A Introduction
Information has always been a valuable as well as often sensitive asset for companies, states and citizens. In this sense, the link between data flowing across borders and the need to protect certain national interests is not entirely new and has been made before.Footnote 1 In particular during the late 1970s and the 1980s, as satellites, computers and software were profoundly changing the dynamics of communications, the trade-offs between allowing data to flow freely and asserting national jurisdiction became apparent. Echoing concerns of large multinational companies, some states worried that barriers to information flows might hinder economic activities and looked for mechanisms that could prevent the erection of such barriers. Non-binding solutions were found under the auspices of the Organisation for Economic Co-operation and Development (OECD) in the form of principles that sought to balance the free flow of data with the national interests in the fields of privacy and security.Footnote 2 Yet, as the OECD itself points out, while this privacy framework endured, the situation then was profoundly different from the challenges in the realm of data governance we face today.Footnote 3 Ubiquitous digitization and the societal embeddedness of digital media have changed the volume, the intensity and, indeed, the nature of data flows.Footnote 4
The value of data, as well as the risks associated with data collection, data processing, data use and reuse, by both companies and governments, has dramatically changed. Beyond the flawed mantra of data being the ‘new oil’,Footnote 5 many studies point at the vast potential of data as a trigger for more efficient business operations, highly innovative solutions and better policy choices in all areas of societal life.Footnote 6 This transformative potential refers notably not only to ‘digital native’ areas, such as search or social networking, but also to brick-and-mortar or physical businesses, such as in manufacturing or logistics.Footnote 7 Overall, the implications of big data availability and analytics are multiple and some of them far reaching.Footnote 8
Recent enquiries have shown that not only the sheer amount of data and our dependence on it have exponentially increased but also the ways governments assert control over global data flows have changed.Footnote 9 Exerting jurisdiction over online matters beyond borders, as exemplified by the seminal French judgment in the Yahoo! case,Footnote 10 or Internet censorship, as practised by China and many other states,Footnote 11 are well-known examples of control. Yet, the new generation of Internet controls seeks to keep information from going out of a country, rather than stopping it from entering the sovereign state space. Governments increasingly ‘localize’ the data within their jurisdictions for a variety of reasons.Footnote 12 To be sure, this kind of erecting barriers to data flows impinges directly on trade and may endanger the realization of an innovative data economy. The provision of any digital products and services, cloud computing applications or, if we think in more future-oriented terms, the Internet of Things (IoT) and artificial intelligence (AI), would not function under restrictions on the cross-border flow of data.Footnote 13 Data protectionism also comes at a certain cost for the countries adopting such measures.Footnote 14
At the same time, while it may often be true that higher levels of data protection will amount to a trade barrier, one cannot disregard the legitimate desire of countries to safeguard the fundamental rights of their citizens, public interests and values that matter for their constituencies. The impact of data collection and data use upon privacy protection in particular has been, in recent years, widely acknowledged by scholars and policymakers alike, as well as felt on the ground by regular users of digital products and services.Footnote 15 The risks have only been augmented in the era of big data, which presents certain distinct challenges to the protection of personal data and, by extension, to the protection of personal and family life.Footnote 16 Indeed, big data puts into question the very distinction between personal and non-personal data. On the one hand, it appears that one of the basic tools of data protection – that of anonymization, i.e. the process of removing identifiers to create anonymized datasets – is only of limited utility in a data-driven world, as in reality it is now rare for data generated by user activity to be completely and irreversibly anonymized.Footnote 17 On the other hand, big data enables the reidentification of data subjects by using and combining datasets of non-personal data, especially as data is persistent and can be retained indefinitely with the presently available technologies.Footnote 18
Big data also puts into question the fundamental elements of existing privacy protection laws, which often operate upon requirements of transparency and user’s consent.Footnote 19 Equally is data minimization as another core idea of privacy protection challenged, as firms are ‘hungry’ to get hold of more and more data.Footnote 20 These challenges have not been left unnoticed and have triggered the reform of data protection laws around the world, best exemplified by the European Union’s General Data Protection Regulation (GDPR).Footnote 21 The reform initiatives are, however, not coherent and are culturally and socially embedded, reflecting societies’ deep understandings of constitutional values, relationships between citizens and the state, and the role of the market, to name but a few.Footnote 22 The striking divergences both in the perceptions and the regulation of privacy protection across nations and in particular between the fundamental rights approach of the EU and the more market-based, non-interventionist approach of the United StatesFootnote 23 have also meant that conventional forms of international cooperation and an agreement on shared standards of data protection have become highly unlikely.
Against this backdrop of a complex and contentious regulatory environment, data and cross-border data flows in particular have become one of the relatively new topics in global trade law discussions. Many questions have been raised in this context, for instance, whether and how do the existing trade rules apply to data flows? How should they be classified – as a good or a service, and if categorized as a service, under which services sector do they fall? How do we address new trade barriers, such as localization measures? How can we reconcile the free flow of data and countries’ privacy, national security and other public interest concerns? How do we ensure that trade law accommodates the data-driven economy and enables global trade for the benefit of all? Which are the appropriate forum and the decision-making processes for moving the global data economy agenda ahead? Many of these questions are still open and this chapter will not give satisfactory answers to them all. It will nonetheless provide valuable information and insights about the current state of global trade law that may help policymakers down the road. In this sense, the chapter has a two-prong objective: first, it seeks to clarify the interfaces between the data-driven economy and existing trade law; second, and more importantly, it traces the regulatory responses and the emerging legal design in preferential trade agreements (PTAs) with regard to digital trade and data flows in particular.
