentionally directing attacks against the civilian population (Rome Statute, 1998, Art. 8(2)(b)(i)), or civilian objects (Rome Statute, 1998, Art. 8(2)(b)(ii)),Footnote 14 or inflicting “collateral damage” – incidental loss of life or injury to civilians that is “clearly excessive in relationship to the concrete and direct overall military advantage anticipated” (Rome Statute, 1998, Art. 8(2)(b)(iv)).Footnote 15 The cyber operations also appear to have been “indiscriminate.”Footnote 16 A cyberattack against a medical facility – of which there were several in Eastern Ukraine (Greenberg, Reference Greenberg2018) – could also constitute a war crime under Rome Statute Articles 8(2)(b) (xxiv) and (e)(ii) (Mačák et al., Reference Mačák, Gisel and Rodenhäuser2020). As with all ICC crimes, one would, among other things, additionally need to attribute responsibility to particular individuals for an ICC case to proceed and satisfy the intent requirement, both of which could prove difficult. There is ICC jurisdiction over the events in Ukraine because Ukraine executed an Article 12(3) declaration, accepting the ICC’s jurisdiction over crimes committed on its territory from November 21, 2013 to February 22, 2014, and then executed another such declaration covering crimes committed from February 22, 2014 and continuing on an open ended basis. (ICC Investigation, Ukraine, n.d.). Thus, there currently is ICC jurisdiction over cyberattacks that have been and are being committed in Ukraine, as well as jurisdiction over war crimes, crimes against humanity, and genocide more generally.
9 Cyberattacks as Crimes Against Humanity under the Rome Statute
Crimes against humanity are defined in the Rome Statute as acts “committed as part of a widespread or systematic attack directed against any civilian population, with knowledge of the attack” (Rome Statute, 1998, Art. 7(1)). The “attack” against the civilian population is defined as “a course of conduct involving the multiple commission of acts [enumerated in Article 7(1)] against any civilian population, pursuant to or in furtherance of a State or organizational policy to commit such attack” (Rome Statute, 1998, Art. 7(2)(a)).Footnote 17 For crimes against humanity, the attack is directed against a civilian population and need not be a military attack or linked to armed conflict (see, e.g., Prosecutor v. Ntaganda, 2019, para. 662). There are also requirements that the perpetrator’s “conduct was committed as part of a widespread or systematic attack directed against a civilian population” (the “nexus” requirement) and that “[t]he perpetrator knew that the conduct was part of or intended the conduct to be part of a widespread or systematic attack directed against a civilian population” (ICC, “Elements of Crimes,” 2011). The “underlying crimes” that support a charge (or multiple charges) of crimes against humanity are murder, extermination, enslavement, deportation, imprisonment, torture, rape or sexual violence, persecution, enforced disappearances, apartheid, and other inhumane acts (see Rome Statute, 1998, Art. 7(1)(a)–(k) for details).
Let us assume a “cyber-9/11” scenario, where the attackers have used cyber means to jam the controls of several airplanes, causing them to crash into buildings with ensuing large-scale loss of life. That would likely constitute the crime against humanity of murder if evidence proves that the attack was “widespread” (e.g., impacting a large number of victims) or “systematic” (a coordinated, organized attack) and orchestrated through a “State or organizational policy” (proof of which may be inferred, Prosecutor v. Bemba, 2016, para. 160), and one can attribute responsibility to particular perpetrators, prove intent, and satisfy jurisdictional requirements. The same cyberattack, if directed toward members of a particular protected group, could additionally constitute the crime against humanity of persecution (see Rome Statute, 1998, Art. 7(1)(h), listing protected groups). Crimes against humanity also include a residual “catch-all” – namely, “[o]ther inhumane acts of a similar character [to other crimes against humanity] intentionally causing great suffering, or serious injury to body or to mental or physical health” (Rome Statute, 1998, Art. 7(1)(k). Cyberattacks with severe consequences, such as a cyber 9/11, could also fall within this category.
While there appears to be great interest and concern about the problem of cyberattacks disrupting elections, to this author such interference – which could certainly be “widespread” and “systematic” (although it need not be both) – does not rise to the level of “other inhumane acts” because it would not involve “great suffering, or serious injury to body or to mental or physical health.” It also does not appear to fit into any of the other “underlying crimes” of crimes against humanity (see Rome Statute, 1998, Art. 7(1)(a)–(k)).Footnote 18
10 Cyberattacks as Genocide under the Rome Statute
Genocide is a crime that targets members of a distinct “national, ethnical, racial or religious group” (Rome Statute, 1998, Art. 6). For this crime, it is not the attack itself, but the intent behind the attack that is key. The dolus specialis (special mental state requirement) of genocide requires proof of: (1) “intent to destroy”; (2) “in whole or in part”; (3) of a “national ethnical, racial or religious group”; and (4) “as such” (i.e., because individuals belong to such a group) (ibid.; Kreβ, Reference Kreβ2006, p. 498). While genocide includes “inchoate” forms – for example, incitement to commit genocide could be the completed crime (Rome Statute, 1998, Art. 25(3)(e); Ohlin, Reference Ohlin2009, discussing “inchoate crimes”) – for Rome Statute purposes, if no genocide occurs the crimes probably would not satisfy ICC gravity requirements.
In addition to these overall requirements, there must be “underlying crimes”; the first enumerated being the killing of members of a group (Rome Statute, 1998, Art. 6(a)). The second underlying crime is “[c]ausing serious bodily or mental harm to members of the group” (Rome Statute, 1998, Art. 6(b)). The third underlying crime is “[d]eliberately inflicting on the group conditions of life calculated to bring about its physical destruction in whole or in part” (Rome Statute, 1998, Art. 6(c)) – see also Arts. 6(d)–(e)). Again, all are subject to Rome Statute gravity requirements, as one can also imagine a “mental” harm caused by a cyberattack that does not rise to the level of Rome Statute gravity, or creating horrible conditions of life for members of a protected group that is not necessarily aimed at bringing about the group’s physical destruction, and/or does not meet Rome Statute gravity. Thus, for a cyberattack to constitute the crime of genocide, it would need to satisfy both this overall special mental state requirement and proof of at least one of the underlying crimes. Additionally, as with all Rome Statute crimes, proof of attribution to particular individuals, proof of intent, and jurisdiction are required.
Here, it may be easier to envision cyber enabled genocide. In Rwanda, in 1994, Radio Télévision Libre des Mille Collines (RTLM) was used to incite and facilitate the killing of members of the Tutsi ethnic group – with the Tutsi identified by their government – issued identity cards, particularly at roadblocks (Metzi, Reference Metzi1997). One can similarly imagine cyber means used to compromise hospital or other medical records to identify members of a protected group, and/or; cyber means being used to incite genocide against protected group members (see, e.g., Mozur, Reference Mozur2018, discussing Burmese military Facebook incitement, coupled with crimes against the Rohingya). In either situation, assume the identification of protected group members and/or incitement is followed by killings (as it was in Rwanda and Myanmar), and one could infer the required genocidal intent (see, e.g., Prosecutor v. Akayesu, 1998); Burmese Military Document entitled “Rohingya Extermination Plan,” Mansour, Reference Mansour2017). Either could satisfy the elements of genocide.Footnote 19 Roscini also provides the example of a cyberattack that shuts down the cooling system of a nuclear power reactor releasing high levels of radiation killing members of a particular national group, if one could prove genocidal intent (Roscini, Reference Roscini2019, p. 250).
11 Cyberattacks as the Crime of Aggression under the Rome Statute
While the crime of aggression has numerous requirements and warrants a far more extensive discussion (see Trahan, forthcoming), some of the key requirements are that there is a state “act of aggression” (Rome Statute, 1998, Art. 8bis, para. 2) that, to qualify as the crime of aggression, must also constitute a “manifest” violationFootnote 20 of the UN Charter by its “character, gravity and scale” (Rome Statute, 1998, Art. 8bis, para. 1). The “act of aggression” is defined as “use of armed force by a State against the sovereignty, territorial integrity or political independence of another State, or in any other manner inconsistent with the Charter of the United Nations”Footnote 21 (Rome Statute, 1998, Art. 8bis, para. 2). There is also a list of acts enumerated in Rome Statute Article 8bis, paragraph 2 (a)–(g) that could meet that requirement, but each would additionally need to constitute a “manifest” violation of the UN Charter (Rome Statute, 1998, Art. 8bis, para. 2 (a)–(g)).Footnote 22 Another requirement is that the crime only covers “leaders” in that it applies only to “person[s] in a position effectively to exercise control over or to direct the political or military actions of a State”Footnote 23 (Rome Statute, 1998, Art. 8bis, para. 1). Also, the leader would need to engage in the “planning, preparation, initiation or execution” of the crime (Rome Statute, 1998, Art. 8bis, para. 1).
While the above requirements appear difficult to satisfy, the fourth act enumerated as potentially qualifying as an “act of aggression” is “[a]n attack by the armed forces of a State on the land, sea or air forces, or marine and air fleets of another State” (Rome Statute, 1998, Art. 8bis, para. 2(d)) and Article 8bis refers to “the use of any weapon by a State against the territory of another State” (Rome Statute, 1998, Art. 8bis, para. 2(b) (emphasis added)). Imagine a cyber unit within the armed forces of a state causes weapon systems of the armed forces of another state to become completely inoperable.Footnote 24 That would constitute an “attack by the armed forces of a State” on the forces of another state. One would additionally need to attribute responsibility to a particular state leader (or head of cyber command) of the attacking armed forces who is “in a position effectively to exercise control over or to direct the political or military actions of a State,” and who planned, prepared, initiated, or played a role in the execution of the cyberattack. Changing the scenario slightly, imagine the leader or head of cyber command instead employs bands of nonstate hackers to conduct the same attack and later acknowledges those acts as acts of the state. Here one would look to the rules on state attribution to determine whether the acts of the nonstate actors become attributable to the state, with perhaps the clearest situation being where the hackers are hired into the state cyber command structure, so they become part of the armed forces.Footnote 25 In any event, the cyberattack would need to be “manifest,” such that it is not de minimis (insufficient in gravity and/or scale) and/or “super clear” in terms of its illegality (meeting the required “character”). Yet, because of seemingly extensive jurisdictional limitations – if they are valid (see Trahan, Reference Trahan2018) – it could be quite difficult to trigger ICC jurisdiction regarding the crime of aggression, absent a UN Security Council referral.Footnote 26
Returning to the example of election interference, this author doubts that the elements of the crime of aggression would be satisfied. While election interference could be viewed as a “sovereignty violation” (Shackelford, Reference Shackelford2017, 11; Efrony & Shany, Reference Efrony and Shany2018, 640), this author does not see it rising to the level of a “manifest” Charter violation, which is required for the crime of aggression (Rome Statute, 1998, Art. 8bis, para. 1). Furthermore, at least one significant state involved in election interference, the Russian Federation (Ohlin, Reference Ohlin2020), is not a party to the Rome Statute, so there would be no ICC jurisdiction over the crime of aggression committed by Russian nationals (ibid., Art. 15bis, para. 5).Footnote 27
12 Conclusion
This chapter has briefly touched on what will need to be a far more extensive study considering how the crimes in the ICC’s Rome Statute could potentially encompass certain cyberattacks. Yet, hopefully, this chapter has made the case that there is at least some potential for applicability. My forthcoming article and the forthcoming report of the Council of Advisers on the Application of the Rome Statute to Cyberwarfare will expand significantly on these topics.
