Cybervetting, or using information drawn from the internet and social media websites to screen job candidates and make hiring decisions, is widely practiced by employers. Estimates of the prevalence of cybervetting as a means of screening job candidates range from 43% of human resources (HR) professionals in a 2015 survey (Society for Human Resources Management [SHRM], 2016) to 70% of hiring managers and HR professionals combined, as found by a more recent study conducted in 2018 (CareerBuilder, 2018). However, online screening of job candidates is more common in certain fields, such as IT, in which 74% of hiring managers and HR professionals report cybervetting (CareerBuilder, 2018). Its prevalence also varies with the position being filled. Cybervetting is more common when hiring for managerial and salaried than hourly or entry-level jobs. Research also suggests it may also be more common for “front stage” positions with high levels of customer interaction than for “back stage” roles (Chang & Madera, Reference Chang and Madera2012; SHRM, 2016). The overall picture that emerges from scholarly and industry research is one of a widespread and growing hiring practice.
Cybervetting warrants researchers’ attention not only due to its popularity but also due to its distinction from traditional hiring and selection procedures. Compared with traditional hiring practices (such as application submissions, phone calls, and interviews), cybervetting affords job seekers less control over the information that hiring agents use to evaluate them (Hedenus & Backman, Reference Hedenus and Backman2017) and offers hiring agents greater access to job candidates’ personal information (Zhang etal., Reference Zhang, Van Iddekinge, Arnold, Roth, Lievens, Lanivich and Jordan2020). It occurs earlier in the hiring process and can be used to quickly scan larger numbers of people. Cybervetting also involves one-way vetting rather than two-way interaction, giving job candidates less say in the evaluation process.
The cybervetting literature is a developing arena that remains quite limited. Previous research has little to say about the potential consequences of cybervetting, especially from the perspective of job seekers who are subjected to and hiring agents who engage in this practice. How does cybervetting affect individuals’ job search experiences and hiring agents’ work activities? How does it influence organizational success and intersect with other social problems? We posit that the growing pervasiveness of cybervetting renders consideration of its consequences, as well as steps to minimize its potential harms, of utmost concern. We examine the implications of cybervetting for three key stakeholders: job candidates, hiring agents, and organizations. Based on a review of existing literature as well as our own research—an interview study of 77 hiring agents (human resource professionals, recruiters, hiring managers, and related market actors) in the Atlanta and Raleigh-Durham metro areasFootnote 1—we discuss the consequences of current cybervetting practices for each stakeholder group and then outline steps that could be taken by each to minimize cybervetting’s negative outcomes. In making recommendations for future practice, we emphasize the steps that organizations can take to ameliorate cybervetting concerns, given the relative power and sway of organizations as compared with individual job candidates and hiring agents. We also suggest actions that professional associations and government should take to ensure that business organizations are held accountable.
Job candidates: Perceptions and experiences of the cybervetted
Workers today face unprecedented demands to manage their public images. This stems largely from two concurrent shifts: the rise of internet-based communications and major transformations in the social contract that implicitly and explicitly governs employment relationships. The internet has spawned a variety of job posting boards, automated hiring applications, and social media platforms, which together have greatly increased the capacity of organizations to gather information about actual and potential job candidates (Ajunwa & Greene, Reference Ajunwa, Greene, Vallas and Kovalainen2019). At the same time, the new employment contract (Rubin, Reference Rubin2012) has transformed workers from stable employees into “free agents” who are responsible for continuously (re-)securing their own economic and social well-being (Gershon, Reference Gershon2017; Kalleberg, Reference Kalleberg2011; Smith, Reference Smith2002). Increasing flexibility in terms of where, when, and for whom one works is a burgeoning expectation (Harvey etal., Reference Harvey, Rhodes, Vachhani and Williams2017; Kalleberg, Reference Kalleberg2011; Smith, Reference Smith2002), and perceived employment insecurity is a rising issue due to shifting employment relations (Fullerton & Wallace, Reference Fullerton and Wallace2007; Kalleberg, Reference Kalleberg2011). Successful online impression management is one factor that can make it easier for individuals to obtain (and maintain) work (Roulin & Levashina, Reference Roulin, Levashina, Landers and Schmidt2016). Online impression management is one form of “employment management work” (Halpin & Smith, Reference Halpin and Smith2017) that individuals engage in to manage how employers see them and thereby protect their present and future employment status (Roulin & Levashina, Reference Roulin, Levashina, Landers and Schmidt2016). Individuals may undertake online impression management regardless of whether they are actively searching for jobs (e.g., Duffy & Chan, Reference Duffy and Chan2019; Hurrell etal., Reference Hurrell, Scholarios and Richards2017; Scolere etal., Reference Scolere, Pruchniewska and Duffy2018). Both employers and workers consider it a normalized expectation to which individuals must adhere in order to maintain a professional image (Berkelaar, Reference Berkelaar2014).
Job candidatesFootnote 2 manage risk via defensive strategies directed at preventing negative employment outcomes in the future. Concerns with risk management arise from perceiving “the scrutiny that could take place across the social media ecology and, consequently, may engender future risks or opportunities” (Duffy & Chan, Reference Duffy and Chan2019:121). Individuals may use privacy settings and aliases or pseudonyms to block potential employers from accessing content seen as “inappropriate” (e.g., drinking photos) and monitor the content posted on more widely accessible platforms in order to ensure that it is indeed “appropriate” (Duffy & Chan, Reference Duffy and Chan2019). Individuals may restrict “less appropriate” content to informal platforms where content is accessible only to close friends (e.g., Snapchat; Duffy & Chan, Reference Duffy and Chan2019) or simply avoid posting such content on social media at all (Roulin, Reference Roulin2014). Individuals are more likely to avoid posting “inappropriate” content on social media when aware of the employer monitoring that takes place (Roulin, Reference Roulin2014). Engaging in these risk-management practices enables job candidates to limit their feelings of uncertainty in an employment context that offers workers little protection against it (Smith, Reference Smith2002).
Simultaneously, active job seekers in particular undertake a more offensive strategy of managing fit to maximize their chances of getting a job. Research illustrates the importance of portraying oneself as a “good fit” with a job or an organization in order to succeed in interviews (Barrick etal., Reference Barrick, Shaffer and DeGrassi2009; Rivera, Reference Rivera2015). Job candidates portray their fit online by creating a unique but highly positive “personal brand” to sell themselves to potential employers (Gershon, Reference Gershon2017). Job seekers use platforms that they perceive as best suited for accomplishing their personal branding (Scolere etal., Reference Scolere, Pruchniewska and Duffy2018), add personal touches (e.g., stories, images) to their profiles to foster a connection with hiring agents, and constantly tailor their online profiles to the next jobs for which they are interviewing (Sharone, Reference Sharone2014). The commonality of individuals’ fit-management strategies (Hurrell etal., Reference Hurrell, Scholarios and Richards2017) is unsurprising given the frequent use of cybervetting as well as employer’s increasing emphasis on hiring “perfect” job candidates (McDonald etal., Reference McDonald, Damarin, Lawhorne, Wilcox, Vallas and Kovalainen2019).