B WTO Law as Pre-Internet Law
While PTAs are in the spotlight of this chapter, the multilateral forum of the World Trade Organization (WTO) cannot be simply ignored – on the one hand, because it matters in its own right as a set of hard and enforceable rules on trade in goods, services and intellectual property (IP) protection, and on the other hand, because PTAs are in many senses only an addition to these rules. Politically speaking, the failings of the multilateral system on certain issues have prompted action on those issues in the preferential venues and this is particularly evident in the area of digital trade, as revealed later.
The WTO agreements, the fundamental basis of international trade law, were adopted during the Uruguay Round (1986–1994) and came into force in 1995.Footnote 24 Despite some adjustments – such as Information Technology Agreement (ITA),Footnote 25 its update in 2015 and the Trade Facilitation Agreement,Footnote 26 WTO law has not fundamentally changed and is still very much in its pre-Internet state.Footnote 27 One could, of course, argue that laws need not change with each and every new technological invention.Footnote 28 And indeed, the law of the WTO lends credence to such an argument because it is in many aspects, both in the substance and in the procedure, flexible and resilient. WTO law can be qualified as relatively ‘hard’, as it involves deep intervention in domestic regulatory regimes and can impose certain sanctions for breach of obligations.Footnote 29 It is furthermore based on powerful principles of non-discrimination, such as the most-favoured nation (MFN) and the national treatment (NT) obligations, that address all areas of economic life and could potentially tackle technological developments better than new made-to-measure regulatory acts. Many of the rules with regard to the application of the basic principles, with regard to standards, trade facilitation, subsidies and government procurement do also operate in a technologically neutral way.Footnote 30
Another advantage of WTO law that may be highlighted is that despite its high degree of legalization and focus on economic rules, it also permits some flexibilities. One of those relates to the so-called general exceptions clauses formulated under Article XX of the General Agreement on Tariffs and Trade (GATT) 1994 and Article XIV of the General Agreement on Trade in Services (GATS), which allow WTO members to adopt measures that would otherwise violate their obligations and undertaken commitments, under the condition that these measures are not be applied in a manner that would constitute a means of arbitrary or unjustifiable discrimination between countries where like conditions prevail, or a disguised restriction on trade. Particularly interesting for this chapter’s discussion on data flows are the possibilities that Article XIV of the GATS may open for maintaining existing and adopting new data restrictions. Article XIV enumerates different grounds as possible justifications and includes two specific categories that are of pertinence for our topic: (a) those relating to public order or public moralsFootnote 31 and (b) those that are necessary to secure compliance with laws or regulations,Footnote 32 including such on ‘the protection of the privacy of individuals in relation to the processing and dissemination of personal data and the protection of confidentiality of individual records and accounts’.Footnote 33 Under this provision, it has been argued, for instance, that the rules of the GDPR may be found to violate the obligations of the EU under the GATS.Footnote 34
Finally, in terms of evolution of norms, it can be maintained that the WTO possesses the advantage of a dispute settlement system that can foster legal evolution.Footnote 35 There is strong evidence in the WTO jurisprudence for both the capacity of the dispute settlement mechanism and for the relevance of the Internet in trade conflicts.Footnote 36 The US–GamblingFootnote 37 case is a great example in this context, as it confirmed that the GATS commitments apply to electronically supplied services and clarified key notions of services regulation, such as likeness and the scope of the ‘public morals/public order’ defence under Article XIV of the GATS.Footnote 38
Yet, plainly assuming that the WTO’s ‘adaptive governance’Footnote 39 works will be flawed. Indeed, there are many reasons to question it and be rather sceptic about the match between the existing WTO rules, their implementation and evolution, and contemporary digital trade. Apart from the current political context, which may prevent new and forward-looking rule-making,Footnote 40 there are important hindrances in applying the GATS in the digital environment. In particular, the GATS commitments are based upon old pre-Internet classifications of services and sectors, and these have become increasingly disconnected from trade practices.Footnote 41 For instance, as the WTO law presently stands, it is unclear whether previously unknown things, such as online games, should be categorized as goods or services (and thus whether the more binding GATT or the GATS apply). Provided that no physical medium is involved and one decides consequently to apply the GATS, the classification puzzle is by no means solved: Online games, for instance, as a new type of content platform, could be potentially fitted into the discrete categories of computer and related services, value-added telecommunications services, entertainment or audiovisual services. One may also be unsure when there is an electronic data flow intrinsic to the service whether to classify this flow separately or as part of the traditional services.Footnote 42 Classification is by no means trivial,Footnote 43 as each category implies a completely different set of duties and/or flexibilities for the WTO members. If online platforms and the services they offer were to be classified as computer services, for example, states would lack any wiggle-room whatsoever and would have to grant full access to foreign services and services suppliers and treat them as they treat domestic ones – because of the high level of existing commitments under the GATS of virtually all WTO members.Footnote 44 On the other hand, were online games classified as audiovisual services, most WTO members would have the policy space to maintain and adopt restrictive and discriminatory measures.Footnote 45 The evolutionary interpretation of schedules of specific commitments, as affirmed in China–Audiovisual Products, while a positive development, does not necessarily help much to achieve legal certainty in such situations.Footnote 46 Neither does the finding that the GATT and the GATS are not mutually exclusive.Footnote 47
The classification dilemma, as particularly critical for digital trade, is an illuminating example of this state of paralysis but by far not the only one. Many other issues, although discussed in the framework of the 1998 WTO Work Programme on Electronic Commerce, have been left without a solution or even a clarification.Footnote 48 For instance and as a minimum for advancing on the digital trade agenda, there is still no agreement on a permanent moratorium on customs duties on electronic transmissions and their content.Footnote 49 Against the backdrop of pre-Internet WTO law and despite the recent reinvigoration of the e-commerce negotiations under the 2019 Joint Statement Initiative,Footnote 50 many of the disruptive changes underpinning the data-driven economy have demanded regulatory solutions outside the ailing multilateral trade forum. States around the world have used in particular the venue of preferential trade agreements to fill in some of the gaps of the WTO framework, clarify its applications and beyond that, address the newer trade barriers and accommodate their striving for seamless digital trade. Quite naturally for developments in preferential trade, the framework that has emerged as a result and now regulates contemporary digital trade is not coherent. It is neither evenly spread across different countries, nor otherwise coordinated. Indeed, it is messy and fragmented both with regard to the substantive rules and the agreements’ membership.