It is important to engage in this analysis, as there would need to be broad recognition of the ICC’s ability to prosecute certain cyberattacks if there is to be any potential for deterrence. Only then can international criminal law in this area play a role in maximizing the potential of reaching a state of cyber peace. It is actually quite significant that there is an existing international criminal tribunal with jurisdiction to prosecute a limited subset of cyberattacks. This capacity was probably never envisioned when the Rome Statute was negotiated; yet, certain cyberattacks appear to meet the elements of the ICC crimes. Whether it is feasible to bring cases will depend if attribution can also be established, and if all of the elements of the crime can be proven through admissible evidence that satisfies the standard, at trial, of proof beyond a reasonable doubt. Perhaps this is not fully feasible now, but as technology develops, it could become more achievable in the future.
None of the cyberattacks perpetrated to date probably have reached the threshold for Rome Statute crimes with the possible exception of those in Ukraine, over which the ICC has an open preliminary examination (ICC, “Preliminary Examination, Ukraine,” n.d.). It may also take time for the ICC to develop the required expertise to be able to develop and prosecute such cases, and the ICC may need to rely extensively on the outside expertise of cyber experts. Yet, as mentioned, that also carries potential pitfalls. To the extent the ICC can develop its own internal capacity that could help alleviate potential conflicts of interest.
International criminal law does have a role to play here. Will this deter all cyberattackers from committing grievous cyberattacks? The author will not be so naïve to claim that it will. But if the ICC is able to achieve some deterrence – deterring even one horrific cyberattack – that would certainly be a worthwhile endeavor. Ironically, it will be hard to know if such an attack has been deterred, because it would involve the absence of the attack, something notoriously difficult to prove.
While ICC States Parties may be “willing” and “able” to prosecute cyberattacks, and under Article 17 of the Rome Statute, that would then render a case “inadmissible” before the ICC (see Rome Statute, 1998, Art. 17), it is also quite possible that domestic jurisdictions will lack the required laws and/or be unable to exercise jurisdiction over the totality of the crime (which potentially might involve a foreign attacker state and multiple “victim” states). Then, the domestic jurisdiction would be “unable” to prosecute the case fully, likely rendering the case “admissible” before the ICC if other Rome Statute requirements are also satisfied.
To date, most of the ICC’s focus has been on crimes in developing countries. Because both developed and developing countries suffer from cyberattacks (probably developed countries even more so), a focus on such crimes before the ICC could be a welcome development, at least in the eyes of many ICC States Parties. Promoting the applicability of the Rome Statute to certain cyberattacks could additionally demonstrate an increased relevance of the ICC to one of the more vexing contemporaneous challenges facing the international community.
“Trust but verify.” Students of history and readers of a certain age will recall those words being spoken by former US President Ronald Reagan. His argument was that peace required verification mechanisms so that each side could be confident in the actions of the other side. There are important lessons for cyber peace. While Reagan was speaking in the context of strategic nuclear arms control, many papers have been devoted to the difficulties of arms control in the cyber domain (Maybaum and Tölle, Reference Maybaum and Tölle2016). Cyber weapons do not require the large physical infrastructure of nuclear programs and can far too easily be kept secret to allow for meaningful validation of adherence to arms control commitments. Moreover, many “cyber weapons” are dual use in nature, being deployed for the administration of computers and networks, or for security testing. Yet, as we discuss in this chapter, arms control is only one area in which verification is an important tool for maintaining international peace in cyberspace and other domains.
This chapter starts with a discussion of the role played by verifiers in peace. We discuss some of the many types of verifiers, and how those whose roles are outside the formal political process can help to construct peace. Many of these have scientific or investigatory roles whose work informs the state of the world. There are interesting models in aviation, including not only the National Transportation Safety Board (NTSB) but also a variety of others including institutions dedicated to telemetry analysis and near miss analysis. We examine each and suggest how a cyber equivalent could contribute to our understanding of the state of the world and in doing so, support peace.
1 The Need for Verifiers in Cyberspace
A state of peace is a social construction. Peace exists because all parties act as if it exists, but it can be broken or threatened by the actions of any party. As long as peace and a belief in peace exists, it acts as an inhibitor to the initiation of violence, because peace is worth preserving. Parties inhibit their activities to maintain peace (or they act to break it). We take these ideas as axiomatic to allow us to investigate the idea of diverse verifiers and investigate several categories of verifiers whose existence would support the construction of peace. Both the construction and effects of peace have many aspects that are explored elsewhere in this volume, particularly in Chapters 1–3.
War and peace are frequently paired with terms of probability, duration, and time: An impending war, an uneasy truce, a stable peace. If people are uncertain about the existence of peace, if they are uneasy about it, then their willingness to make threats, to plan to carry out threats, and to impose their will on others will be higher. If societies are worried about a lack of peace they will invest in security. Building walls and forts takes substantial resources and takes those resources away from other possible investments. They will invest in arming, training, and maintaining military forces. In times of peace, those investments are reduced. The frames assigned to such things (the “peace dividend,” “to maintain peace, prepare for war,” and the like) are usually normative and closely relate to the speaker’s belief in the stability and longevity of peace. A more widely shared belief that the world is at peace and that peace is stable will free resources for nondefense spending. To the extent that such a belief is accurate and well founded, those other areas of spending will reflect the desires (rather than the fears) of the public. Wide sharing of a belief in peace will be enhanced if many groups with different perceived motives are reporting similar things. Contrariwise, if some sources are reporting signs of war and others are not, there will be disagreement over spending.
A cyber peace dividend might consist of several components, including reduced corporate investment, reduced national investment, and reduced cost to the general public. Today, a widely cited rule of thumb is that commercial entities spend about 8 percent of IT budgets on security (Nash, Reference Nash2019). Not all of that could be reclaimed by a cyber peace dividend. National investments by governments include both attack and defense. The former is easier to unilaterally reduce. We note, in passing, that the offense budgets are often “black budgets” and hard for outsiders to understand. The cost to the public is a mix of anxiety and the inhibition of productive work because security is hard.
In 2020, there is extreme distrust both across and between societies. The Trump administration announced that the United States would withdraw from the World Health Organization (WHO), a move that the Biden administration reversed. The United Kingdom has withdrawn from the European Union. Many people are refusing to wear masks, refusing to believe in climate change, the list goes on. Attacks on the credibility of news organizations (“it’s fake news”) augment and bolster other attacks on credibility. In order to overcome this distrust, the world would be better with a series of neutral, trustworthy, and trusted institutions that are less subject to political or market forces and must adhere to strict protocols for verifying the claims of actors in cyberspace. “Governments and diplomats,” as Roger Hurwitz (Reference Hurwitz2012) notes, “… have been less clear in recognizing how foundational public trust is for cyberspace.” Similarly, Elinor Ostrom has commented that “trust is the most important resource” (ESCOTET Foundation, 2010). In that spirit, diverse verifiers are the soil in which trust grows.
We look for inspiration to aviation. Among the reasons to look to aviation is that while aviation is inherently risky, deeply technical, and still relatively new, it has evolved into a set of trusted and trustworthy institutions. In addition, other research projects we have done over the last few years have familiarized us with the institutions there, and on consideration they seem to be perhaps both interesting and inspirational.
2 Building Off of the Aviation Model
In other contexts, international mechanisms exist to investigate claims of activity that violate international agreements or norms of behavior. Interpol and the International Criminal Court both investigate allegations of war crimes and human rights violations. The International Atomic Energy Agency (IAEA) investigates violations of the nonproliferation treaty. Given the limitations we note above on applying the arms control model to cyberspace, a better analogy than nuclear site inspections may be international civil aviation. In the domestic context, the authors have separately and collectively promoted the development of cyber incident investigations, modeled on the National Transportation Safety Board’s process for investigating aviation incidents and the processes for sharing “near misses” within the aviation community. In concert with the development of national mechanisms for investigating cyber incidents, the international community is also in need of international mechanisms to coordinate and referee international cyber incidents involving multiple states.
For international aviation incidents, the Convention on International Civil Aviation (1994) dictates that the jurisdiction of the crash site will have primary responsibility but allows that jurisdiction to cede authority to a different authority. Such arrangements are managed through the International Civil Aviation Organization (ICAO), the organization established by the convention. In the case of the Malaysian Airlines Flight 17, which was shot down by Russian-backed rebels over Ukraine on July 17, 2014, Ukraine delegated the Netherlands to conduct the investigation given that the flight originated in Amsterdam and had a large number of Dutch citizens onboard (Parker and Olearchyk, Reference Parker and Olearchyk2014). The decision may also have created the perception of improved capability and objectivity by bringing in a third country that was not embroiled in the ongoing conflict to conduct the investigation. In the case of Malaysian Airlines Flight 370, which disappeared over the Indian Ocean on March 8, 2014, Malaysia assembled a Joint Investigative Team of experts from Malaysia, China, the United Kingdom, and the United States, led by an independent investigator under ICAO standards.
In contrast, when international cyber incidents occur, investigations are conducted in an ad hoc manner, usually under the authority of the victim state or by private firms. The findings of such investigations are often the subject of political machinations by the victim company or organization who may wish to avoid negative market reactions for failing to prevent the incident; by the victim’s government, which may either seek to downplay or promote the narrative depending on the geopolitical concerns of the moment; and, of course, by the attacker or the attacker’s country. In the vast majority of cases, however, no investigative report is ever published. Incident response will be carried out for the purposes of containing an ongoing incident, recovering systems, and preventing future incidents at the victim company. Incident handlers are not, however, in the business of fact finding and reporting so that lessons can be learned and, thus, similar incidents being prevented at other companies.