Insecurities and identities online
Widespread societal pressures to engage in risk- and fit-directed online impression management have numerous negative consequences. Insecurity arises from uncertainty about the potential effects of one’s online actions and the “best” way to portray oneself online (Duffy & Chan, Reference Duffy and Chan2019; Sharone, Reference Sharone and Vallas2017). Job candidates have a general sense that someone might be looking at their profiles, now or in the future, but worry about who might be looking, when they might be looking, and what negative outcomes might happen as a result (Duffy & Chan, Reference Duffy and Chan2019). Due to the highly subjective process of interpreting online signals, as well as the lack of clear guidelines for maintaining a strong online persona (Gershon, Reference Gershon2017), candidates experience insecurity in deciding whether and how to manage their online professional identities. For example, individuals belonging to marginalized groups may be wary of posting profile pictures that could facilitate discrimination but may also worry that if they do not post a profile photo, they will be overlooked by hiring agents (Sharone, Reference Sharone and Vallas2017).
Job candidates also experience anxiety arising from the difficulty of negotiating various identities online. Social networking sites complicate individuals’ ability to maintain a personal identity distinct from their professional identity given that personal posts may be subjected to employer scrutiny and should therefore look professional (Duffy & Chan, Reference Duffy and Chan2019; Sharone, Reference Sharone and Vallas2017). This creates unrealistic demands because people have multiple identities and often adjust their portrayal of self, depending on with whom they are communicating (van Dijck, Reference van Dijck2013). For example, individuals are more likely to post “inappropriate” content when trying to impress their friends and less likely to post “inappropriate” content when trying to convey positive impressions to potential employers (Roulin, Reference Roulin2014). The obligation that individuals portray their one “true” identity on social networking sites—an assumed obligation built into the layout and features of sites such as Facebook and LinkedIn—creates further complications during the job search process (Sharone, Reference Sharone and Vallas2017; van Dijck, Reference van Dijck2013). On LinkedIn, individuals are allowed only one profile, which can pose difficulties for those attempting to tailor their profiles to different jobs for which they are applying (Sharone, Reference Sharone and Vallas2017). Facebook’s timeline feature imposes a similar limitation by synthesizing all of the information users have ever posted on the site and sharing these data with the public by default (van Dijck, Reference van Dijck2013).
For active job seekers who are unable to find work, the demand to manage one’s online persona can also encourage self-blame. When the burden of illustrating job “fit” hinges on the candidate, repeated rejection leads job seekers to believe that their inability to obtain a job is due to some inherent personal flaw (Sharone, Reference Sharone2014). Individuals who are unable to find a job may begin to question their personal deficiencies or lament their past decisions (Lopez & Phillips, Reference Lopez and Phillips2019). These feelings of self-blame, shame, and inadequacy can plague the job search experience and discourage individuals from continuing with the process (Lopez & Phillips, Reference Lopez and Phillips2019; McDonald etal., Reference McDonald, Damarin, Lawhorne, Wilcox, Vallas and Kovalainen2019; Sharone, Reference Sharone2014). Given that rejection and continued unemployment is more common among marginalized groups, such as racial minorities (e.g., McBrier & Wilson, Reference McBrier and Wilson2004; Pager etal., Reference Pager, Bonikowski and Western2009), individuals with marginalized identities likely experience intensified self-blame arising from pressure to portray oneself as a good “fit” with jobs and employers.
Job candidates’ perceived lack of privacy
Individuals also tend to perceive cybervetting as a violation of privacy or as unjust (Berkelaar, Reference Berkelaar2014; Hurrell etal., Reference Hurrell, Scholarios and Richards2017; Madera, Reference Madera2012; Stoughton etal., Reference Stoughton, Thompson and Meade2015; Suen, Reference Suen2018). Cybervetting is associated with lower levels of perceived procedural justice among job candidates (Bauer etal., Reference Bauer, Truxillo, Tucker, Weathers, Bertolino, Erdogan and Campion2006; Madera, Reference Madera2012; Stoughton etal., Reference Stoughton, Thompson and Meade2015; Suen, Reference Suen2018), and this relationship persists regardless of the hiring outcome (Stoughton etal., Reference Stoughton, Thompson and Meade2015).Footnote 3 Perceived lack of privacy and procedural justice further encourage the previously discussed anxieties that job candidates experience. Perceiving a lack of privacy online makes online impression management seem especially important (Duffy & Chan, Reference Duffy and Chan2019), whereas perceiving a lack of procedural justice may feed worries about discrimination.
The relationship between online screening and perceived procedural justice may be moderated by individual characteristics (Stoughton etal., Reference Stoughton, Thompson and Meade2015), perceived transparency of the data collection process (Black etal., Reference Black, Stone and Johnson2015; Suen, Reference Suen2018), and perceived relevance of the collected data (Alge, Reference Alge2001). Candidates who are able to manage their online presence may be less worried about cybervetting constituting an invasion of privacy. Employees involved in the design or operation of surveillance tend to perceive less invasion of privacy and greater procedural justice (Alge, Reference Alge2001). Candidates who tailor their online profiles to potential employers (Hurrell etal., Reference Hurrell, Scholarios and Richards2017) and who expect to receive a favorable evaluation as a result of employer screening (Kuhn & Nielsen, Reference Kuhn and Nielsen2008) perceive employers’ use of screening as more fair and acceptable than those who do not. Among candidates with greater confidence about their personal ability to control their online presence, there is a weaker relationship between employer use of online screening and candidates’ perceived violation of privacy (Suen, Reference Suen2018). This suggests that increased individual agency and control may help to ameliorate, but not necessarily cancel out, the negative privacy implications of cybervetting. As Hedenus and Backman (Reference Hedenus and Backman2017) have observed, the maintenance of online employability in the form of a sanitized and professionalized digital identity is an exercise in self-reflection, which may be viewed as empowering for employees or as an instance of coerced adaptation to organizational norms.
Discriminatory effects for job candidates
A third potential implication of cybervetting for job candidates is objective and subjective discrimination. Extensive research documents discrimination targeting individuals with marginalized social identities during the hiring process. Audit studies show that Black job applicants are less likely to receive callbacks than White job applicants (Gaddis, Reference Gaddis2015; Pager etal., Reference Pager, Bonikowski and Western2009; Pager & Quillian, Reference Pager and Quillian2005), queer women are less likely to receive callbacks than straight women (Mishel, Reference Mishel2016), and socioeconomically privileged and high-achieving women are less likely to receive callbacks than their male counterparts (Quadlin, Reference Quadlin2018; Rivera & Tilcsik, Reference Rivera and Tilcsik2016). Such discriminatory hiring decisions are shaped by stereotypical beliefs about which categories of individuals are the “most appropriate” for certain jobs (Abrams etal., Reference Abrams, Swift and Drury2016; Heilman, Reference Heilman2012; Koch etal., Reference Koch, D’Mello and Sackett2015; Moss & Tilly, Reference Moss and Tilly1996; Waldinger & Lichter, Reference Waldinger and Lichter2003). For example, the stereotype that socioeconomically privileged women are “less committed” to demanding careers harms their prospects on the job market (Rivera & Tilcsik, Reference Rivera and Tilcsik2016). Given that information about an individual’s social group identities, such as race and gender, is widely available on social media (Zhang etal., Reference Zhang, Van Iddekinge, Arnold, Roth, Lievens, Lanivich and Jordan2020), cybervetting is likely to exacerbate the influence of stereotypical and discriminatory decisions in the hiring process.