In the following section, the chapter provides an overview of the developments in PTAs in the last two decades in the area of digital trade governance. The information stems from our own dataset TAPED: Trade Agreement Provisions on Electronic Commerce and Data,Footnote 51 which ran a detailed mapping and coding of all PTAs that include chapters, provisions, annexes or side documents that directly or indirectly regulate digital trade. In the subsequent section, we look at the new rules on free data flows and their design across different PTAs. We then analyze in more detail the most sophisticated template for digital trade rules that we have so far – that of the Comprehensive and Progressive Agreement for Trans-Pacific Partnership (CPTPP) and some subsequent developments in the United States–Mexico–Canada Agreement (USMCA). In the final section, the chapter offers some thoughts about the current state of global digital trade law and the prospects of governing data flows.
C Evolution of Digital Trade Provisions in PTAs
I Overview and Some Emerging Trends
From the 347 PTAs agreed upon between 2000 and 2019 and reviewed in TAPED, 184 PTAs have provisions related to digital trade.Footnote 52 The largest number of provisions is found in e-commerce and intellectual property chapters; overall, the provisions remain however highly heterogeneous, addressing various issues ranging from customs duties and paperless trading to personal data protection and cybersecurity. The depth of the commitments and the extent of their binding nature can also vary significantly. For instance, if one looks at the top countries that have entered into PTAs with e-commerce provisions,Footnote 53 the European Union occupies the first place with Singapore, yet it is only in the very recent EU PTAsFootnote 54 that there is a dedicated chapter on e-commerce and some substantive provisions – beforehand e-commerce provisions were only few, part of the services chapters and limited to mere GATS-level commitments and cooperation pledges.Footnote 55
Putting the digital trade provisions along a chronological line, it is evident that the inclusion of provisions in PTAs referring explicitly to electronic commerce is not a recent phenomenon, although it has evolved significantly in the past eighteen years. The first e-commerce provision dates back to the 2000 Free Trade Agreement (FTA) between Jordan and the United States.Footnote 56 Almost at the same time, New Zealand and Singapore agreed upon the Closer Economic Partnership Agreement (CEPA), including an article on paperless trading. Two years later, the Australia–Singapore FTA (SAFTA), concluded on 17 February 2003, was the first PTA to have a dedicated chapter on e-commerce. At the moment of this writing, specific provisions applicable to e-commerce can be found in 109 PTAs, mostly in dedicated chapters (79) (for details, see Table 1.1). The last eight years have witnessed a significant increase in the number of agreements with digital trade provisions. As shown in Figure 1.1, digital trade provisions are, on average, included in more than 68 per cent of all PTAs that were concluded between 2010 and 2019 and despite the fall in agreed upon deals, more of them include digital trade provisions. The rise in the total number of PTAs with such norms is driven mainly by bilateral PTAs: 84 per cent of total PTAs since 2000 and involves both developed and developing countries.Footnote 57
Table 1.1. PTAs concluded with digital trade provisions per year (2000–2019)
| Year | Total PTAs | WTO notified | Digital trade provisions | E-commerce chapters | % PTAs with digital trade provisions |
|---|---|---|---|---|---|
| 2000 | 20 | 8 | 2 | 0 | 10.00 |
| 2001 | 23 | 12 | 2 | 0 | 8.70 |
| 2002 | 26 | 8 | 4 | 0 | 16.00 |
| 2003 | 30 | 10 | 6 | 3 | 20.69 |
| 2004 | 29 | 14 | 6 | 6 | 21.43 |
| 2005 | 17 | 10 | 5 | 4 | 33.33 |
| 2006 | 26 | 13 | 7 | 6 | 31.82 |
| 2007 | 20 | 13 | 4 | 4 | 29.41 |
| 2008 | 24 | 27 | 9 | 6 | 40.91 |
| 2009 | 23 | 21 | 6 | 3 | 19.05 |
| 2010 | 14 | 18 | 5 | 3 | 50.00 |
| 2011 | 19 | 15 | 2 | 2 | 18.75 |
| 2012 | 8 | 20 | 3 | 3 | 33.33 |
| 2013 | 14 | 22 | 9 | 6 | 64.29 |
| 2014 | 14 | 12 | 10 | 7 | 88.89 |
| 2015 | 10 | 10 | 6 | 5 | 50.00 |
| 2016 | 11 | 14 | 7 | 5 | 71.43 |
| 2017 | 6 | 18 | 3 | 2 | 33.33 |
| 2018 | 9 | 7 | 9 | 10 | 100.00 |
| 2019 | 4 | 0 | 4 | 4 | 100.00 |
| Total | 347 | 272 | 109 | 79 |

Figure 1.1. Evolution of PTAs with digital trade provisions (2000–2019)
Among the PTAs with digital trade provisions, it is evident that the number and level of detail have also increased significantly over the years, as depicted in Figure 1.2. In 2019, 13 is the average number of provisions found in e-commerce chapters of PTAs, with an average number of 2,527 words (see Table 1.2).