Some incident handlers generate or contribute to a product labelled “threat intelligence.” These “feeds” are often commercial and include the attacker’s given names like “Dynamite Panda” (MITRE ATT&CK, 2020). Many times, these products include attribution information, such as “this group uses these tactics,” or “the Panda set of attackers are Chinese Government affiliated.” The quality of these products have not fared well under scrutiny (Bouwman et al., Reference Bouwman, Griffioen, Egbers, Doerr, Klievink and van Eeten2020).
On attributing an attack to a specific state, attribution is also typically carried out in ad hoc manner, as was discussed more fully in Chapter 7. Cybersecurity firms may choose to attribute the incidents they discover, or prevent the actions of specific states, if they see it in their commercial interest, or believe that they have a patriotic duty to do so. More often than not, however, cybersecurity firms will choose to avoid attributing activity to a specific nation state so as not to hurt their commercial prospects in that state, or to avoid becoming a target themselves of that state. When national governments make a claim attributing malicious cyber activity to an adversary state, those claims are typically rebuffed by the accused state and largely ignored by the international community.
3 Background: Historical Incident Investigations
In the United States, investigations of cyber intrusions are typically conducted by private, for-profit cybersecurity firms. In rare cases, when a significant incident occurs, the federal government will investigate and report out on the incident. When the incident involves a federal computing system, such as the incident at the Office of Personnel Management (OPM) in 2015, Congress may investigate. In other cases, Congress asks the Government Accountability Office (GAO) to investigate. These reports are often slow to be produced and can be highly political in nature. While they may provide lessons learned to the cybersecurity community, that is not their primary purpose. Instead, their goal is to assign blame, sometimes in a highly partisan fashion. In the case of the OPM data breach in 2014, the House Oversight and Government Report Committee issued a 241-page report on the incident titled “The OPM Data Breach: How the Government Jeopardized Our National Security for More than a Generation.” While the report provides a comprehensive review of the incident that is valuable from a historical context, its partisan tone undermines its legitimacy as an even-handed fact-finding effort. Its timing, two years after the incident and a month before a hotly contested presidential election, also led to questions about its motivation and purpose.
On the international front, as with the downing of Malaysian Airlines Flight 17 in the air domain, Ukraine has proven to be the focus of significant international conflict within the cyber domain due to the protracted conflict between Russian-backed separatists and the western Ukraine government. Offensive cyber operations that were conducted against electric sector targets caused widespread power outages on two occasions. Ukraine was also the target of the NotPetya malware attack. Given the global spread of NotPetya and international concern over attacks on critical infrastructure, this analysis will focus on the attacks on the power grid. In the first of those incidents (in December of 2015) offensive cyber operators took thirty substations and two power distribution centers offline. The Ukrainian government sought international assistance to investigate the matter. According to reporting by Wired Magazine (Greenberg, Reference Greenberg2017), the investigation into the incident was conducted by Ukrainian officials with the assistance of the US Federal Bureau of Investigations and the US Department of Homeland Security. At least two private sector experts were brought in to assist the investigation. They were Robert Lee, a former National Security Agency technical operator and CEO of the industrial control systems security firm Dragos, and Michael Assante, the former chief information security officer (CISO) for the North America Electric Reliability Corporation. Both Lee and Assante were also instructors at the private SANS Institute.
Following the investigation, Lee and Assante published a publicly available report, “Analysis of the Cyber Attack on the Ukrainian Power Grid” (2016), under the auspices of the SANS Institute and the Electricity Information Sharing and Analysis Center (E-ISAC). That report addressed one of the two main purposes for conducting such an investigation, relating to other security professionals what happened so that lessons could be learned to prevent other, similar incidents in the future. It did not, however, address attribution of the attack. The Ukraine government asserted that the attack was carried out by Russia, but no international body validated that claim and the Ukrainian government offered no proof to substantiate the claim. For its part, the US government has never publicly attributed the attack to Russia, but leaks to the media have substantiated the claim (Park et al., Reference Park, Summers and Walstrom2017).
While the 2015 attack could have been the launching point of an effort to investigate incidents at critical infrastructure and disseminate lessons learned, no such virtuous cycle of process development and ongoing improvement began. When the Ukrainian power grid was attacked a second time, in December of 2016, the incident garnered far less attention. A standout example of dissemination of findings following a cyber incident was the March 2019 breach of Norsk Hydro, a Norwegian aluminum maker. Norsk Hydro made the unprecedented decision to be fully transparent about the incident, hosting web conferences to disseminate findings to the security community. In this incident, Microsoft’s Detection and Response Team led the response and authored the main report on it (Briggs, Reference Briggs2019).Footnote 1
4 Investigating Domestic Incidents: The Need for a National Cybersecurity Board
When a major security incident happens, victims are strangely incented to lavish praise on the attackers. After all, there is little shame in being hacked by the pros – “how were we supposed to fight the Russians?” So, some attacks that were performed by criminals or even teenage hackers will be blamed on professionals. If the Acme Company blames the KGB, who is to contradict them? From where do we get our facts? This misattribution is not harmless. The act of blaming the Russians (the Israelis, the Chinese, and the North Koreans) undercuts our assurance of a state of peace.
An investigatory board could help provide those facts. Reports from the NTSB, for example, are seen as authoritative and trustworthy. An investigatory board that invested in gaining and maintaining a reputation for competence could be a substantial counterbalance to organizations spreading self-serving claims. For example, a cyber board could conduct an investigation and release a report that assessed the sophistication displayed by an attacker on a scale from “not sophisticated” to “exceptionally sophisticated.” It could assess the idea that an attack was carried out by a nation state or the reliability of a claim that it was a particular nation state.
As this is being drafted, the United States, United Kingdom, and Canada released a joint statement claiming that Russian Intelligence is trying to steal vaccine information (NCSC et al., 2020), but such statements are unusual. The process for releasing intelligence information is opaque. Is the absence of such an announcement the result of peace or a geopolitical decision by intelligence agencies to withhold information?Footnote 2 By credibly communicating facts, a cyber board could be a stabilizing force for peace.
4.1 Why Do We Not Already Have a Cyber NTSB?
This subsection starts with a brief summary of what the NTSB does, examines some of the objections to a cyber analog, continues with some of the ways those objections might be addressed, and ends with some practical, achievable steps to create a cyber version NTSB. The NTSB is best known for investigating accidents in aviation. Aviation is a regulated sector. For an airplane to exist (in the United States) requires permission from the FAA; taking off requires a qualified pilot at the controls before leaving an airfield. Each of these is a term of both law and art and, while exceptions exist, these many constraints also act as constraints on the NTSB. An accident is something that leads to the death or injury of someone on a plane, or meaningful damage to one, and these are usually prerequisites to, and provide scope for, an investigation.
The first call we know of for a cyber investigations board was in the 1991 National Research Council report, Computers at Risk. Yet no such board exists thirty years later, and the reason, we think, is primarily industry opposition.Footnote 3 The core of that opposition is concern. No one wants to have their actions judged with 20/20 hindsight. No one wants to have their innovation judged by those who’ve never operated a business or been responsible for a profit and loss account. And while such judgements may or may not be real, the perceived threat inhibits the creation of such a board. In contrast, the NTSB was created when accidents in aviation were frequent, and those accidents inhibited the growth of the sector. The aviation industry came together in support of an investigatory body. In contrast, the technology sector seems to be generally opposed. It may be that there is also support, for example, from the insurance industry, but such support has not caused a cyber version of the NTSB to come into existence.
The fear of being judged can be a real problem. An interesting quote from Roving Mars (Squyres, Reference Squyres2005 discusses the choice to launch the Mars Exploration Rovers (Spirit and Opportunity)). Before we reach this scene, there was one prelaunch review board after another, examining the engineering choices that had been made:
Chris Scolese, Ed’s deputy, was still in the room, and he explained what had happened. Chris is an engineer, and he has managed space flight projects. What Chris knew is that practically every spacecraft that’s ever flown has had some kind of weird problem that popped up once or twice during testing, never to be seen again. You have to take some risks in this business, and the risk we were taking with the transponder was lower in Chris’s judgement than the risks we’d already decided we were willing to take on launch day and landing day. Chris had told Ed that he thought we should fly, and Ed had accepted Chris’s advice. But it had been a tough call by both of them.
With 20/20 hindsight, Scolese’s decision was right, but imagine if the rocket had blown up. Was “you have to take some risks” and “the risks were lower with the transponder” really justifiable? The prospect of such questioning inhibits experimentation and risk-taking. Sometimes that inhibition is appropriate. We would all agree that it is important to have test systems that mirror the production system as closely as possible, and to test with those systems, right? Take a moment to think and see if you agree. Sometimes that inhibition is appropriate. That being said, progress requires innovation and experimentation, and blame and second-guessing inhibit such experimentation.
As it turns out, the real world is a strange and complex place. It turns out that companies like Facebook and Netflix have moved to a practice of rolling out changes slowly across subsets of their production systems. This practice is often derisively called “testing in production,” which was a shocking strategy when these companies first admitted to it (Mappic, Reference Mappic2011). If those trying it had been worried about an external review board, they might have been prevented from experimenting. Testing in production is now accepted practice; it is considered by some to be a leading approach.
Industry concerns about having their practices judged are strong and real, as is the regular reinvention of the idea. It may be that there are ways to square this circle.
4.2 Getting to a Cyber NTSB
To stand up to a cyber incidents investigation board, we must balance the real and perceived concerns with an understanding of the myriad benefits, which include the ability to learn from the misfortune of others and to support the construction of peace. A board does not have to investigate everything to be useful to the cause of peace. The NTSB’s role is strictly constrained to accidents involving transportation; thus, a cyber version could be created in a way that aids in peace while addressing corporate concerns.
For example, such a board could initially limit its investigations to breaches involving US Government computers and limit its investigation of more complex incidents to the government computer subset of those cross-entity incidents.Footnote 4 As the capability of the organization grows, and as processes mature, the scope could be expanded to other critical infrastructures or other organizations could be created for this purpose. Today, these might be investigated by the FBI, and the attackers might be the subject of surveillance or other operations by intelligence agencies. Each of these agencies has limited resources, and different goals. Managing the overlap of such investigations may carry some complexity. However, this is a reality of complex incidents. For example, the Air Force already imposes such complexity on itself. Accidents are investigated by both a Safety Investigation Board and an Accident Investigation Board, each with different goals (Air Combat Command, 2013).