Despite some research on the effect of formalized organizational policies (e.g., Balser, Reference Balser2002; Hirsh & Lyons, Reference Hirsh and Lyons2010; Kaiser etal., Reference Kaiser, Major, Jurcevic, Dover, Brady and Shapiro2013), we are unable to find any literature examining how perceived discrimination is affected by the largely informal practice of cybervetting. This promises to be a fruitful avenue for future industrial-organizational psychology research. Although perceived procedural justice is a primary focus of the cybervetting literature, it is only one of the factors that could lead to perceived discrimination and is therefore a narrower concern (Harris etal., Reference Harris, Lievens and Hoye2004). To the extent that cybervetting leads to perceived discrimination more broadly, it can have a wide range of negative outcomes for job candidates. Perceived discrimination is associated with increased physical and psychological health problems and has negative consequences for work-related outcomes such as job satisfaction and organizational citizenship behavior (Ensher etal., Reference Ensher, Grant-Vallone and Donaldson2001; O’Brien etal., Reference O’Brien, McAbee, Hebl and Rodgers2016; Triana etal., Reference Triana, Jayasinghe, Pieper, Delgado and Li2019). It also has implications for individuals’ job search patterns and outcomes. For example, African Americans who perceive having been subject to discrimination in the workplace are more likely to apply for a wider range of jobs, which expands their likelihood of finding a new job but also leads to reduced wages (Pager & Pedulla, Reference Pager and Pedulla2015). Given the potential objective and subjective discriminatory effects of cybervetting, future research examining cybervetting and perceived discrimination is needed in order to address implications of cybervetting for job candidates more comprehensively.
Hiring agents: Perceptions and experiences of the cybervetters
For hiring agents, cybervetting consists of searching for information about job applicants on social media sites and via search engines (CareerBuilder, 2018; SHRM, 2016). Among social media, they use LinkedIn most often, followed by Facebook, Twitter, and professional or industry sites (Caers & Castelyns, Reference Caers and Castelyns2011; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; SHRM, 2016). Hiring agents may cybervet at any stage of the hiring process but often do so early on, after job applications are received but before interviews are conducted (Chang & Madera, Reference Chang and Madera2012; Sameen & Cornelius, Reference Sameen and Cornelius2013; SHRM, 2016). Their searches are generally unofficial and casual, as few organizations have any formal cybervetting policies, procedures, or trainings (Caers & Castelyns, Reference Caers and Castelyns2011; Hoek etal., Reference Hoek, O’Kane and McCracken2016; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; SHRM, 2016). HR personnel are less likely to cybervet than recruiters from other professional fields (Berkelaar & Buzzanell, Reference Berkelaar and Buzzanell2015; Gershon, Reference Gershon2017), likely because they have more training and occupational socialization in standard procedures and legal compliance. But why do hiring agents engage in cybervetting at all, and what are their concerns about the practice? Here we examine their subjective perceptions, motives, and doubts, highlighting the ambivalence that surrounds cybervetting even among regular practitioners.
Hiring agents’ motivations for cybervetting
Hiring agents most commonly cite risk management as the reason for cybervetting (e.g., Carr Reference Carr, Landers and Schmidt2016; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). They see this form of screening as a way to minimize uncertainty about candidates, the possibility of making poor hires, and associated fallout such as negligent hiring claims (Carr, Reference Carr, Landers and Schmidt2016; Chauhan etal., Reference Chauhan, Buckley and Harvey2013; Davison etal., Reference Davison, Bing, Kluemper, Roth, Landers and Schmidt2016; Schmidt & O’Connor, Reference Schmidt, O’Connor, Landers and Schmidt2016). Online risk screening takes several forms. Recruiters may search applicants’ LinkedIn profiles to see whether they have mutual connections that can serve as “back door references,” individuals who can comment on candidates without the latter’s knowledge or influence (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, interview notes). They also use LinkedIn to see whether candidates have received any endorsements or recommendations, how many connections they have, or whether they are connected to prominent members of their professional fields (Berkelaar & Buzzanell, Reference Berkelaar and Buzzanell2015; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; Zide etal., Reference Zide, Elman and Shahani-Denning2014). Another common practice is consistency checking or searching to see whether LinkedIn or Google information matches resumes and applications (Hoek etal., Reference Hoek, O’Kane and McCracken2016; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). Among SHRM’s (2016) survey participants, 50% cite the ability to “easily verify information from an applicant’s resume, cover letter, or CV” (p. 20) as a reason for social media screening. Searches for backdoor references and information (in)consistencies arise in part from hiring agents’ mounting distrust for traditional job resumes, which are seen as untrustworthy due to candidate impression management, and formal references from prior employers, who often provide very little information due to libel concerns (Berkelaar, Reference Berkelaar2014).
A third form of risk-management screening is the search for “red flags,” or online traces of poor judgment, unprofessionalism, or potentially destructive workplace behavior—things like posts and pictures depicting alcohol use, overt sexual content, expletives, racism, or badmouthing of employers. Some recruiters claim that red flags do not automatically rule candidates out but instead prompt discussion during interviews (Hedenus & Backman, Reference Hedenus and Backman2017; Hoek etal., Reference Hoek, O’Kane and McCracken2016; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). Still, SHRM (2016) reports that 36% of employer organizations have disqualified candidates due to concerning posts or search results, whereas CareerBuilder (2018) offers a higher estimate of 57%. Numerous studies find that cybervetters tend to weigh negative online content (e.g., posts indicating heavy drinking or self-absorption) more strongly than benign content (e.g., Becton etal., Reference Becton, Walker, Gilstrap and Schwager2019; Zhang etal., Reference Zhang, Van Iddekinge, Arnold, Roth, Lievens, Lanivich and Jordan2020). Common explanations for this pattern, also found in in-person job interviews, include risk management and fundamental cognitive processes (Becton etal., Reference Becton, Walker, Gilstrap and Schwager2019; Chang & Madera, Reference Chang and Madera2012; Tews etal., Reference Tews, Stafford and Kudler2020). Hiring agents rarely check the veracity of online information, negative or positive, via other sources (Berkelaar & Buzzanell, Reference Berkelaar and Buzzanell2015). Even those who are skeptical of risk-management cybervetting may feel pressured to do so. Once enough peers adopt the practice, the perceived costs of not doing it are simply too high (Kuhn, Reference Kuhn2015).
