No CrossRef data available.
Article contents
Large deviations of Poisson Telecom processes
Published online by Cambridge University Press: 12 October 2022
Abstract
We study large-deviation probabilities of Telecom processes appearing as limits in a critical regime of the infinite-source Poisson model elaborated by I. Kaj and M. Taqqu. We examine three different regimes of large deviations (LD) depending on the deviation level. A Telecom process
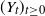 $(Y_t)_{t \ge 0}$
scales as
$(Y_t)_{t \ge 0}$
scales as
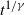 $t^{1/\gamma}$
, where t denotes time and
$t^{1/\gamma}$
, where t denotes time and
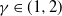 $\gamma\in(1,2)$
is the key parameter of Y. We must distinguish moderate LD
$\gamma\in(1,2)$
is the key parameter of Y. We must distinguish moderate LD
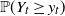 ${\mathbb P}(Y_t\ge y_t)$
with
${\mathbb P}(Y_t\ge y_t)$
with
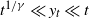 $t^{1/\gamma} \ll y_t \ll t$
, intermediate LD with
$t^{1/\gamma} \ll y_t \ll t$
, intermediate LD with
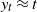 $ y_t \approx t$
, and ultralarge LD with
$ y_t \approx t$
, and ultralarge LD with
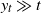 $ y_t \gg t$
. The results we obtain essentially depend on another parameter of Y, namely the resource distribution. We solve completely the cases of moderate and intermediate LD (the latter being the most technical one), whereas the ultralarge deviation asymptotics is found for the case of regularly varying distribution tails. In all the cases considered, the large-deviation level is essentially reached by the minimal necessary number of ‘service processes’.
$ y_t \gg t$
. The results we obtain essentially depend on another parameter of Y, namely the resource distribution. We solve completely the cases of moderate and intermediate LD (the latter being the most technical one), whereas the ultralarge deviation asymptotics is found for the case of regularly varying distribution tails. In all the cases considered, the large-deviation level is essentially reached by the minimal necessary number of ‘service processes’.
MSC classification
- Type
- Original Article
- Information
- Copyright
- © The Author(s), 2022. Published by Cambridge University Press on behalf of Applied Probability Trust