Another key question area would be the ability of a board to compel participation by either or both an organization and specific staff. Obviously, the participation of the victim organization is important, but to what extent is it expected and reasonable? What about their staff? To what extent should an investigations board be able to compel participation from suppliers to that victim? Would Microsoft, Google, and Amazon need staff dedicated to answering the board when their products are involved in a breach? Would investigators be limited to “what’s in the manual” or can they delve into product design decisions?Footnote 5 Even with regard to the manual, it is not always obvious what section of a complex product’s technical documentation is relevant. The two volumes of the latest edition of “Windows Internals” (Yosifovich et al., Reference Yosifovich, Solomon and Ionescu2017) comprise 1,568 pages, and those are books. The more voluminous technical documentation is now largely online and updated frequently. What is a reasonable expectation of an operator of such systems? These questions are not insurmountable, but some versions of them need to be addressed to move proposals forward.
What about the participation of staff? Can that be compelled? What about the right against self-incrimination? As we write this, Uber’s former Chief Security Officer has just been charged with obstruction of justice. What are the expectations for staff of a breached organization in terms of participation in an investigation? Is it “answer three questions by email” or “be deposed for a day or more?” How are software development staff to be trained, and whose staff would receive training? For example, the Air Force delivers annual training to pilots on the various investigations that will happen after an accident.
4.3 What Could a Cyber NTSB Do for Peace?
Calls for a cyber investigations board have traditionally focused on learning and disseminating lessons from incidents. This is inherently useful in the creation and preservation of cyber peace because it makes future attacks more difficult. And there are many other ways in which a board could support the cause of peace, including the following:
Publishing lessons learned reports (as opposed to sharing them under NDAs)
Bring different goals to incident investigation
Investigating more/different cases than police or intelligence agencies
Provide attribution with different biases
Report on the state of the world
Provide international assistance
Support a construction of peace
The primary reason for previous calls for a cyber investigations board has been to find and distribute lessons. The incredible safety record of aviation is commonly attributed to these and other learning systems. An investigations board could establish consistency and credibility, and stand in complement to the information released by police and prosecutors. That information is focused on literally “making the case” for prosecution and conviction, rather than learning lessons or informing. Analysis that is designed to be objective could better support peace by informing debate about the state of the world. It could potentially do so in a larger set of cases if the investigators are not required to testify, be subjected to cross-examination, and perform other tasks in the judicial system. The cases that a board investigates might be quite different than the ones that the police investigate. (There would need to be a deconfliction/equites process to ensure that investigations did not accidentally cross paths with other investigations. That process, like all the others, requires training for the involved participants.)
A board could provide attribution information about cases with a different authority than either private or prosecutorial analysis. Such analysis might be read with less skepticism or read with different skepticism by different parties, providing information that either supports or undercuts the construction of peace through a better understanding of the state of the world.
In addition to information about specific attacks, additional high-quality information about the frequency and intensity of international attacks would illustrate the state of the world at a given time and add information about the actors who are violating the peace, increasing the likelihood that they would be either caughtFootnote 6 or meaningfully made to take the blame for their actions.
The NTSB provides help and assistance to air crash investigations around the world. It would not be unreasonable to expect that once a board had established itself and its competence, it could, when asked, help investigate “important incidents” outside of the federal government, including state and local governments, as well as, perhaps, private enterprises. This assistance to entities within national borders could raise the cost of attacks via exposure. International assistance could be an act of goodwill, bolstering peace.
Additionally, a stream of analytic reports that establish norms and expectations would inform industry’s position on the impact of investigations. While it is reasonable to think that more data would aid in the understanding of the state of the world as was described in Chapter 3, it is similarly reasonable to think that most industry benefits from peace and trade.
5 A System for Reporting Near Misses
The NTSB is the best known of a polycentric constellation of aviation safety programs which complement and overlap to make hurtling through the air at hundreds of miles per hour incredibly safe. There are others including the Aviation Safety Reporting System (ASRS) and the Aviation Safety Information Analysis and Sharing System (ASIAS). One of the authors (Shostack) has argued at length for a Cyber Security Reporting System (CSRS),Footnote 7 and we believe that such a system could also enhance and preserve peace (Bair et al., Reference Bair, Bellovin, Manley, Reid and Shostack2017). Before discussing near misses at some length, we will first briefly explain the ASIAS system, and some of the limits an ASIAS analog would face. This helps illustrate the value of an ASRS-like system.
5.1 ASIAS: Telemetry Analysis
The ASIAS program collects telemetry from aircraft in operations, analyzes it, and reports back to the operators. For example, if flights operated by one airline have substantially different wing flutter than those operated by other airlines from that same airfield, then that might be interesting for each airline to know. Our ability to compare telemetry is built on a scaffolding of similarities. Aircraft and their components are made by a small number of manufacturers. The operational systems are defined by flights of a limited number of types (general, cargo, and military) from one field to another. This leads to similarity between the telemetry each emits. Computer systems run a far more varied set of workloads. A mail server might run on Windows, Linux (Ubuntu, Debian, RedHat, etc.), FreeBSD, OpenBSD, or others (McKusick et al., Reference McKusick, Bostic, Karels and Quarterman1996). The mail software might be sendmail, postfix, qmail, or Exchange, or even Gmail or Hotmail, which are (reputedly) unique software. Each of these operating systems and mail packages logs differently. Similarly, there is diversity in each “stack” of software, and that software delivers diverse values.
Despite this diversity, aggregated analysis of attacks could produce useful information. For example, if logs of rejected emails were collected, then we could learn about spam campaigns. There is a difference between mail from northeastem.com going to northeastern.edu and it going to shostack.org. On first blush, the former is much more likely to be a targeted campaign, and the latter to indicate a broad spamming campaign. But if we gathered rejection data from many recipients about email domains, we could tell recipients about the unusual campaigns they receive. Unusual might be determined algorithmically based on those whose sending domains are unusual, and there are standard computer science techniques that would help determine what counts as unusual relative to each recipient.Footnote 8 The data sent back to participants could motivate their participation, and the agency performing the analysis could provide information about the state of conflict in the world and possibly between states and semi-state and nonstate actors.
5.2 ASRS: Near Miss Reporting
We believe we can develop broader, and perhaps less expected lessons, from a cyber version of ASRS. In aviation, if there is an incident, then anyone involved can submit a short, two-page form to the ASRS, operated by NASA.Footnote 9 An incident is anything short of an accident, which, again, is the death or injury of a person or damage to an aircraft. The reports go to NASA to isolate them from accidental disclosure to the regulators. (There are important additional protections in both law and agreements between NASA and the FAA.) NASA ingests the reports, analyzes them, and publishes data that are carefully anonymized.Footnote 10 NASA also sends back a receipt. The reporter can use that receipt to demonstrate “evidence of constructive engagement” in a disciplinary proceeding. This evidence is one of the factors that the FAA takes into account in its administrative law proceedings. This incentive, which might seem small, adds to each participant’s desire for a safe aviation system and is enough to motivate roughly 100,000 reports each year to the ASRS (ASRS, 2019).
5.3 Cyber Near Misses and What We Might Learn
Near miss reporting, both within and between organizations, is an important building block in safety programs in a great many industries. Similarly, many of these programs use blamelessness as a tool to demonstrate their prioritization of learning over retribution.
The nature of near misses in cybersecurity makes them easier to report and discuss, and that eases open doorways to understanding the state of the world. The sorts of things we might understand include (but are not limited to) attacks that progress too close to a meaningful target or attacks that gain the interest of investigators for their distinctiveness. In doing so, near-miss reporting makes more measurable what is commonplace and effective, such as phishing and the techniques in use. These are nominally reported on, but what’s almost working can be lost in the noise.
We can learn useful things about what works to protect, detect, and respond to problems by tracking which tools are reliably reported for each. Such analysis can be broad and helps us to better preserve peace by prioritizing effective defenses. For example, while the NIST CSF contains over 900 controls (Reciprocity Labs, 2019),Footnote 11 the Australian Signals Directorate recommended a “top 4,” now transformed into an “essential eight” (Coyne, Reference Coyne2017).Footnote 12 Even if we believe that the controls in each set are at different levels of abstraction, and thus each of the eight represents a dozen in the NIST set, there remains a massive difference in the control recommendations. Either one of these standards is missing crucial controls, or the other standard includes investments that do not do very much good.Footnote 13 Knowing what does not work can be an important step forward. Stopping ineffective investments makes room for new ones. So, both positive and negative reports can be useful. A mix allows for interesting science: Why does measure A work for some organizations but not others?
5.4 The Contribution of a CSRS to Cyber Peace
The first contribution of a CSRS to peace would be the ability to improve defenses or to reduce costs without reducing the quality of defenses. The former makes attacks harder, and the latter allows us to invest in other things. Today in cyber warfare, the attacker has tremendous advantages. Improving the effectiveness of defenses would shift the balance somewhat. Making attacks more difficult, more likely to be detected, or more attributable would shift the logic against launching attacks and thus contribute to peace.
The second contribution could be an assessment of attacker activity. If a CSRS-adjacent body had access to confidential descriptions of “tactics, techniques, and procedures,” then it could analyze near miss information to report on rates of attacks or attack intensity.Footnote 14 This would be a very different function than aviation’s ASRS, but streams of near miss information in cybersecurity could be leveraged for this. Such variation may cause problems for multinational companies reporting to local authorities.
6 An International Mechanism to Investigate and Attribute Cyber Incidents
Building off of the ICAO model, what is needed in the international context is a mechanism for requesting international support for investigating significant cyber incidents. These investigations would be carried out for a dual purpose. First, they would provide a standard process and rapid timeline for disseminating findings useful to cyber defenders. Second, they would provide a means for determining attribution and releasing such findings to the public, allowing other international bodies to censure or penalize the offending state. These findings could also serve as the basis for organizing coalitions of governments to sanction or otherwise condemn the actions of the offending state should international institutions fail to act.
At this stage, rather than funding a standalone organization to investigate international cyber incidents, a more modest approach would be to establish a concept of operations for how such investigations should take place and who should take part in them. As in the successful example of the 2015 Ukraine investigation, such investigations will need to rely heavily on private sector expertise. Particularly in the area of industrial control systems, expertise on the security and forensic methods for such systems is exceedingly rare. Thus, keeping experts with the knowledge to carry out these investigations on the sidelines while waiting for the phone to ring would not be practical. Instead, ad hoc teams should be formed at the behest of the victim state. These teams would be invited to investigate and issue initial findings in a rapid fashion, followed by a comprehensive final report issued by the international body sponsoring the effort.