The desire to assess candidates’ “fit” with prospective jobs and employers also motivates hiring agents’ cybervetting practices (Hoek etal., Reference Hoek, O’Kane and McCracken2016; Roulin & Bangerter, Reference Roulin and Bangerter2013; Sameen & Cornelius, Reference Sameen and Cornelius2013). Personnel selection scholarship defines fit as “compatibility between an individual and work environment that occurs when their characteristics are well matched” (Kristof-Brown etal., Reference Kristof-Brown, Zimmerman and Johnson2005, p. 281). It is a dominant organizing concept but also an ambiguous one. Fit can refer to either similarity or complementarity between individuals and their jobs, organizations, work groups, or supervisors, in terms of skills, goals, values, or personality traits and is further complicated by different methods of measurement (Kristof-Brown etal., Reference Kristof-Brown, Zimmerman and Johnson2005). Practitioners also see fit as important but understand it in different ways. Hiring agents speak differently about fit when selecting candidates for different types of jobs and organizations (Berkelaar & Buzzanell, Reference Berkelaar and Buzzanell2015). In addition, hiring agents may emphasize different aspects of fit for different jobs or at different stages of the hiring process (Barrick & Parks-Leduc, Reference Barrick and Parks-Leduc2019). They use a variety of screening devices to assess fit. Personal interviews and telephone screens are dominant, but online screening is also significant.
When cybervetting, some hiring agents clearly focus on what researchers call “person–job” (P–J) fit. For instance, one of our interviewees searched Google to determine engineering candidates’ “job experience and the different roles that they held, the different requirements that they would need in their job” (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, interview notes). This is essentially an assessment of objective job qualifications. However, many hiring agents also look for “culture fit,” a more amorphous and subjective quality, which they variously describe as ability to interact with others, sharing organizational values and goals (e.g., tolerance for diversity), personality and extracurricular activities (“If they’ve got pictures of them with their mom and dad … you just kind of get a feeling that they’re the stablish type of person that we like”), or “professionalism,” often judged by appearance in LinkedIn profile pictures (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, p. 10; Zide etal., Reference Zide, Elman and Shahani-Denning2014). This seems to encompass two categories identified by researchers: person–group (P–G) fit (i.e., getting along with immediate coworkers) and person–organization (P–O) fit (i.e., similarity in the values held by an individual and an employer; Kristof-Brown etal., Reference Kristof-Brown, Zimmerman and Johnson2005). Some hiring agents use Google and social media searches to assess P–J, P–G, and P–O fit at once (Roulin & Bangerter, Reference Roulin and Bangerter2013; Sameen & Cornelius, Reference Sameen and Cornelius2013).
With or without mentioning “fit” specifically, many hiring agents describe cybervetting as a means of getting “more information,” “a sense of,” or “a little insight” about individual job candidates, to gauge “who they really are” or “get a feeling” for the person (Hoek etal., Reference Hoek, O’Kane and McCracken2016; Kotamraju etal., Reference Kotamraju, Allouch, van Wingerden and Katz2014; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, interview notes). As one HR professional put it,
A resume …is the best professional version of you … Facebook is the reality—or Instagram, or whatever—that is the reality of you. My reality is that Iam going to be working with you for hopefully the next five or ten years, so Iwant to know the person, not just the best professional version, but the person. Who am Igoing to be hiring? That’s why Icheck that at all, really, is to find out more about them and what they like to do, and that kind of thing. (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, p. 8)
Of course, some hiring agents recognize that social media profiles are forms of impression management and may not reflect the “real person” in this sense (Hoek etal., Reference Hoek, O’Kane and McCracken2016). Still, SHRM (2016) finds that HR professionals’ most frequent reason for cybervetting is “ability to obtain more information about an applicant than would be provided by just a resume, cover letter or CV” (p. 20). Though it does not correspond to any category of fit in the scholarly literature, hiring agents’ use of online information to construct and evaluate images of “real” candidates can be seen as assessments of impressionistic or “fuzzy” fit.
Risk- and fit-based explanations legitimize cybervetting as a rational, instrumental practice. However, it is also involves less rational motivations. Davison etal. (Reference Davison, Bing, Kluemper, Roth, Landers and Schmidt2016) suggest that hiring agents may search candidates online in part because it is entertaining, and Kotamraju etal.’s (Reference Kotamraju, Allouch, van Wingerden and Katz2014) Netherlands study reports curiosity as a common motive. There is also the role of habit: Hiring agents may cybervet partly because they are accustomed to using social media in their wider personal and professional lives. This is supported by evidence that regular Facebook and LinkedIn users are more likely than others to employ these platforms in recruiting and selection (Nikolaou, Reference Nikolaou2014) and that hiring agents who use LinkedIn regularly are especially likely to trust information found there (Caers & Castelyns, Reference Caers and Castelyns2011). According to Berkelaar (Reference Berkelaar2014), employers and job seekers take it for granted that cybervetting will occur, whether they like it or not.
Hiring agents’ ambivalence toward cybervetting
Although motives for cybervetting range from perceived necessity to sheer curiosity, many hiring agents view the practice with ambivalence. Multiple studies find that about 30% of surveyed hiring agents claim to do no cybervetting at all (CareerBuilder, 2018; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; Sameen & Cornelius, Reference Sameen and Cornelius2013), and one study of HR professionals estimates that as many as 50% purport refraining (SHRM, 2016). Even those who do cybervet often question the quality of the resulting information, citing the possibility that much of it is inaccurate, irrelevant to the job at hand, and/or liable to misinterpretation (Hedenus & Backman, Reference Hedenus and Backman2017; Hoek etal., Reference Hoek, O’Kane and McCracken2016; Kotamraju etal., Reference Kotamraju, Allouch, van Wingerden and Katz2014; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; SHRM, Reference Smith2016). The issue of online impression management by candidates is also subject to varied interpretation. LinkedIn profiles may be seen as accurate reflections of professional accomplishments or as the products of candidates “positioning themselves in the best light and highlighting all the positives, and typically not giving as much history” (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, interview notes). Similarly, LinkedIn’s endorsements and recommendations are useful to some, whereas others do not trust them (“I mean my best friend was a vendor of ours; Icould have her write something fantastic about me”; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, interview notes). Some hiring agents view personal social media (Facebook, Instagram) as reflective of “the real person,” whereas others suggest that candidates can and should edit that reality (“if you have like a glow stick around your head and cocktail in your hand, Imean, you might want to take that down while you’re doing a job search”) (Berkelaar, Reference Berkelaar2014; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021, interview notes). This last point highlights hiring agents’ frequent slippage between three very different approaches to social media information. They take it at face value, question its veracity, and/or insist that candidates engage in artifice so as to display a professional character.
In addition to accuracy, hiring agents may worry about the efficiency of cybervetting. In the past it was assumed that cybervetting occurs because social media and search engines provide easier, cheaper, and more-convenient access to candidate information than traditional hiring tools (Chauhan etal., Reference Chauhan, Buckley and Harvey2013; Davison etal., Reference Davison, Bing, Kluemper, Roth, Landers and Schmidt2016). Today, cybervetting remains convenient, as the barriers to entry are low (Berkelaar, Reference Berkelaar2014). Otherwise, perceptions of its efficiency are mixed. Though 60% of Sameen and Cornelius’s (Reference Sameen and Cornelius2013) survey respondents said cybervetting saves money and time, only 38% associated it with “easy processing of data.” Hoek etal. (Reference Hoek, O’Kane and McCracken2016) likewise found that hiring agents cite excessive time and resource requirements as important reasons for not cybervetting. Perhaps for this reason, reports of screening social media profiles because “it takes little time and effort” decreased from 63% in 2011 to 34% in 2016 (SHRM, Reference Smith2016). The early convenience of cybervetting appears to have decreased over time due to technology churn (Carr, Reference Carr, Landers and Schmidt2016), notably the proliferation of online platforms, features, users, and content (Ajunwa & Greene, Reference Ajunwa, Greene, Vallas and Kovalainen2019).