Figure 1.2. PTAs with digital trade provisions: average number of articles and words
Table 1.2. PTAs with e-commerce chapters: average number of provisions and words (2000–2019)
| Year | Total PTAs | E-commerce chapters | Average number of articles | Average number of words |
|---|---|---|---|---|
| 2000 | 20 | 2 | 1 | 91 |
| 2001 | 23 | 2 | 1 | 838 |
| 2002 | 25 | 4 | 4 | 168 |
| 2003 | 29 | 6 | 8 | 395 |
| 2004 | 28 | 6 | 6 | 606 |
| 2005 | 15 | 5 | 5 | 541 |
| 2006 | 22 | 7 | 6 | 801 |
| 2007 | 17 | 5 | 7 | 753 |
| 2008 | 22 | 9 | 7 | 606 |
| 2009 | 21 | 4 | 5 | 606 |
| 2010 | 10 | 5 | 3 | 313 |
| 2011 | 16 | 3 | 3 | 318 |
| 2012 | 9 | 3 | 3 | 233 |
| 2013 | 14 | 9 | 7 | 640 |
| 2014 | 9 | 8 | 8 | 1,073 |
| 2015 | 10 | 5 | 8 | 842 |
| 2016 | 7 | 5 | 10 | 1,390 |
| 2017 | 6 | 2 | 2 | 357 |
| 2018 | 10 | 10 | 12 | 1,697 |
| 2019 | 4 | 4 | 13 | 2,527 |
At the moment of writing, the Singapore–Australia Free Trade Agreement (SAFTA), updated in 2016, is the PTA in force with the highest number of provisions in an e-commerce chapter (19 in total), with 2,997 words. As of 2020, the USMCA would overtake SAFTA, as the current text of its Digital Trade chapter has also 19 articles but comprising 3,206 words. The new dedicated digital trade agreements go well beyond: the US–Japan Digital Trade Agreement has 5,346 words, and the Digital Economy Partnership Agreement (DEPA) between Chile, Singapore and New Zealand contains 10,887 words.
II Overview of Data-Related Rules in PTAs
One can in general speak of the relevance of trade rules for data and data flows, as they matter for data in at least three ways: (i) because they regulate the cross-border flow of data by regulating trade in goods and services as well as the protection of intellectual property; (ii) because they may install certain beyond the border rules that demand changes in domestic regulation – for example, with regard to procedures with electronic signatures or data protection; and (iii) finally, because trade law can limit the policy space that regulators have at home.Footnote 58 Thinking of the layered structure of the Internet, one also ought to take into account the entire set of global economic law rules that regulate infrastructure (e.g. rules with regard to communication networks and services, technical standards and IT hardware) and applications and content (such as software, computer and audiovisual services), so as to understand the existing regulatory environment with regard to data flows.Footnote 59 In addition to this generic trade law framework, whose rules are found both in WTO law and in the WTO-plus preferential agreements, the last decade has also witnessed the emergence of entirely new rules that explicitly regulate data flows. This section provides a brief overview of these rules.
It needs to be mentioned at the outset that there is no common agreement on a definition of data flows in PTAs, despite the wide-spread rhetoric around the term and its frequent use in reports and studies.Footnote 60 One of the first agreements that targets data – the South Korea–United States FTA – stressed in its Article 15.8 ‘the importance of the free flow of information in facilitating trade, and acknowledging the importance of protecting personal information’ and encouraged the Parties ‘to refrain from imposing or maintaining unnecessary barriers to electronic information flows across borders’.Footnote 61 Later agreements, such as the CPTPP and the USMCA, that are analyzed in more detail later, speak of ‘cross-border transfer of information by electronic means, including personal information’Footnote 62 and this has become the most common wording thus far. The new generation of EU FTAs have been cautious with regard to data and has only recently started to promote the inclusion of provisions on the ‘free flow of data’.Footnote 63 In essence, what can be maintained is that so far in the trade policy discourse and in the treaty language, there has not been any clear definition but despite the different terms used, there seems to be a tendency for a broad and encompassing definition of data flows (i) where there are bits of information (data) as part of the provision of a service or a product and (ii) where this data crosses borders, although the data flows do not neatly coincide with one commercial transaction and the provision of certain service may relate to multiple flows of data. In this sense, ‘[t]he geography of data flows is very different from the geography of trade flows’.Footnote 64 In addition, it may be noted that there has not been a distinction between different types of data – for instance, between personal and non-personal data, personal or company data or machine-to-machine data.Footnote 65 Yet, personal information is commonly included explicitly in the data-related provisions in PTAs,Footnote 66 whereby the potential clashes with domestic data protection regimes become evident.
Overall, specific data-related provisions are a relatively new phenomenon and can be found primarily in dedicated e-commerce chapters of PTAs and only in a handful of agreements. The rules refer to both the free cross-border flow of data and to banning or limiting data localization requirements. Provisions on the cross-border flow of data can be also found in chapters dealing with discrete services sectors, where data flows are inherent to the very definition of those servicesFootnote 67 – this is particularly valid for the telecommunications and the financial services sectors, as shown in Table 1.3.