Some of these functions might be picked up by a “Cyber Peace Corps,” as discussed elsewhere in this volume, including in the essays section. But such a group, with room for everyone, carries a different function and requires a different culture from an organization with strong leadership focus on producing investigative reports. A Peace Corp could be a feeder to such an investigative body, helping to respond to problems, preserving evidence, and bringing forward interesting cases.
On determining attribution, significant conclusions can typically be achieved by comparing the tradecraft of the attacker to other known historic incidents. This process has led ESET (2016) and Dragos (2017), among others, to conclude that the team behind the Ukraine attacks was the same team behind the attacks on the Democratic National Convention and other political targets in the lead up to the 2016 US presidential election. Thus, without the benefit of national intelligence capabilities, investigators should be able to make preliminary conclusions on attribution. Intelligence agencies could then provide their own findings to the team, agreeing to release some, all, or none of the evidence uncovered through intelligence collection to the public. This process would allow for sources and methods to largely be protected, while providing an independent verification mechanism of the claims.
Conclusion
In this chapter, we have argued that trusted verifiers are essential for cyber peace. By creating trusted national mechanisms for investigating cyber incidents, lessons learned can be shared with the wider community and confidence that problems that caused one incident can be corrected elsewhere before more such incidents occur. By creating trusted verifiers for near misses, all members of the cybersecurity community can provide telemetry to determine the current level of hostility in cyberspace. With a strong international mechanism for investigating significant cross border cybercrime, determining lessons learned, and attributing malicious activity, more consequences can be created for states that engage in such activity. As norms of conduct in cyberspace are developed, it is essential that verifiers are enabled at multiple levels to ensure that they are being upheld, and when they are not to verify that claims of malfeasance are proved true and taken seriously. Trust but verify is, now more than ever, essential to the preservation of peace.Footnote 15
Since President Macron’s launch of the Paris Call for Trust and Security in Cyberspace in the fall of 2018,Footnote 1 amidst the collapse of international cyber norm discussions in June 2017, the international community has contemplated and launched multiple initiatives to restore a multilateral dialogue on the regulation of cyberspace in the context of international security. In December 2018, two resolutions were adopted by the United Nations General Assembly to set up two processes on progress in information and telecommunications in the context of international security: The sixth Group of Governmental Experts (GGE)Footnote 2 on the subject and a new Open-Ended Working Group (OEWG).Footnote 3 Then in October 2020, a few months before the end of these two processes, France and Egypt, together with thirty-eight countries and the European Union, proposed the launch of a program of action for advancing responsible state behavior in cyberspace,Footnote 4 while two new resolutions were once again adopted by the UN General Assembly.Footnote 5
At first sight, this profusion of initiatives looks like a renewed and strong interest among states in advancing cyber peace and stability. But the details reveal a more complex – and confusing – picture. Competing processes with overlapping mandates and agendas reflect the heightened strategic competition that prevails between great powers that pursue somewhat conflicting goals: Minimizing the risks to international peace, security, and cyber stability while maximizing their own cyber power, security, and normative influence. In other words, the cyber arms race is on and even though states aim at preserving collective security they are not ready to give up any of their ability to conduct offensive operations in cyberspace.Footnote 6 The road to cyber peace is paved with malicious intentions.
This chapter offers an analysis of the multilateral efforts conducted over the past decade to build cyber peace in a context of proliferation of cyber conflicts and exacerbated geopolitical tensions, not to mention the global COVID-19 pandemic that has largely disrupted international meetings. It studies more specifically how international law has been leveraged in UN negotiations to serve strategic objectives. International law plays a central role in state-level discussions on peace and stability in cyberspace, but it has been a source of tension since the very first resolution of the UNGA on the regulation of cyberspace in 1998. Although considerable progress has been made by previous GGEs – notably in 2013 and 2015 – in achieving consensus over the applicability of international law to cyberspace, fundamental disagreements persist that are grounded in conflicting geopolitical representations and interests.
States not only have opposing views on the necessary means to ensure security and stability in cyberspace, but also on the content of the negotiations themselves. This reflects their diverging perceptions of the risks associated with the militarization of cyberspace and with the possible forms of responses authorized by international law in reaction to internationally wrongful acts. It also reflects the entanglement of the issues at stake: Negotiating on protective principles, such as the principle of sovereignty, for example, which may limit states’ actions on the territory of other states, bears potential consequences that could extend to the lawfulness of the collection of transborder evidence.Footnote 7
The first part of the chapter explains the context in which the two competing 2018 UN processes were created and, second, examines the challenging – and largely overlapping – mandates they were given. It then analyzes the October 2020 state initiatives as a window into the geopolitical underpinnings of cyber peace building going forward.
1 The Short History of Cyber Peace Building
The OEWG and the sixth GGE were created by resolutions 73/27 and 73/266, adopted within a few days, on December 5 and 22, 2018, respectively, in a context of heightened tensions between states. For the first time since the discussion started in 1998, two resolutions on ICTs in the context of international security – instead of one – were adopted by the General Assembly. While their composition and calendar differ, their mandates are largely similar, making them competing processes in essence. This situation testified to an apparent division between two blocks of member states opposing each other on this topic.
Their creation followed a series of preceding GGEs and of UN-level discussions on progress in information and telecommunication in the context of international security that reached a dead-end in June 2017 with the failure of the fifth GGE, triggering a series of private sector and multistakeholder initiatives to maintain international discussions on the security and stability of cyberspace.
The history of cyber peace building is still young but its analysis helps to measure the progress that has been made so far, and the scope of what remains to be done.
1.1 How Cyberspace Became an International Security Issue in Multilateral Negotiations
In 1998, the Russian Federation introduced the theme of “Progress in information and telecommunication in the context of international security” at the United Nations General Assembly, initiating a multilateral discussion on the consequences of the development of state and nonstate actors’ cyber capacities on international security and stability (UNGA, Report of the First Committee, A/53/576 (1998)). This initiative led to the adoption of resolution 53/70 on December 4, 1998, by the General Assembly, which has since passed a resolution on the matter every year.
These resolutions created five successive GGEs up to 2016 (2004, 2009, 2012, 2014, and 2016). But the participants in the first GGE in 2004 proved unable to reach a consensus on a final report. As one of the experts in the Russian delegation later testified: “whether humanitarian international law and international law provided a sufficient regulation of security in international relations in case of a ‘hostile’ use of information and communication technologies for politico-military reasons was the main stumbling block.”Footnote 8 Hence, international law was, from the start, at the heart of the disagreements among governmental experts.
The following three GGEs, however, were successful and led to the adoption of consensual reports in 2010,Footnote 9 2013Footnote 10 and 2015Footnote 11. These reports were submitted to the General Assembly by the Secretary General. The UNGA took note of the reports and suggested that member states draw from them.Footnote 12 The GGE reports contain recommendations on confidence building measures prone to preserve the security and stability of cyberspace, along with measures of international cooperation and assistance that could be implemented by the states and, most importantly, norms of responsible state behavior in cyberspace.
The first major breakthrough was the recognition of the applicability of international law to cyberspace in the 2013 final report:
International law, and in particular the Charter of the United Nations, is applicable and is essential to maintaining peace and stability and promoting an open, secure, peaceful, and accessible ICT environment.Footnote 13
As a result, the following GGE was, for the first time, instructed to deal with international law.Footnote 14 Its final report in 2015 dedicated a full section (part 6) to international law, listing several rules. Since then, numerous states have endorsed this approach in their voluntary contributions to the Secretary General of the United Nations.Footnote 15
The fifth GGE, however, ended in failure in June 2017, amid a dispute over the interpretation of international law. The governmental experts were indeed not able to reach an agreement for the adoption of a consensual final report. Three states – China, Cuba, and Russia – refused the explicit mention in the final report of the applicability of certain branches of international law, namely, the right of self-defense, the law of countermeasures, and the law of armed conflict. Cuban and Russian governmental experts explained that the endorsement of the applicability of these branches of international law in cyberspace could serve to justify the militarization of cyberspace,Footnote 16 and they pointed at profound divergences in interpreting the law. This mention was regarded as crucial by other states, particularly the United States, which released an unusually bitter communiqué blaming “some participants” for the failure of the negotiations.Footnote 17 The representative of the United States was adamant:
I am coming to the unfortunate conclusion that those who are unwilling to affirm the applicability of these international legal rules and principles believe their States are free to act in or through cyberspace to achieve their political ends with no limits or constraints on their actions. That is a dangerous and unsupportable view, and it is one that I unequivocally reject.Footnote 18
The deadlock led a number of diplomats to claim that China and Russia were back tracking on the applicability of international law to cyberspace – which both countries denied – and that the discussion should continue among like-minded countries. The dreary perspectives over international discussions encouraged nonstate actors to jump in, given the explosion of confrontation in cyberspace and its increasingly damaging consequences.
1.2 A Multistakeholder Push to Reign in State Behavior
The Snowden revelations in 2013 uncovered the extent of state offensive activities in cyberspace and made the security and stability of cyberspace a widely public and highly political issue, provoking the first summit bringing together the Internet governance community with the international security community: The so-called Net Mundial conference in 2014. The conference produced a statement with recommendations on Internet governance principles and a roadmap for the future evolution of the Internet governance ecosystem. This nonbinding document was “the outcome of a bottom-up, open, and participatory process involving thousands of people from governments, the private sector, civil society, the technical community, and academia from around the world.”Footnote 19 Since then, the proliferation of state-sponsored attacks started to backfire with large-scale consequences, undermining the security and stability of cyberspace for all users.
The private sector, academic actors, and other stakeholders who participate in Internet governance instances started to claim their own legitimacy and interest in taking part in the discussions over the security and stability of cyberspace. Academics created and built the Internet, later globalized and commercialized by the private sector. Most of the infrastructures are owned by major private companies that are at the forefront of the attacks, often playing the role of first defender. Because of their data, resources, and skills, they are an essential partner of states for their cybersecurity. Global technology companies also have a vested interest in the security and stability of cyberspace for the trust of their users and the performance of their products, which are under constant attack.
Microsoft Corporation is by far the most important private actor in cybersecurity policymaking efforts, and leads multiple initiatives to promote cyber norms. As early as 2015, the company called on states – then on private companies – to adopt new norms. Most importantly, in 2017, its president, Brad Smith, proposed a Geneva Digital Convention for states to commit to protecting civilians against state-sponsored attacks, and the creation of an international organization for the attribution of cyberattacks.Footnote 20 The reference to international humanitarian law indirectly acknowledged the representation of cyberspace as a warfighting domain, but put the emphasis on the risk borne by civilians. The propositions were, however, regarded as infringing on states’ rights and privileges. They were also criticized for shifting all the responsibility on states while creating few constraints on the industry to secure its products, whose flaws are exploited by malicious actors to conduct offensive operations.