Hiring agents may also have qualms about the legality and ethics of cybervetting. Concern about legal action focuses mostly on the possibility of discrimination arising from the ease with which candidates’ protected statuses may be observed online (Hoek etal., Reference Hoek, O’Kane and McCracken2016; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; SHRM, Reference Smith2016). Hiring agents question not only the threat of litigation but also broader ethical and practical dilemmas around bias and fairness. For instance, some worry that viewing candidates’ protected statuses early in the hiring process (before face-to-face interviews) could amplify the effects of bias, whereas others argue that cybervetting is fine at any stage because status information emerges prehire anyway (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). Hiring agents also estimate their own ability to avoid discriminating very differently—some express complete confidence, whereas others worry about the effect of subconscious bias (Kotamraju etal., Reference Kotamraju, Allouch, van Wingerden and Katz2014; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021).
Doubts about cybervetting also stem from its potential to violate job applicants’ privacy and personal/professional boundaries (Hoek etal., Reference Hoek, O’Kane and McCracken2016). Given the United States’ weak legislation in this area (Schmidt & O’Connor, Reference Schmidt, O’Connor, Landers and Schmidt2016), HR professionals do not usually see privacy as a source of potential litigation. Instead, they worry about the ethics of “snooping” on candidates’ online profiles and using them to gauge future professional conduct (Becton etal., Reference Becton, Walker, Gilstrap and Schwager2019). However, even as they voice such concerns, hiring agents offer caveats and carve outs that restore cybervetting’s ethical palatability. For instance, some hiring agents place the onus of privacy on individual job seekers, claiming that they waive privacy expectations when they post to social media (Chauhan etal., Reference Chauhan, Buckley and Harvey2013) or that it is up to them to adjust their profiles and privacy settings to suit their own needs (Berkelaar and Buzzanell, Reference Berkelaar and Buzzanell2015; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). Others divide responsibility for privacy between applicants and hiring agents, suggesting that it is acceptable for employers to cybervet if job seekers have given prior consent (Hoek etal., Reference Hoek, O’Kane and McCracken2016) or supplied relevant links in resumes or applications, an increasingly common practice (SHRM, Reference Smith2016). Hiring agents also manage privacy concerns by limiting cybervetting to LinkedIn, seen as a “professional” social networking tool and therefore fair game, but not Facebook, associated with personal life (Caers and Castelyns, Reference Caers and Castelyns2011; Hoek etal., Reference Hoek, O’Kane and McCracken2016; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021).
In summary, although most hiring agents engage in cybervetting, some do so reluctantly and others avoid it outright. We suspect that it is additionally complicated insituations involving time pressure or high-stakes hires and for hiring agents whose roles emphasize procedure and accountability, notably HR professionals. Overall, it appears that for hiring agents, the biggest challenge of cybervetting is ambiguity and ambivalence arising from the uncertain quality of information found online, the unclear legality of seeking it out, and the murky ethics of including it in candidate evaluations.
Organizations: Cybervetting benefits and liabilities
Prior to the internet, organizations screened job candidates by verifying credentials, checking references, and conducting interviews, or they outsourced this work to headhunters or executive search consultants (Finlay & Coverdill, Reference Finlay and Coverdill2007). Today these practices have not gone away (Coverdill & Finlay, Reference Coverdill and Finlay2017), but they are increasingly superseded by extended candidate screening carried out easily via internet tools, within employer organizations. The ability to tap into the vast crowd-sourced landscape of internet data to evaluate job candidates has thrived because it aligns well with the organizational imperative to identify evidence-based solutions (Fourcade & Healy, Reference Fourcade and Healy2017). Cybervetting is different, though, in that it involves not simply the collection and evaluation of more data but a unique form of data. This new form of data offers a chance to reveal insights for improving hiring decisions, but questions about its veracity abound. As noted earlier, many in the HR community want to obtain further information such as social media posts and pictures to reduce hiring uncertainty and claim that they can effectively draw pertinent inferences from these data (Carr, Reference Carr, Landers and Schmidt2016; McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; Zide etal., Reference Zide, Elman and Shahani-Denning2014). Researchers have expressed greater skepticism (Davison etal., Reference Davison, Maraist and Bing2011, Reference Davison, Bing, Kluemper, Roth, Landers and Schmidt2016; Gershon, Reference Gershon2017).
Organizations vary in the extent to which they rely on cybervetting. Previous research shows substantial differentiation in these activities by organizational size, sector, and form. According to SHRM (Reference Smith2016), cybervetting is more common among privately owned, for-profit employers than publicly owned, for-profit or nonprofit employers. Based on our own research (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021), cybervetting tends to be more common among small to medium for-profits and third-party recruiting firms than among large for-profits, nonprofits, and government entities. HR recruiters in government and nonprofit organizations express the most skepticism toward cybervetting. These organizations are more likely to have policies and training materials in place to guide and/or limit these practices. Cybervetting is most prevalent among third-party recruitment and staffing agencies, which rely heavily on gathering online information to screen job candidates prior to putting them forward to the firms with whom they are contracting. For-profit organizations fall in the middle of this continuum. Their HR staff express both enthusiasm and skepticism for cybervetting. They attempt to limit the problematic aspects of cybervetting but rarely have formal policies in place.
Why do we see variation along these lines? Several factors seem to be especially important. First, organizations tend to operate with distinctive goals and motivations depending on sector (Chua, Reference Chua2011; Cobb, Reference Cobb2016). Government and nonprofit organizations express a greater commitment to equity, universalism, and transparency. This sensitizes their HR staff to concerns about bias, discrimination, and privacy. By contrast, for-profit organizations are more committed to efficiency and revenue generation. In these contexts, cybervetting is viewed as a means toward those ends. Second, organizations respond to different institutional pressures across sectors. Legal institutions loom especially large. Government organizations, large for-profit firms, and federal contracting firms are held to the highest standards in terms of employment equity. Regulatory context therefore heightens the risks posed by cybervetting. Third-party contracting agencies are the furthest removed from these risks, as they are consultants to the hiring process rather than final hiring authorities. Finally, the plentitude of information available online poses organizational challenges, but as tools for data access have expanded, so too have tools for data processing, including applicant tracking systems, advanced search functions, and algorithmic data processing (e.g., machine learning). Advanced techniques and software are more accessible for large organizations and for third-party staffing firms that specialize in applicant sourcing and screening. However, organizational capacity has varied implications. Larger and more bureaucratic organizations are also most likely to have policies and regulations governing cybervetting.