Table 1.3. Overview of data-related provisions in PTAs
| Data flows | ||||
|---|---|---|---|---|
| General | Financial services | Telecommunication services | Data localization | |
| Soft commitments | 16 | 0 | 1 | 1 |
| Hard commitments | 12 | 70 | 64 | 11 |
| Total number of provisions | 28 | 70 | 65 | 12 |
1 Rules on Data Flows
If we look at the evolution of data flow provisions in PTAs, there has been a sea change over the years. Non-binding provisions on data flows appeared early. Already in the 2000 Jordan–US FTA, the Joint Statement on Electronic Commerce highlighted the ‘need to continue the free flow of information’, although it fell short of including an explicit provision in this regard. The first agreement having such a provision is the 2006 Taiwan–Nicaragua FTA, where as part of the cooperation activities, the parties affirmed the importance of working ‘to maintain cross-border flows of information as an essential element to promote a dynamic environment for electronic commerce’.Footnote 68 A similar wording is used in the 2008 Canada–Peru FTA,Footnote 69 the 2011 Korea–Peru FTA,Footnote 70 the 2011 Central America–Mexico FTA,Footnote 71 the 2013 Colombia–Costa Rica FTA,Footnote 72 the 2013 Canada–Honduras FTA,Footnote 73 the 2014 Canada–Korea FTA,Footnote 74 and the 2015 Japan–Mongolia FTA.Footnote 75 In the same line, in the 2010 Hong Kong–New Zealand FTA, the parties agreed to ensure that ‘their regulatory regimes support the free flow of services, including the development of innovative ways of developing services, using electronic means’.Footnote 76
A slightly stronger commitment can be found in the 2007 South Korea–US FTA, where the parties, after ‘recognizing the importance of the free flow of information in facilitating trade, and acknowledging the importance of protecting personal information’, stated that they ‘shall endeavor to refrain from imposing or maintaining unnecessary barriers to electronic information flows across borders’.Footnote 77 More recently and as typically for EU-led agreements, the parties have agreed to consider in future negotiations commitments related to cross-border flow of information. Such a clause is found in the 2018 EU–Japan EPA,Footnote 78 and in the modernization of the trade part of the EU–Mexico Global Agreement, currently under negotiation. In the latter two agreements, the parties commit to ‘reassess’ within three years of the entry into force of the agreement, the need for inclusion of provisions on the free flow of data into the treaty. This signals a repositioning of the EU on the issue of data flows, as well as EU’s wish to couple this in due time with the high data protection standards of the GDPR.Footnote 79 The EU follows this model of endorsing and protecting privacy as a fundamental right also in its proposals for digital trade chapters in the currently negotiated trade agreements with Australia, New Zealand and Tunisia,Footnote 80 as well as in the EU proposal for WTO rules on electronic commerce.Footnote 81
The first agreement having a binding provision on cross-border information flows is the 2014 Mexico–Panama FTA. According to this treaty, each party ‘shall allow its persons and the persons of the other Party to transmit electronic information, from and to its territory, when required by said person, in accordance with the applicable legislation on the protection of personal data and taking into consideration international practices’.Footnote 82 A much more detailed provision in this regard is found in the 2015 amended version of the Pacific Alliance Additional Protocol (PAAP),Footnote 83 which was modelled along the negotiated text of the 2016 Transpacific Partnership Agreement (TPP) and which has since then largely influenced all subsequent agreements having data flows provisions, such as notably the CPTPP and the USMCAFootnote 84 – both endorsing a strong protection of the free flow of data, as discussed in more detail later.
2 Data Localization
In recent years, some PTAs have started to include specific provisions on data localization, by either banning or limiting requirements of data localization or data use. An important difference with the data flows provisions analyzed earlier is that almost all the provisions on data localization found in PTAs are binding.Footnote 85 The first agreement with such rules is the 2015 Japan–Mongolia FTA. The provision stipulates that neither party shall require a service supplier of the other party, an investor of the other party, or an investment of an investor of the other party in the area of the former party, to use or locate computing facilities in that area as a condition for conducting its business.Footnote 86 Later the same year, the 2015 amended version of the PAAP, and as strongly influenced by the parallel TPP negotiations, included a similar provision on the use and location of computer facilities.Footnote 87 In 2016, the TPP included a clear ban on localization, which was then replicated in the CPTPP and the USMCA. The diffusion of these norms is clearly discernible in subsequent PTAs, such as the 2016 Chile–Uruguay FTAFootnote 88 and the 2016 Updated SAFTA,Footnote 89 which closely follow the CPTPP template.Footnote 90
3 Privacy and Data Protection
Eighty-one PTAs in our dataset include provisions on privacy, usually under the concept of ‘data protection’. Yet, the way personal data is protected varies considerably and can include a truly mixed bag of binding and non-binding provisions (see Table 1.4), which is symptomatic of the very different positions of the major actors and the inherent tensions between the regulatory goals of data innovation and data protection.Footnote 91
Table 1.4. Overview of privacy-related provisions in PTAs
| Total number of provisions | 89 |
| Soft commitments | 81 |
| Hard commitments | 8 |
Earlier agreements dealing with privacy issues consist of non-binding declarations. The 2000 Jordan–US FTA Joint Statement on Electronic Commerce, for instance, merely declares it necessary to ensure the effective protection of privacy regarding the processing of personal data on global information networks, yet states also that the means for privacy protection should be flexible and parties should encourage the private sector to develop and implement enforcement mechanisms, such as guidelines and verification and recourse methodologies, recommending the OECD Privacy Guidelines as an appropriate basis for policy development.Footnote 92 Similarly, the 2001 Canada–Costa Rica FTA includes a provision on privacy as part of the Joint Statement on Global Electronic Commerce, with both parties agreeing to share information on the functioning of their respective data protection regimes.Footnote 93 Later agreements include cooperation activities on enhancing the security of personal data in order to improve the level of protection of privacy in electronic communications and avoid obstacles to trade that requires transfer of personal data.Footnote 94 These activities include sharing information and experiences on regulations, laws and programmes on data protectionFootnote 95 or the overall domestic regime for the protection of personal information;Footnote 96 technical assistance in the form of exchange of information and experts;Footnote 97 research and training activities;Footnote 98 the establishment of joint programmes and projects;Footnote 99 maintaining a dialogue;Footnote 100 holding consultations on matters of data protection;Footnote 101 or in general, other cooperation mechanisms to ensure the protection of personal data.Footnote 102