The company then shifted its focus to promote cyber peace through multiple initiatives: A public petition, a commitment for the industry (Cybersecurity Tech AccordFootnote 21), and the launch of the Cyberpeace Institute,Footnote 22 in partnership with the Hewlett Foundation and Mastercard in 2019. Its missions are to promote transparency and accountability by investigating and analyzing cyberattacks that impact civilians, provide assistance to the most vulnerable victims of cyberattacks, and promote cybersecurity norms of responsible behavior. The keyword is accountability, reflecting an interest in emphasizing state responsibility for the lack of cybersecurity. Other private sector initiatives were launched, such as the Charter of Trust,Footnote 23 initiated by Siemens in 2018, which contains ten principles to increase the resilience of digital products and the integrity of the supply chain.
The deadlock among states prompted the creation, in February 2017, of the Global Commission on the Stability of Cyberspace (GCSC), a multistakeholder group of international experts coming from academia, civil society and technical organizations, government, and the private sector. The Commission, initiated by the Ministry of Foreign Affairs of the Netherlands, and supported by several governments, private companies, and public organizations, started its work “convinced that an issue traditionally reserved to states—international peace and security—could no longer be addressed without engaging other stakeholders.”Footnote 24 During its three-year mandate, its mission was to propose norms and initiatives to guide responsible state and nonstate behavior in cyberspace in order to enhance international peace and security, with a main focus on stability, defined as such in its final report:
Stability of cyberspace means everyone can be reasonably confident in their ability to use cyberspace safely and securely, where the availability and integrity of services and information provided in and through cyberspace are generally assured where change is managed in relative peace, and where tensions are resolved in a non-escalatory manner.Footnote 25
In November 2017, the Global Commission proposed a Call to Protect the Public Core of the Internet, and that proposition has since been included in the European Union Cyber Security Act. It released its final report at the Paris Peace Forum of 2018 and the Internet Governance Forum held at the same time in Paris.
On the same occasion, the president of France launched the Paris Call for Trust and Security in Cyberspace (Paris Call, 2018), an initiative strongly supported by Microsoft, which led to a commitment to a set of principles and norms of responsible behavior of over 1,100 signatories, including 79 states, as of March 2021 – but not Russia, China, or the United States. The Paris Call refers to five GCSC norms, making explicit reference to three of them.Footnote 26 This initiative also demonstrates how some states attempt to draw from the legitimacy of multistakeholder support in order to build consensus over norms of responsible behavior for states and industry in cyberspace. This was also the approach favored by the Secretary General of the United Nations when setting up a High-Level Panel on Digital Cooperation in July 2018 to “advance proposals to strengthen cooperation in the digital space among Governments, the private sector, civil society, international organisations, academia, the technical community and other relevant stakeholders.”Footnote 27
Although states widely recognize the role of the private sector in the security and stability of cyberspace, and many of them endorse the multistakeholder governance model, they also perceive cyberspace as an international security threat that should be addressed by international regulation, which is the sole prerogative of UN Member States. It is in a very tense geopolitical context, marked by large-scale devastating attacks, information warfare targeting democratic processes, and the weakening of multilateral institutions that, eventually, the OEWG and the sixth UN GGE were created.
2 The Creation of Two Competing Processes at the UN: The Open-Ended Working Group and the Sixth Group of Governmental Experts
2.1 A Context of Heightened Strategic Competition
The resolutions creating the OEWG and the GGE were introduced by two groups of states, one led by the Russian Federation, the other one by the United States, forming seemingly adversarial blocs. But the reality is more complex and nuanced.
Russia, supported by China and other states,Footnote 28 proposed a first draft resolution in October 2018 creating an OEWG. The draft resolution listed not only norms adopted by the GGE in 2015, but also norms taken from the International Code of Conduct for Information Security proposed by the member states of the Shanghai Cooperation Organization in 2015 – and rejected by Western governments. In response, the United States submitted an alternative draft for a resolution creating a sixth GGE, which was supported by many European countries.Footnote 29 Eventually, Russia and cosponsoring states modified their project to account for the many criticisms they had received. But the United States and their cosponsors did not retract their own draft, arguing that the revised Russian draft still contained unacceptable provisions and did not reflect the 2015 GGE final report as well as it claimed. As a result, two competing resolutions on ICTs in the context of international security were debated in the First Committee of the UNGA; one promoted by Russia, the other by the United States. Both were adopted within a few days of each other, to the surprise of a number of states.
Heightened tensions between states surrounded the debates. According to the press communiqué describing the debates, Iran “[a]s a victim of cyber weapons,” supported the “establishment of international legal norms and rules aimed at preventing the malicious use of cyberspace and information and communications technology” and condemned “those seeking dominance and superiority in cyberspace and their attempts to maintain the status quo” and pointed to a certain state (the United States) which, “in collaboration with Israel, used the computer worm Stuxnet against Iran’s critical infrastructure, and yet has tabled a draft resolution regarding responsible state behaviour in cyberspace.”Footnote 30
The representative of China asked whether a negative vote on the Russian resolution would bring a “ticket” for the country to take part in the GGE, knowing that the number of participants is limited to twenty-five states, including the five permanent members of the UN Security Council.Footnote 31
The debates gave the impression of two competing blocs of states, sponsoring different resolutions initiated by two states with diametrically opposed approaches on how to regulate cyberspace and what the content of the negotiations should be: On the one side, the United States and European countries, usually described as the “like-minded state,” and on the other side, China and Russia. However, greater nuance is needed both in the homogeneity of the two blocs of states and the antagonism underlying their respective positions.
First, the countries in each group are not really homogeneous, they share certain characteristics in their approach that are not completely alike. There are, for example, important divergences between the Chinese approach and the Russian one,Footnote 32 as well as between France and the United States.
Second, the majority of UN member states did not adhere to any of the two groups and felt caught in the middle without a full grasp of the stakes. This supports an argument for the idea of two poles instead of two blocs of states structuring in international negotiations. More importantly, the vast majority of the member states voted in favor of both resolutions, as they regarded them as potentially complementary.Footnote 33 While these two processes might effectively be competing, they each advanced different sets of interests. The OEWG is open to all the member states, taking all the points of view into account. But, on the contrary, the composition of the GGE is limited to twenty-five member states designated “on the basis of equitable geographical distribution,”Footnote 34 the permanent members of the Security Council being ex officio members. Hence, the GGE appears as a more specialized entity which could lead to concrete progress on the core questions debated, whereas the nonlimited composition of the OEWG offers a more inclusive approach that allows each state to have its positions and interests heard.
The first session of the OEWG, which took place in New York in September 2019, actually highlighted the interests that many states have in taking an active part in the discussions – something confirmed by the high number of states involved in the second formal session in February 2020, as observed through the online videos of the debates on the UN website. Hence, the two ongoing processes are somewhat complementary. Despite the hostile climate that surrounded their creation, which reveal strong geopolitical tensions, they offer – in theory at least – a possibility for states to go beyond their inherent divisions and offer a smooth parallel functioning, or even synergy. The ambassadors Guilherme de Aguiar Patriota and Jürg Lauber, who preside over the GGE and the OEWG, respectively, actually advertised this constructive ambition from the moment they were nominated in these roles, as they have publicly declared on multiple occasions.
The complementarity of the two cyber norms processes has been highlighted by several states. However, an analysis of their respective mandates shows that, if they can be complementary, their mandates overlap to a certain extent, which does not facilitate the search for consensus and coherence in the negotiations.
2.2 Overlapping Mandates and Subtle Differences
At first glance, the mandates of the two groups are so similar they overlap to a large extent, with the risk of encroaching on one another. Indeed, both groups are mandated to work on the norms, rules, and principles of responsible behavior of the states, on confidence building measures, on capacity building, and international law. However, a careful reading reveals several differences.
First, the GGE can consult states that are not part of the GGE and competent regional organizations such as the African Union, the Organization of American States, the Organization for Security and Co-operation in Europe, and the Regional Forum of the Association of Southeast Asian Nations. The OEWG, on the other hand, is empowered to hold informal sessions to consult private actors and nongovernmental organizations. Furthermore, nonstate actors are authorized to attend the formal sessions as long as they have an accreditation with the United Nations Economic and Social Council (ECOSOC), following the Chinese refusal to further enlarge the pool.
Second, the GGE report is to be presented to the General Assembly with “an annex containing national contributions of participating governmental experts on the subject of how international law applies to the use of information and communications technologies by states.”Footnote 35 As such, the twenty-five countries participating in the GGE will have to clarify their position on the international law applicable to cyber operations. Some states, such as France and the Netherlands, have already moved forward in this regard. The French Ministry of Armed Forces published a report, International Law Applied to Cyberoperations,Footnote 36 in 2019, and the Dutch Ministry of Foreign Affairs also published International Law in Cyberspace in 2019.Footnote 37 These documents are most likely meant to be the two countries’ national contributions to the GGE.Footnote 38
Finally, the OEWG is tasked with examining “the possibility of establishing regular institutional dialogue with broad participation under the auspices of the United Nations”Footnote 39 to deal with ICTs in the context of international security. It could take the form of a permanent body or a new process.
A number of differences have raised concerns, starting with the respective timelines. The OEWG was supposed to end its work in 2020 and submit its report to the UNGA during its 75th session, a year before the GGE. Indeed, the GGE’s mandate ends in May 2021 and the GGE should thus present its report to the UNGA during its 76th session. The extension of the 75th session until March 2021, due to the COVID-19 crisis, allowed the OEWG’s work to continue in order to present it to the 76th session of the UNGA. The final deadlines for the two reports have therefore been preserved. Yet, some observers worry that several states behind the resolution creating the OEWG might change course after the end of its sessions. In other words, they would be adopting a constructive approach up to the end of the OEWG’s work in order to achieve a consensus on its conclusions, before becoming less cooperative during the remaining time of the GGE sessions to push for a failure, and boast of the superior achievements of the OEWG. But given the short time between the end of the two processes, this might be more difficult to achieve.
The second concern regards the content of the mandates. Both processes discuss international law, which constitutes a central topic in their proceedings. This can be seen both as an opportunity and a risk: States may conduct meaningful discussions and make progress on a consensus about the interpretation of international law in this new context of international peace and security, but they also may take diverging directions in the two processes, leading to a certain level of instability for the international legal order.