Dubious effectiveness and negative effects of cybervetting
Cybervetting is touted as a way to improve hiring outcomes, but whether it actually does so is rarely subject to empirical evaluation. Research on personality assessments of online content offers the clearest insights. Digital footprints are modestly correlated with personality characteristics. Kluemper etal. (Reference Kluemper, Rosen and Mossholder2012) showed that trained human evaluators are capable of developing reasonably reliable estimates of personality characteristics based on social media content. These estimates of specific personality traits are significantly correlated with measures from self-reported personality surveys, though only in the range of about .20 < r < .40 (Kluemper etal., Reference Kluemper, Rosen and Mossholder2012; see Davison etal., Reference Davison, Bing, Kluemper, Roth, Landers and Schmidt2016, for similar estimates). Stoughton etal. (Reference Stoughton, Thompson and Meade2013) obtained self-reported personality estimates from college students, which they found to be correlated with their self-reported negative online behaviors (like posts about substance abuse and badmouthing others). However, personality differences only explained about 7% to 8% of the overall variation in posting behaviors. Moreover, the link between these personality estimates and job performance is much less certain. According to the Kluemper etal. study, the average correlation between other-reported personality scores and job performance one year later ranged .11 < r < .15. In Van Iddekinge etal. (Reference Van Iddekinge, Lanivich, Roth and Junco2016), expert personality assessments of Facebook content offered no significant contributions to the prediction of subject job performance or turnover.
The relatively low correlations among social media content, personality, and job performance address the problems of faulty inferences and overinterpretation of social media data. The quintessential example is the “red cup” photo in which a person who is holding a red Solo-brand cup is often assumed to be an alcohol abuser. We have also observed examples where a Halloween costume gives off the wrong impression about a person’s lifestyle (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). The lack of correspondence between online content and performance could also be due to a lack of relevance. Zide etal. (Reference Zide, Elman and Shahani-Denning2014) report interview responses with HR recruiters that reference an affinity for specific hobbies: “I love skiing. If Isee a candidate belongs to skiing groups or has anything on their profile related to skiing, I’m not going to lie, Iwould be pretty excited” (590). It is not clear how this hobby translates into worker performance for the sales/marketing job that the recruiter typically filled.
Potential for bias in cybervetting is substantial (Ruggs etal., Reference Ruggs, Walker, Blanchard, Gur, Landers and Schmidt2016). In the aforementioned Van Iddekinge etal. (Reference Van Iddekinge, Lanivich, Roth and Junco2016) study, the personality assessments that failed to predict performance indicators instead correlated with race and gender characteristics, revealing a preference for White and female applicants. Audit studies show how even subtle signaling in resumes (based on race, gender, age, social class, and religion) can lead to different applicant evaluations for otherwise identical candidates (e.g., Acquisti & Fong, Reference Acquisti and Fong2015; Bertrand & Mullainathan, Reference Bertrand and Mullainathan2004; Gaddis, Reference Gaddis2017). These types of sociocognitive biases are certain to be apparent as part of cybervetting evaluations (Ruggs etal., Reference Ruggs, Walker, Blanchard, Gur, Landers and Schmidt2016). Our own research (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021) shows that biased evaluations of job candidates as part of cybervetting are often justified by the desire to assess “fit.” The signals that HR staff typically use to make that determination are filtered through a culturally and cognitively biased lens. Examples of ideal candidates who displayed active lifestyles (hiking, camping, skiing, and going to a ball game) reflect an age, race, and class-specific habitus—that is, young, White, and upper middle class (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021; Zide etal., Reference Zide, Elman and Shahani-Denning2014).
Screening on these types of signals biases evaluations toward dominant social groups and can lead to the homogenization of an organization’s workforce. Previous research demonstrates that a lack of diverse workplace relationships can be detrimental to creativity, adaptability, and innovation (DiTomaso etal., Reference DiTomaso, Post and Parks-Yancy2007; Reagans & Zuckerman, Reference Reagans and Zuckerman2001; Reagans etal., Reference Reagans, Zuckerman and McEvily2004). Workforce diversity has also been linked to increased sales, market share, and profits (Herring, Reference Herring2009; but see Stojmenovska etal., Reference Stojmenovska, Bol and Leopold2017). Consequently, although cybervetting is often promoted as a means of improving individual hires, its effect on aggregate organizational hiring may be less salutary. Beyond organizational interests, cybervetting has the potential to undermine the broader goal of equal employment opportunity. Many cybervetting strategies contribute to the bifurcation of the workforce into “haves” and “have nots,” in ways that fail to align with meritocratic ideals (McDonald etal., Reference McDonald, Damarin, Lawhorne, Wilcox, Vallas and Kovalainen2019).
Organizations must also grapple with the fact that cybervetting violates applicants’ and employees’ beliefs about privacy and procedural justice (McDonald etal., Reference McDonald, Thompson and O’Connor2016; Stoughton, Reference Stoughton, Landers and Schmidt2016). When applicants learn that their online social media has been screened, it significantly reduces their attraction to an organization, increases feelings of privacy invasion, and increases litigation intentions (Stoughton etal., Reference Stoughton, Thompson and Meade2015). These findings are consistent with other research showing that perceived procedural justice tends to be positively correlated with organizational attraction (Bauer etal., Reference Bauer, Truxillo, Tucker, Weathers, Bertolino, Erdogan and Campion2006; Madera, Reference Madera2012), willingness to reapply to jobs within the organization, and recommendations of the organization to others (Konradt etal., Reference Konradt, Warszta and Ellwart2013). Alack of perceived procedural justice is associated with intentions to withdraw, as well as actual withdrawal, from the hiring process (Griepentrog etal., Reference Griepentrog, Harold, Holtz, Klimoski and Marsh2012; Suen, Reference Suen2018). This reveals a central paradox of cybervetting: although the practice is often viewed as a means of reducing risk, organizations take on additional risks by engaging in it.
Minimizing the consequences of cybervetting
Given the potential negative outcomes of cybervetting for job candidates, the ambivalence toward cybervetting felt by hiring agents, and the oft-downplayed complications of cybervetting for organizations, we now consider how each stakeholder can improve existing cybervetting practices and outcomes. We also consider how government and professional associations may help to regulate cybervetting. We summarize the following recommendations and other important aspects of our argument in Table 1.