PTAs have also dealt with personal data protection with reference to the adoption of domestic standards. While some merely recognize the importance or the benefits of protecting personal information online,Footnote 103 in several treaties parties specifically commit to adopt or maintain legislation or regulations that protect the personal data or privacy of users,Footnote 104 in relation to the processing and dissemination of data,Footnote 105 which may also include administrative measures,Footnote 106 or the adoption of non-discriminatory practices.Footnote 107 Few agreements include qualifications of this commitment, in the sense that each party shall take measures it deems appropriate and necessary considering the differences in existing systems for personal data protection,Footnote 108 that such measures shall be developed insofar as possible,Footnote 109 or that the parties have the right to define or regulate their own levels of protection of personal data in pursuit or furtherance of public policy objectives, and shall not be required to disclose confidential or sensitive information.Footnote 110 Some PTAs add that in the development of online personal data protection standards, each party shall take into account the existing international standards,Footnote 111 as well as criteria or guidelines of relevant international organizations or bodiesFootnote 112 – such as the APEC Privacy Framework and the OECD Guidelines on Transborder Flows of Personal Data (2013);Footnote 113 or to accord a high level of protection compatible with the highest international standards in order to ensure the confidence of e-commerce users.Footnote 114 In a handful of treaties, the parties commit to publish information on the personal data protection it provides to users of e-commerce,Footnote 115 including how individuals can pursue remedies and how businesses can comply with any legal requirements.Footnote 116 Certain agreements put special emphasis on the transfer of personal data, stipulating that it shall only take place if necessary for the implementation, by the competent authorities, of agreements concluded between the parties,Footnote 117 or that the countries need to have an adequate level of safeguards for the protection of personal data.Footnote 118 Some treaties add that the parties will encourage the use of encryption or security mechanisms for the personal information of the users, and their dissociation or anonymization, in cases where said data is provided to third parties.Footnote 119
PTA parties have also employed more binding options to protect personal information online. A first option is to consider the protection of the privacy of individuals in relation to the processing and dissemination of personal data and the protection of confidentiality of individual records as an exception in specific chapters of the agreement – such as for trade in services,Footnote 120 investment or establishment,Footnote 121 movement of persons,Footnote 122 telecommunicationsFootnote 123 and financial services.Footnote 124 Certain agreements, mostly EU led, even have special chapters on protection of personal data, including the principles of purpose limitation, data quality and proportionality, transparency, security, right to access, rectification and opposition, restrictions on onward transfers, and protection of sensitive data, as well as provisions on enforcement mechanisms, coherence with international commitments and cooperation between the parties in order to ensure an adequate level of protection of personal data.Footnote 125 The USMCA was the first US-led PTA to include such a provision that recognizes key principles of data protection.Footnote 126
A second option lets countries adopt appropriate measures to ensure the privacy protection while allowing the free movement of data, establishing a criterion of ‘equivalence’ – meaning that countries agree that personal data may be exchanged only where the receiving party undertakes to protect such data in at least an equivalent, similar or adequate way to the one applicable to that particular case in the party that supplies it. This has been largely the EU approach and to that end, parties commit to inform each other of their applicable rules and negotiate reciprocal general or specific agreements.Footnote 127
A third, less used, option leaves the development of rules on data protection to a treaty body. For example, in the 2012 Colombia–EU–Peru FTA (which also now includes Ecuador), the Trade Committee may establish a working group with the task of proposing guidelines to enable the signatory Andean Countries to become a ‘safe harbour’ for the protection of personal data. To this end, the working group shall adopt a cooperation agenda that defines priority aspects for accomplishing that purpose, especially regarding the respective homologation processes of data protection systems.Footnote 128
D Substantive Developments in Digital Trade Governance
As evident from the earlier overview, the regulatory environment for data flows has been substantially shaped by PTAs. The United States has played a key role in this process and has sought to endorse liberal rules in implementation of its ‘Digital Agenda’.Footnote 129 The agreements reached since 2002 with Australia, Bahrain, Chile, Morocco, Oman, Peru, Singapore, the Central American countries,Footnote 130 Panama, Colombia and South Korea, all contain critical WTO-plus (going above the WTO commitments) and WTO-extra (addressing issues not covered by the WTO) provisions in the broader field of digital trade. The emergent regulatory template on digital issues is not however limited to US agreements but has diffused and can be found in other FTAs, as evident from the earlier overview. Singapore, Australia, Japan and Colombia have been among the major drivers of this diffusion but as earlier mentioned, the issues covered and the levels of legalization may still vary substantially.Footnote 131
Key aspects of digital trade are typically addressed in (i) specifically dedicated e-commerce chapters; (ii) the chapters on cross-border supply of services; and (iii) the IP chapters. The electronic commerce chapters show by far the most substantial evolution over time – moving from less to more binding and from a mere compensation for the lack of progress in the WTO towards new (and partially innovative) digital trade rule-making. In the former sense, they have included a clear definition of ‘digital products’, which treats digital products delivered offline equally as those delivered online, so that technological neutrality is ensured. The chapters also recognize the applicability of WTO rules to electronic commerce, and establish a permanent moratorium on duties on the import or export of digital products by electronic transmission. Critically, the e-commerce chapters, especially those of US-led agreements, ensure both MFN and NT for digital products trade; discrimination is banned on the basis that digital products are ‘created, produced, published, stored, transmitted, contracted for, commissioned, or first made available on commercial terms outside the country’s territory’ or ‘whose author, performer, producer, developer, or distributor is a person of another party or a non-party’.Footnote 132
The e-commerce chapters do also include rules that go beyond the WTO and next to provisions on IT standards and interoperability, cybersecurity, electronic signatures and payments, paperless trading and e-government, the rules on data flows are the most illustrative example in this context. In the following two sections, we look more closely at the most advanced template for digital trade chapters endorsed by the CPTPP and slightly further developed by the USMCA, including also some remarks on the dedicated US–Japan Digital Trade Agreement.