This concern also applies to norms of responsible state behavior, mentioned twice in resolution 73/27 that defines the mandate of the OEWG. The situation here is delicate for two reasons. The first mention of norms in resolution 73/27 appears early on in the definition of the OEWG mandate in paragraph 5.Footnote 40 Norms – as stated in the resolution – constitute the working base of the OEWG, but their definition is slightly different from the norms of the 2015 GGE report to which they refer. The mandate of the GGE is clearer since resolution 73/266 refers exclusively to the GGE report. As a result, the working base of the two processes could slightly differ and potentially increase the risks of divergence, or even contradiction in the meaning of the recommendations adopted by each process. For example, the recommendation on the prevention of malicious computer tools or technologies is included in a paragraph on supply chain integrity in the 2015 GGE report, whereas it is the subject of a stand-alone provision in resolution 73/27 that creates the OEWG. This could indicate a desire to work more extensively on the issue of proliferation in the context of the OEWG.
The practice of the states, however, shows that this risk remains limited as a large majority of states, during the first two sessions of the OEWG, opted for the norms as stated in the 2015 GGE report. This illustrates the lack of consensus on the norms as stated in the provisions of resolution 73/27, but it also highlights a gap between a strict application of the mandate and the practice adopted by states during the negotiations.
The uncertainty around the working base could also affect other aspects of the negotiations, such as norm implementation.Footnote 41 Member states are tasked with detailing the operationalization of the norms. Because several of them are quite vague, they need to be specified in order to be implemented. Finally, the OEWG mandate paves the way for a possible reappraisal of the agreed provisions of the 2013 and 2015 GGEs as states are able to “introduce changes,”Footnote 42 including establishing new norms. Elaborating new norms is authorized by resolution 73/27 and could involve creating new norms that better define what responsible behavior is, or revisit the norms adopted in the 2013 and 2015 reports.
The second mention of norms in the resolution 73/27 can be found in the second part of the definition of the mandate. But it does not state explicitly if this mention refers to the norms stated in resolution 73/27 or the ones adopted by the GGEs in 2013 and 2015.
A close reading of the mandate thus highlights a number of questions related to the working base on which the negotiations are to be conducted. The practice of using the GGE norms have prevailed so far, but contradictions could emerge as both the GGE and the OEWG are tasked with working on these provisions.
It was also hard to know how the work would be divided between the two processes, given the fact that international law and norms of responsible behavior are mentioned in both mandates. In his speech during the first session of the OEWG in June 2019, the special representative of the President of the Russian Federation for international cooperation in information security proposed that the OEWG deals with norms of responsible behavior, confidence building measures, and measures of international cooperation and assistance, hence leaving the issue of international law to the GGE.Footnote 43 This proposal was not accepted. As a result, both processes work concomitantly on the entire set of issues.
This situation is both understandable and problematic. On the one hand, international laws and norms of responsible state behavior are intrinsically linked and, therefore, difficult to completely dissociate. On the other hand, this situation reinforces the risk of repetitions in the content of the negotiations, and also the risk of contradictions in the recommendations made by the two groups on the rights and obligations of states. Most importantly, the refusal to dissociate them highlights disagreements on the necessary means to ensure security and stability of cyberspace.
The COVID-19 pandemic has added a layer of complexity. In addition to overlapping mandates, the two processes have ended up with largely overlapping calendars since the two final reports will be produced a month apart from each other. It is, however, difficult to assess whether this overlapping can help build synergy between the two processes or fuel further rivalry. Most importantly, states have not waited for the end of these two processes, as initially planned, to propose new processes.
3 Bumpy Road to Cyber Peace
3.1 New Path(s) for Cyber Stability?
In the face of potential difficulties in reaching consensus over a final report and successfully coordinating the two existing processes, France and Egypt, supported by thirty-eight countries and the European Union, proposed on October 1, 2020, a new path to cyber stability: The creation of a Program of Action (PoA) for advancing responsible state behavior in cyberspace, a proposal made to all member states within the context of the OEWG. Neither China, Russia, nor the United States have been officially part of this initiative.
A PoA consists of the production of an outcome document adopted by an intergovernmental conference, considered as politically binding, which contains objectives, recommendations, and rules for implementation and monitoring, in a new process with working conferences every other year including a review conference every five years.Footnote 44 It would, therefore, fulfill one of the objectives of the OEWG; that is, “study the possibility of establishing a regular institutional dialogue with broad participation under the auspices of the United Nations.”Footnote 45
This process would present the advantage of bringing the discussion back into a single process more inclusive than the GGE. As a new process, it would also be free from all the political baggage linked to the United States versus Russia rivalry over the GGE and OEWG processes. Unlike previous dialogues, it would not require building a consensus over a final report but, rather, building a working relationship that fosters practical cooperation and allows for agreement on specific issues as the discussions progress. There would be no end dates, even if states fail to agree on an outcome document at the end of a technical or review conference. The ultimate goal is to preserve and build on the agreed provisions of the previous GGE by providing a “forum for practical cooperation and ongoing discussions.”Footnote 46
Although the proposition was well received, two draft resolutions were put forward before the UNGA First Committee a few days later.Footnote 47 On October 5, a coalition of forty-six member states led by the United States, including France and many supporters of the PoA, proposed a draft resolution entitled “Advancing responsible state behaviour in cyberspace in the context of international security.” The resolution acknowledges the ongoing discussions at the GGE and OEWG and declares that member states will study the conclusions of both groups and “will decide thereafter on any future work, as needed.”Footnote 48
The very next day, jumping ahead of the calendar, Russia along with fourteen other states proposed another draft resolution stating – in operative paragraph 1 – that the UNGA will create a new OEWG starting in 2021, without waiting for the conclusions of the two ongoing processes.Footnote 49 A revised version was submitted on October 26, specifying that the new OEWG “shall start its activities up to the conclusion of the work of the current Open-Ended Working Group and considering its outcomes”.Footnote 50 The revised version, however, leaves room for interpretation as to whether the acquis will be preserved, since the mandate of the new OEWG includes the possibility to “if necessary, … introduce changes to them [the norms] or elaborate additional rules of behaviour.”Footnote 51 In addition, this new draft resolution borrows from the PoA approach by stating that the new OEWG “may decide to establish thematic subgroups, as the Member States deem necessary, with a view to fulfilling its mandate and facilitating the exchange of views among States on specific issues related to its mandate, and may decide to interact, as appropriate, with other interested parties, including businesses, non-governmental organizations and academia.”Footnote 52 Yet, while it opens the door to consultations with nonstate actors, the drafting is less prescriptive than in the resolution that created the first OEWG, and it will limit nonstate actors’ participation in the discussions for the next five years. And, finally, there is a tweak that leaves the question of its future mandate open: The name changed from “OEWG on developments in the field of information and telecommunications in the context of international security” to “OEWG on security of and in the use of information and communication technologies.”Footnote 53
Both draft resolutions were submitted to a vote at the First Committee on November 9, 2020, and both were adopted. The UNGA adopted both of them respectively on December 7th (UNGA Res. 75/32 (2020)) and December 31st (UNGA Res. 75/240 (2020)), adding more confusion to the field of competing processes. The PoA was proposed to all participating states during the discussions held within the OEWG, and offered to continue the negotiations within a single process. The resolution sponsored by Russia offered to continue this dialogue within the OEWG and the resolution sponsored by the United States suggested to wait and see. These competing initiatives have fostered strong debates within the United Nations and, more broadly, among actors involved on these matters.
3.2 The Contest for Normative Influence
Once again, the debates seemed to oppose two blocs, one led by the Russian Federation and the other by Western states along with Australia, even though the reality was more complex. We studied the coalition of sponsors and the votes at the UNGA for each resolution. The analysis reveals that the United States gained support among states since its 2018 resolution, while Russia has lost part of its support (Figure 9.1).
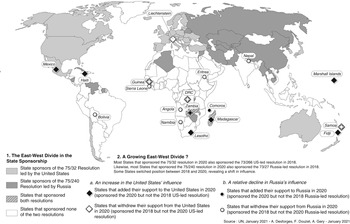
Figure 9.1 State sponsorship of 2020 UN Cyber Diplomacy Resolutions: a persistent east-west divide.
The map “State Sponsorship of 2020 UN Cyber Diplomacy Resolutions” illustrates a clear east-west divide regarding the sponsorship of the two resolutions. The US-led resolution 75/32 was overwhelmingly supported by Western countries while the Russian led resolution 75/240 was supported by Eastern Countries. But the map also reveals a slight change of balance in favor of the United States. In 2020, eight states that had sponsored the Russian-led resolution in 2018 withdrew their support to Russia for the 2020 resolution. In the meantime, two states (Comoros and Zambia) added their support to Russia; that is, sponsored the 2020 resolution but not the 2018. But Zambia also sponsored the US-led resolution. On the contrary, the US-led resolution gained sponsorship between 2018 and 2020: Seven states added their support to the United States in 2020 while four withdrew their support, as illustrated by the graph in Figure 9.2.
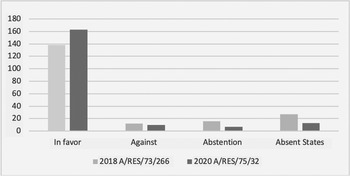
Figure 9.2 The 2020 US-led resolution gains more votes than the 2018 resolution.
The two draft resolutions were introduced before the UN First Committee on the October 5–6, 2020. The first one, “Advancing responsible State behaviour in cyberspace in the context of international security,”Footnote 54 was introduced by the United States on behalf of fifty-three states, against fifty-one states for the 2018 US-sponsored resolution.Footnote 55 The vote at the First Committee reached a large consensus with 153 states in favor, 9 against, and 9 abstaining. The UNGA adopted the resolution in its plenary session on December 7, 2020, by an even larger margin: 163 in favor, 10 against, and 7 abstaining. By comparison, the 2018 US-sponsored resolution was adopted by a lower margin (138 in favor, 12 against, 9 abstaining). This can be explained by the noncontentious nature of the 2020 resolution, which did not involve a strong commitment to a specific process.
The draft resolution A/C.1/75/L.8/Rev.1, sponsored by Russia on behalf of twenty-six states (thirty-four in 2018), however, was faced with harsh criticism coming mainly from Western states. The representative of the Russian Federation, speaking in exercise of the right of reply, said: “Western delegations are sabotaging the process and breaking with decades of consensus on cybersecurity.” As such, his delegation was offended by their level of cynicism and hypocrisy, which stalled the work of the OEWG. He added, “If it were not for the Russian Federation, the United Nations would not have open negotiations on the matter.”Footnote 56
The opposition focused on operative paragraph 1, creating a new OEWG for 2021. Western states objected that it is part of the mandate of the present OEWG to make suggestions about future institutional work and, therefore, decide whether a new OEWG should be created. The draft resolution would thus preempt the work of the present OEWG. They therefore asked for the withdrawal of this operative paragraph and all related ones.