Table 1. Primary Considerations
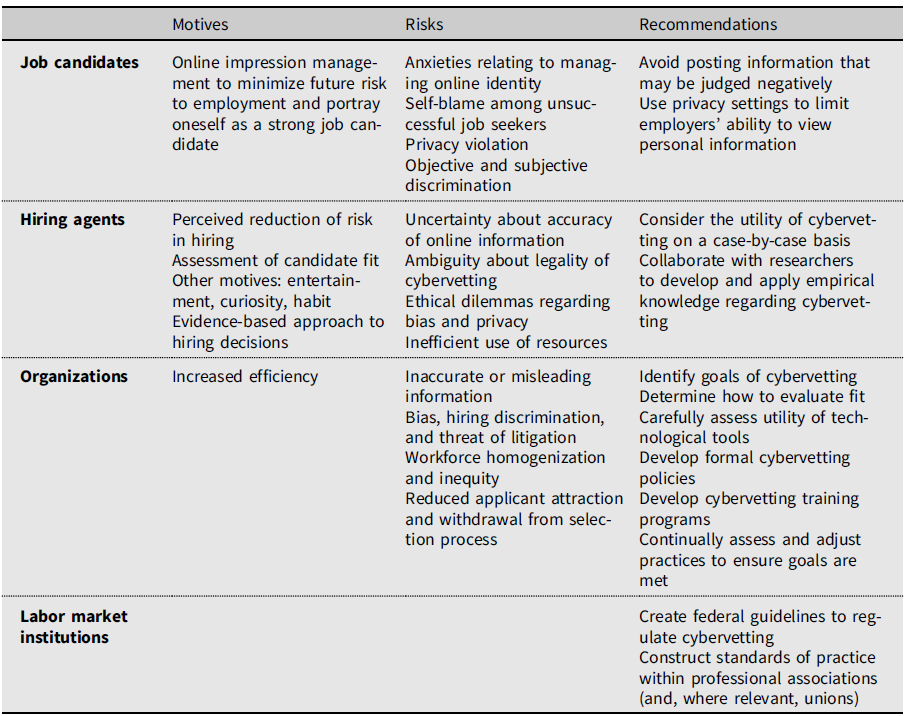
As job candidates have little power over or say in employers’ cybervetting practices, monitoring online social media posts in order to conform to the new norm of cybervetting is a central concern (Black etal., Reference Black, Stone and Johnson2015; Roulin, Reference Roulin2014; Zhang etal., Reference Zhang, Van Iddekinge, Arnold, Roth, Lievens, Lanivich and Jordan2020). Job candidates should remove and avoid posting any information that potential employers might evaluate negatively (Roulin & Levashina, Reference Roulin, Levashina, Landers and Schmidt2016) including any information regarding any religious affiliation, sexual behavior, alcohol or drug use, profanity or violence, illegal activity, or negative attitudes regarding work (Zhang etal., Reference Zhang, Van Iddekinge, Arnold, Roth, Lievens, Lanivich and Jordan2020). They may also consider using privacy settings on social media websites to limit the information that potential employers can access online (Black etal., Reference Black, Stone and Johnson2015; Zhang etal., Reference Zhang, Van Iddekinge, Arnold, Roth, Lievens, Lanivich and Jordan2020). Although these are realistic recommendations, we are also aware that they are problematic because they reinforce the expectation that the onus for managing online employment security is on job candidates rather than employers. Therefore, we stress the responsibility of hiring agents and organizations to reshape cybervetting practices instead.
Hiring agents typically make cybervetting decisions with little organizational guidance. Afew considerations can help minimize the negative consequences of the practice. First, instead of cybervetting out of habit or curiosity, hiring agents should subject the practice to more careful consideration. For instance, given that hiring agents expect candidates to manage impressions online, can social media profiles, posts, and photos still be taken as face-value indicators of “real” personalities or qualifications? What is the goal of seeking a “sense” of the “whole person”? Is this a valid, relevant, and justifiable hiring criterion? To what aspect of job performance is it connected? These questions should be answered not only in general but also with consideration of the roles, skills, and organizational levels of specific hires (Davison etal., Reference Davison, Bing, Kluemper, Roth, Landers and Schmidt2016; Hoek etal., Reference Hoek, O’Kane and McCracken2016), as cybervetting may have value in some cases but little in others (Chang & Madera, Reference Chang and Madera2012; Weidner etal., Reference Weidner, O’Brien, Wynne, Landers and Schmidt2016). Furthermore, hiring agents in the HR field can engage with their profession to ensure that cybervetting practices are grounded in solid evidence. At the moment, the gap between practitioners’ casual approach to online screening and the decidedly mixed reviews it receives in the scholarly literature (e.g., Carr, Reference Carr, Landers and Schmidt2016; Chauhan etal., Reference Chauhan, Buckley and Harvey2013; Davison etal., Reference Davison, Bing, Kluemper, Roth, Landers and Schmidt2016; Schmidt and O’Connor, Reference Schmidt, O’Connor, Landers and Schmidt2016; Tews etal., Reference Tews, Stafford and Kudler2020) is rather stark. Closing this gap requires collaboration, with researchers becoming more engaged with the problems and realities faced by hiring agents, and hiring agents becoming more attuned to mounting scholarship on the validity of online information, its influence on bias, and the legality of cybervetting, among other important concerns (Tkachenko etal., Reference Tkachenko, Hahn and Peterson2017).
Organizational leaders should reconsider the potential value of cybervetting relative to the many costs it imposes. In most instances, it is advisable to avoid these practices altogether and instead rely on other formalized procedures for recruiting, screening, and hiring new employees. However, it is unreasonable to expect all firms to adopt this position. If cybervetting must be done, we encourage organizations to consider the following recommendations. First, organizational leaders and hiring agents should collectively develop a clear set of goals defining what they want to accomplish through cybervetting and what means are most appropriate for doing so. Organizational actors should consider what risks they are most concerned about and what cybervetting does to aid that risk assessment. For example, a history of criminal activity is a reasonable concern for an employer to have, but this risk might be better assessed through criminal background checks. Concerns about how a new hire might interact with clients or customers might be better addressed through reference checks or vignette-style questions as part of the interview process. To the extent that cybervetting may be helpful in assessing risks, hiring agents should contemplate how they can do so accurately and which signals of risk are most important to evaluate or emphasize.
Likewise, organizational actors should come to a collective decision on how to evaluate fit. We encourage organizational actors to focus exclusively on P–J fit, assessed via concrete employment qualifications and/or knowledge, skills, and abilities. Research is far less clear about the benefits of P–O fit assessments, particularly as used in hiring.Footnote 4 We strongly encourage employers to avoid assessments of organizational fit and what hiring agents call “culture fit,” as well as impressionistic “fuzzy” fit, in cybervetting and throughout the hiring process in general. Hiring on P–O and cultural fit is linked to race, gender, and other forms of bias, which may lead recruiters to select based on similarity to self (Kristof-Brown etal., Reference Kristof-Brown, Zimmerman and Johnson2005; Rivera, Reference Rivera2015), to assess different forms of fit for applicants of different ethnicities (Wolgast etal., Reference Wolgast, Björklund and Bäckström2018), and to accommodate coworker prejudices, even against their own beliefs and group identities (Vial etal., Reference Vial, Brescoll and Dovidio2019). Emphasizing these forms of fit in hiring could lead to suboptimal candidate selections, increase organizations’ exposure to litigation, and promote innovation-stifling “group think” (Kristof-Brown etal., Reference Kristof-Brown, Zimmerman and Johnson2005).
In identifying what they would like to accomplish through cybervetting, organizational actors might also evaluate alternative technologies that could be used as part of this practice. In addition to human evaluators, researchers have attempted to use word counts (Alsadhan & Skillicorn, Reference Alsadhan and Skillicorn2017) and machine learning algorithms (Philip etal., Reference Philip, Shah, Nayak, Patel, Devashrayee, Balas, Sharma and Chakrabarti2019) to measure personality traits from large amounts of social media data. Hiring organizations are able to contract with consulting firms to use these techniques to obtain personality profiles on their applicants. However, skepticism is warranted when considering these technologies, as their veracity with respect to performance outcomes—much like human coding of online signals—has yet to be demonstrated. Furthermore, automated evaluations of this sort are not bias free. The mathematical models that underlie quantitative decision making tend to be opaque and rely on proxies that are not causally related to behavioral outcomes (O’Neil, Reference O’Neil2016). They are often based on stereotypical assumptions that are particularly damaging to members of disadvantaged communities. In hiring, algorithmic tools are often based on biased assumptions about “fit,” which can reproduce rather than ameliorate discriminatory outcomes (Ajunwa and Greene Reference Ajunwa, Greene, Vallas and Kovalainen2019).