I The CPTPP
The Comprehensive and Progressive Agreement for Transpacific Partnership (CPTPP; also known as the TPP11 or TPP 2.0)Footnote 133 was agreed upon in 2017 among eleven countries in the Pacific RimFootnote 134 and entered into force on 30 December 2018. The CPTPP represents 13.4 per cent of the the global gross domestic product, or $13.5 trillion, making it the third largest trade agreement after the North American Free Trade Agreement and the single market of the European Union.Footnote 135 Beyond the broader economic impact and, more importantly, for the discussion of this chapter, the CPTPP chapter on e-commerce created the most comprehensive template so far in the landscape of PTAs. It comprises eighteen articles and includes a number of new features.Footnote 136 It is fair to note that the e-commerce chapter of the CPTPP ‘survived’ the TPP negotiations in its entirety and without any change, so in a sense it still very much reflects the efforts of the United States in the domain of digital trade rule-making.
The CPTPP sought for the first time to explicitly restrict the use of data localization measures. Article 14.13(2) prohibits the parties from requiring a ‘covered person to use or locate computing facilities in that Party’s territory as a condition for conducting business in that territory’. The soft language from the US–South Korea FTA on free data flows is now framed as a hard rule: ‘[e]ach Party shall allow the cross-border transfer of information by electronic means, including personal information, when this activity is for the conduct of the business of a covered person’.Footnote 137 The rule has a broad scope and most data that is transferred over the Internet is likely to be covered, although the word ‘for’ may suggest the need for some causality between the flow of data and the business of the covered person.
Measures restricting digital flows or localization requirements under Article 14.13 CPTPP are permitted only if they do not amount to ‘arbitrary or unjustifiable discrimination or a disguised restriction on trade’ and do not ‘impose restrictions on transfers of information greater than are required to achieve the objective’.Footnote 138 These non-discriminatory conditions are similar to the test formulated by Article XIV GATS and Article XX GATT, which, as earlier noted, is meant to balance trade and non-trade interests. The CPTPP test differs from the WTO norms in one significant element: while there is a list of public policy objectives in the GATT and the GATS (such as public morals or public order), the CPTPP provides no such enumeration and simply speaks of a ‘legitimate public policy objective’.Footnote 139 This permits more regulatory autonomy for the CPTPP signatories. However, it also may lead to overall legal uncertainty. Further, it should be noted that the ban on localization measures is somewhat softened with regard to financial services and institutions.Footnote 140 An annex to the financial services chapter has a separate data transfer requirement, whereby certain restrictions on data flows may apply for the protection of privacy or confidentiality of individual records, or for prudential reasons.Footnote 141 Government procurement is also excluded.Footnote 142
Pursuant to Article 14.17, a CPTPP member may not require the transfer of, or access to, source code of software owned by a person of another party as a condition for the import, distribution, sale or use of such software, or of products containing such software, in its territory. The prohibition applies only to mass-market software or products containing such software.Footnote 143 This means that tailor-made products are excluded, as well as software used for critical infrastructure and those in commercially negotiated contracts.Footnote 144 The aim of this provision is to protect software companies and address their concerns about loss of IP or cracks in the security of their proprietary code.Footnote 145
These provisions illustrate an important development this chapter alluded to earlier, namely, the evolution of digital trade rules that go beyond the WTO and do not simply entail a clarification of existing bans on discrimination or more liberal commitments. It is also evident that the new rules do not merely set higher standards, as is generally anticipated from trade agreements; rather, they shape the regulatory space domestically and may even lower certain standards. A commitment to lower standards of protection is particularly palpable in the field of privacy and data protection.
Article 14.8(2) requires every CPTPP party to ‘adopt or maintain a legal framework that provides for the protection of the personal information of the users of electronic commerce’. No standards or benchmarks for the legal framework have been specified, except for a general requirement that CPTPP parties ‘take into account principles or guidelines of relevant international bodies’.Footnote 146 A footnote provides some clarification in saying that ‘[f]or greater certainty, a Party may comply with the obligation in this paragraph by adopting or maintaining measures such as a comprehensive privacy, personal information or personal data protection laws, sector-specific laws covering privacy, or laws that provide for the enforcement of voluntary undertakings by enterprises relating to privacy’.Footnote 147 Parties are also invited to promote compatibility between their data protection regimes.Footnote 148 Overall, there is a priority given to trade over privacy protection. This commitment had been pushed by the United States, which subscribes to a relatively weak and patchy protection of privacy. Timewise, this insertion can be linked to the Schrems I judgment of the Court of Justice of European Union (CJEU) that struck down the EU–US Safe Harbor Agreement.Footnote 149
The CPTPP contains also rules on consumer protection,Footnote 150 network neutralityFootnote 151 and spam control,Footnote 152 although these are fairly weak. The same is true for the newly introduced rules on cybersecurity under Article 14.16, which identifies a relatively limited scope of activities for cooperation, in situations of ‘malicious intrusions’ or ‘dissemination of malicious code’, and capacity-building of governmental bodies dealing with cybersecurity incidents.