The Russian delegates strongly opposed this demand; they believed that this would void the resolution of all substance and invoked article 129 of the Rules of Procedures of the UNGAFootnote 57 to have the contentious operative paragraph 1 be voted on separately instead of withdrawn. This situation in itself illustrates the opposition between Western states and the Russian Federation. As a result, the President of the First Committee put to a vote the decision regarding the division of the draft resolution, which was approved by fifty-seven states in favor, thirty-one against, and sixty-three abstaining. Once the division approved, the First Committee then proceeded to the three following votes on: the preamble (108 in favor, 49 against, 11 abstaining); the operative paragraph 1 (92 in favor, 52 against, 24 abstaining); and the resolution as a whole (104 in favor, 50 against, 20 abstaining).
The resolution was thus submitted to the UNGA and adopted on December 31, 2020. The date in the middle of the holiday season may explain the high number of absent states on the day of the vote. The voting data show an overall support for the resolution and also a sizeable opposition: ninety-two in favor, fifty against, and twenty-one abstaining. The Russia sponsored resolution was nevertheless adopted by the UNGA, yet the number of States voting in favor (92) was drastically lower than for the 2018 Russia sponsored resolution (119 in favor). However, this result must be interpreted with caution. Thirty states were absent from the UNGA that day, among which eighteen states who voted in favor of the Russia sponsored resolution in 2018. A close reading of the votes shows, however, that Russia indeed lost the support of an additional thirteen member states compared to 2018, as illustrated by the graph in Figure 9.3.
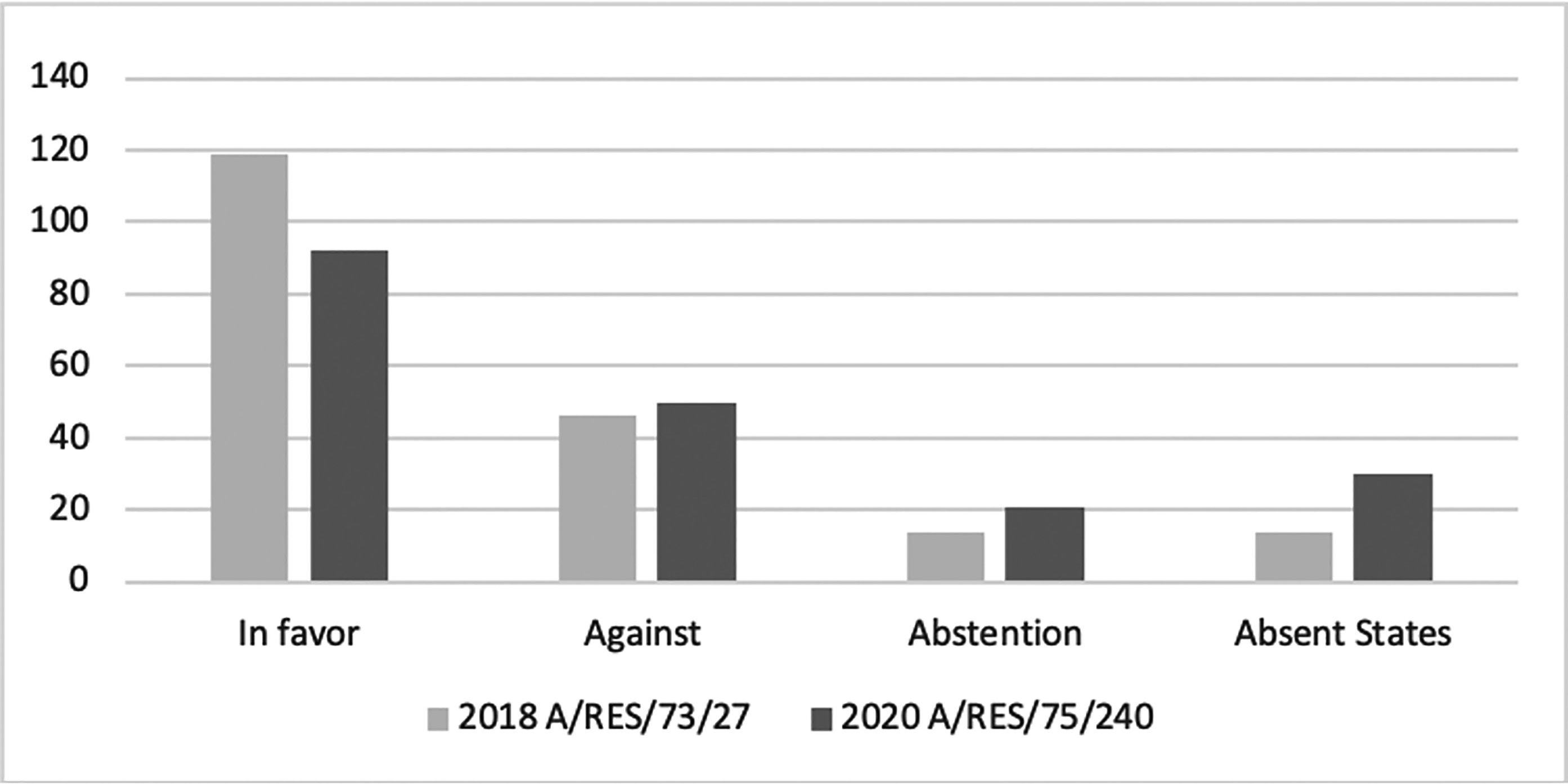
Figure 9.3 The 2020 Russian-led resolution gathers less votes than the 2018 resolution.
The charts “The 2020 UNGA Balance of Votes” illustrate the percentage of states that voted in favor of each resolution, against it, or abstained (Figure 9.4).
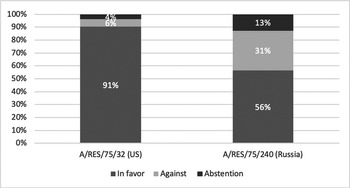
Figure 9.4 The 2020 UNGA balance of votes.
The map “UNGA Vote on 2020 Cyber Diplomacy Resolutions,” with the votes on the two resolutions, highlights the dynamics of power between states. First, it confirms the East-West divide observed on the state sponsorship map. It also confirms the growing support gained by the United States, whose resolution was adopted by a larger and growing margin of states (with fewer absent states) and by less opposition. In addition, support for the US-led resolution appeared more consistent. All the states that had only sponsored the US-led resolution in 2020 voted for it and, in addition, voted against the Russia-led resolution (none of them abstained or voted in favor of it) (Figure 9.5).
Figure 9.5 UNGA vote on 2020 Cyber Diplomacy Resolutions: a majority of states caught between two stools.
On the contrary, several states that had sponsored the Russia-led resolution did not oppose the US-led resolution: They either voted in favor of it or abstained. This could be explained by the fact that the US-led resolution is more consensual than the Russia-led resolution, but it also reveals a more complex picture. A majority of states either voted for both resolutions or voted for one and abstained from the other. This shows that the East-West divide is clear, but most states – caught between two stools – chose not to position themselves within this duopoly. Any claim that international negotiations on the security and stability of cyberspace is marked by a strong opposition between two blocks of states should thus be cautioned.
Conclusion
The cyber peace building dynamics at the United Nations reflects fundamental disagreements on the means to ensure the security and stability of cyberspace and the struggle for normative influence among states.
Russia has justified its 2020 initiative by the desire to ensure that international discussions would continue after the end of the two processes, highlighting its role in opening negotiations. But the Russian Federation might also be defending another agenda, along with its own legal culture and perspective. Russia makes no secret of wanting to elaborate a treaty for cyberspace, an option best preserved by the OEWG process. A PoA, on the contrary, could considerably delay the perspective of a treaty by providing a process with no end date and “politically binding” decisions, a compromise that is a priori at odds with Russia’s legalist approach to international relations. Yet, Russia could also use the PoA as a vehicle to launch the drafting process of a treaty.
The analysis of the maps shows there is a strong polarization between the United States and Russia and a relative decline in Russia’s influence. However, Russia’s leadership is still strong enough to get its resolution voted by the UNGA and there is still a vast reserve of votes, given the ambiguous position of a significant number of states. Indeed, a majority of states did vote for both resolutions, or chose to vote for one resolution without opposing the other.
To the surprise of all observers, states participating in the OEWG were able to reach a consensus and adopt a report on March 12, 2021,Footnote 58 while the GGE had still not ended its mandate. Meanwhile, a new OEWG is scheduled to start its work soon after the adoption of the consensus report since the UNGA enacted its creation in resolution 75/240. This leaves the question of the creation of other processes totally open, particularly since the PoA proposal has been acknowledged by the OEWG. Indeed, the final report recommended that “the Programme of Action should be further elaborated including at the Open-Ended Working Group process established pursuant to General Assembly resolution 75/240.”Footnote 59 Although the report states that the PoA should be discussed within the future OEWG, it also leaves room for discussion of a PoA in another context. In this regard, the French Ambassador for Digital Affairs, Henri Verdier, announced on March 24, 2021 that France was considering launching the PoA in October 2021Footnote 60; that is, at the beginning of the 76th session of the UN General Assembly. If this was to happen, it would raise the question of how many processes could states handle without ending in a total deadlock, letting alone the fact that another GGE could also be created in the meantime. While the PoA could offer a productive venue for states that wish to work on more action-oriented recommendations, it could also lead to more bumps in the road to cyber peace.
The road to cyber peace is arduous, given the will of states to preserve their ability to conduct cyber offensive operations. Official documents tend to refer to cyber stability rather than cyber peace as a goal for international negotiations.Footnote 61 The proliferation of damaging attacks and the risk of conflict escalation in cyberspace have led states to leverage the traditional instruments of collective security – such as international law and nonbinding norms of responsible behavior – to regulate cyberspace. In the early stages of consensus building up to 2016, these instruments have helped advance the discussions by providing an existing legal framework applicable to cyber operations as a basis for negotiation. But since then, the renewed strategic competition and exacerbated geopolitical tensions have led states to engage not only in a cyber arms race, but also in a competition for normative influence. As a result, international law has proved to be exactly what it is: An instrument in the service of state foreign policy – with the risk to lead states to a stalemate.