After clearly defining the goals of cybervetting, organizational actors, and particularly HR professionals who are responsible for hiring procedures, should develop formal policies outlining acceptable cybervetting practices—policies that are currently lacking in over 60% of employer organizations (SHRM, Reference Smith2016). Such policies should detail who will be cybervetting, what online sources of information will be used, what signals will be evaluated, when this activity will occur,Footnote 5 and for which portion of the applicant pool. To ensure that managers follow new formal policies, research suggests engaging managers in goal-oriented projects and increasing the transparency of their efforts rather than attempting to regulate their behavior and limit their autonomy, which often provokes resistance and ultimately backfires (Dobbin etal., Reference Dobbin, Schrage and Kalev2015). Therefore, organizational actors working to implement these new policies might reduce problematic cybervetting activities by engaging managers and other actors in discussing principles and establishing cybervetting practices appropriate to the employer and to local departments or teams.
Organizations should also develop training programs focused on appropriate cybervetting practices and integrate this training into the onboarding process for new hiring agents. Formal training programs are rare: In our study of nearly 60 different employers in the Raleigh and Atlanta metro areas, only a single organization that had explicit training materials (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). Cybervetting training should reflect previously discussed concerns such as which types of risk and/or fit should be the core evaluative focus, which positions hiring agents should cybervet for, and so forth in order to socialize new hiring agents into organizational norms and expectations. Such training and its focus would necessarily vary across organizations and specific roles.
Finally, in adopting and maintaining these practices, organizations must continuously assess the extent to which cybervetting goals have been met and adjust their practices as needed. Clark and Roberts (Reference Clark and Roberts2010) have argued that if organizations want to use cybervetting, they need to demonstrate an empirical link between those practices and outcomes of interest. We agree that maintaining reflexivity through an explicit emphasis on evaluation and assessment is critical. To what extent are cybervetting practices generating added value to hiring decisions over and above traditional screening procedures? What information sources and signals correlate with turnover and worker performance? To what extent does cybervetting contribute to the homogenization or diversification of the workforce? Although addressing these questions would require resources, it would help to mitigate significant liabilities brought on by unreflective engagement in cybervetting. Moreover, university researchers are interested in answering these questions, too, and would be happy to partner with organizations at very low cost to assist with these assessments.
Beyond these organizational decisions, we can consider a broader set of strategies for ensuring fair and equitable application of cybervetting. First, greater federal guidance is needed to clarify the conditions under which cybervetting is an acceptable tool. The Equal Employment Opportunity Commission (EEOC) states that selection procedures cannot intentionally discriminate, must be job related and job appropriate, and that procedures with the lowest likelihood of screening out protected groups are preferred (U.S. Equal Employment Opportunity Commission, 2007). Although they have held hearings on the use of online data as part of recruitment and screening practices (U.S. Equal Employment Opportunity Commission, 2016), they offer no official guidance or policy statements on cybervetting per se.Footnote 6 We think some formal guidance would be helpful in order to clarify which types of cybervetting practices are most problematic and help steer those organizations that choose to engage in cybervetting toward better practices. Federal and state legislatures could also intervene by setting explicit guidelines for employers to follow. Although there are no federal statutes to prevent employers from reviewing social media information of applicants, 20 states have laws that prevent employers from requiring passwords to social media accounts (Schmidt & O’Connor, Reference Schmidt, O’Connor, Landers and Schmidt2016). States could also extend privacy protections to a larger range of online content. In most states, information on social media websites is considered to be public even if privacy controls are applied (Schmidt & O’Connor, Reference Schmidt, O’Connor, Landers and Schmidt2016).
Standards of practice should also be developed separately within industries. Professional associations could publish standards that clarify whether cybervetting is permissible when hiring individuals who engage in their specific type of work. If it is deemed permissible, those standards could point to specific sources of online data that may be evaluated and what type of conduct may be assessed. This could help provide greater clarity to workers and employers as to how and what online content is to be assessed. We found in our research that third-party staffing and consulting agencies tended to be most enthusiastic about cybervetting while also providing the fewest restrictions on its practice (McDonald etal., Reference McDonald, Damarin, McQueen and Grether2021). Therefore, standards of practice would be most helpful for organizations involved in this work. They should develop a clear set of procedures with respect to how online information will be used as part of applicant screening and sharing that document with the hiring organizations with which they contract. Organizations that contract with third party hiring consultants should require this information as well.
Conclusion
Cybervetting is rapidly becoming a widespread practice (SHRM, 2013, Reference Smith2016), which has serious implications for job candidates, hiring agents, and organizations. As new technologies that offer employers greater online access to job candidates’ information arise, probing the challenges and limitations of cybervetting will become even more important. Employers must be mindful of their practices and consider whether it is possible to avoid cybervetting. If cybervetting is necessary, employers must develop formal cybervetting policies and training programs and continuously evaluate cybervetting practices to ensure their goal directedness. Professional associations and government must also take action to hold organizations accountable for “better practices” for cybervetting. We encourage organizational leaders to be transparent about how they are doing this work and to share their data so that more can be learned about the benefits, costs, and consequences of online screening.
For now, cybervetting is typically a routine, unreflective activity undertaken by individual hiring agents within organizations that alternately ignore or encourage it. This casual approach at the microlevel of everyday practice belies the serious repercussions that emerge from its widespread use. The best argument for cybervetting is that it can improve the quality of individual hires. But this is untested; it is equally possible that cybervetting produces idiosyncratic, uneven, and false information, leading to suboptimal choices. For individual employers and employees, the result of cybervetting is disaffection and turnover. For the economy as a whole, this translates to dampened productivity. Moreover, cybervetting can also facilitate both conscious and tacit discrimination based on protected (e.g., race) or unprotected (e.g., physical appearance) statuses. Organizations may miss out on talent, become less diverse and innovative, and run the risk of litigation as individual job seekers face reduced employment options.
Perhaps the most insidious implications of cybervetting stem from its ethical deficiencies. Cybervetting has the potential to substantially undermine equal opportunity in hiring, exacerbating the already gaping income and racial inequalities that have recently been exposed anew by the ravages of COVID-19 and institutionally racist violence. As a form of surveillance that erodes personal/professional boundaries, cybervetting also promotes privacy invasion. Among individuals, this encourages constant impression management, self-censorship, and anxiety. For organizations, it contributes to employee distrust. At the societal level, it limits freedom of expression and curtails open discussion of public issues.
We worry that organizational leaders have not fully considered these implications. For example, in testimony to the EEOC, industry experts in the area of algorithmic cybervetting admitted that the companies using it rarely considered implications beyond efficiency and return on investment: “Around the diversity question …, that’s something that we weren’t often asked to speak to…. Very few asked us, is this also promoting diversity?” (U.S. Equal Employment Opportunity Commission, 2016). If online screening continues to proceed uncritically, then we must reject it. Extensive transformation of cybervetting could lead to progress, but only if organizational leaders and hiring agents commit to asking difficult questions about its value.