II The USMCA
After the withdrawal of the United States from the TPP, there was some uncertainty as to the direction it will follow in its trade deals in general and on matters of digital trade in particular. The renegotiated NAFTA, now referred to as ‘United States–Mexico–Canada Agreement’ (USMCA), casts the doubts aside. The USMCA has a comprehensive electronic commerce chapter, which is now also properly titled ‘Digital Trade’ and follows all critical lines of the CPTPP in ensuring the free flow of data through a clear ban on data localization (Article 19.12), providing a non-discrimination treatment for digital products (Article 19.4) and a hard rule on free information flows (Article 19.11).
The USMCA appears particularly interesting in two aspects. The first one is that it keeps the clause on exceptions that permits the pursuit of certain non-economic objectives. Article 19.11 specifies, very much in the sense of the CPTPP, that parties can adopt or maintain a measure inconsistent with the free flow of data provision, if this is necessary to achieve a legitimate public policy objective, provided that the measure (a) is not applied in a manner which would constitute a means of arbitrary or unjustifiable discrimination or a disguised restriction on trade; and (b) does not impose restrictions on transfers of information greater than are necessary to achieve the objective.Footnote 153 Furthermore and departing from the standard US approach, the USMCA signals abiding to some data protection principles. While Article 19.8 remains soft on prescribing domestic regimes on personal data protection, it recognizes principles and guidelines of relevant international bodies. Article 19.8 recognizes ‘the economic and social benefits of protecting the personal information of users of digital trade and the contribution that this makes to enhancing consumer confidence in digital trade’Footnote 154 and requires from the parties to ‘adopt or maintain a legal framework that provides for the protection of the personal information of the users of digital trade. In the development of its legal framework for the protection of personal information, each party should take into account principles and guidelines of relevant international bodies, such as the APEC Privacy Framework and the OECD Recommendation of the Council concerning Guidelines Governing the Protection of Privacy and Transborder Flows of Personal Data (2013)’.Footnote 155
The parties also recognize key principles of data protection, which include limitation on collection; choice; data quality; purpose specification; use limitation; security safeguards; transparency; individual participation; and accountability,Footnote 156 and aim to provide remedies for any violations.Footnote 157 This is interesting because it may go beyond what the United States has in its national laws on data protection and also because it reflects some of the principles the European Union has advocated in the domain of the protection of privacy. One can of course wonder whether this is a development caused by the ‘Brussels effect’, whereby the EU ‘exports’ its own domestic standards and they become global,Footnote 158 or whether we are seeing a shift in US privacy protection regimes as well.Footnote 159
Finally, three innovations of the USMCA may be mentioned. The first refers to the inclusion of ‘algorithms’, the meaning of which is ‘a defined sequence of steps, taken to solve a problem or obtain a result’Footnote 160 and has become part of the ban on requirements for the transfer or access to source code in Article 19.16. The second novum refers to the recognition of ‘interactive computer services’ as particularly vital to the growth of digital trade. Parties pledge in this sense not to ‘adopt or maintain measures that treat a supplier or user of an interactive computer service as an information content provider in determining liability for harms related to information stored, processed, transmitted, distributed, or made available by the service, except to the extent the supplier or user has, in whole or in part, created, or developed the information’.Footnote 161 This provision is important, as it seeks to clarify the liability of intermediaries and delineate it from the liability of host providers with regard to IP rights’ infringement.Footnote 162 It also secures the application of Section 230 of the US Communications Decency Act,Footnote 163 which insulates platforms from liability but has been recently under attack in many jurisdictions, including in the United States, in the face of fake news and other negative developments related to platforms’ power.Footnote 164 The third and rather liberal commitment of the USMCA parties regards open government data. This is truly innovative and very relevant in the domain of domestic regimes for data governance. In Article 19.18, the parties recognize that facilitating public access to and use of government information fosters economic and social development, competitiveness and innovation. ‘To the extent that a Party chooses to make government information, including data, available to the public, it shall endeavor to ensure that the information is in a machine-readable and open format and can be searched, retrieved, used, reused, and redistributed.’Footnote 165 There is in addition an endeavour to cooperate, so as to ‘expand access to and use of government information, including data, that the Party has made public, with a view to enhancing and generating business opportunities, especially for small and medium-sized enterprises’.Footnote 166
The US approach towards digital trade issues has been confirmed also by the recent US–Japan Digital Trade Agreement (DTA), signed on 7 October 2019, alongside the US–Japan Trade Agreement.Footnote 167 The DTA can be said to replicate almost all provisions of the USMCA and the CPTPP,Footnote 168 including the new USMCA rules on open government data,Footnote 169 source codeFootnote 170 and interactive computer servicesFootnote 171 but notably covering also financial and insurance services as part of the scope of agreement. A new provision has been added with regard to ICT goods that use cryptography,Footnote 172 which complements the source code provisions and is similar to Annex 8-B, section A.3 of the CPTPP chapter on technical barriers to trade, which addresses practices by several countries, in particular China, that impose bans on encrypted products or set specific technical regulations that restrict the sale of such products.Footnote 173
E Conclusion
The era of big data has ushered in new challenges for global trade law. Policymakers are faced with the extremely difficult task to match the existing, largely analogue-based, institutions and rules of international economic law with the dynamic, scruffy innovation of digital platformsFootnote 174 and data that flows regardless of state borders. At the same time, and this only makes the task more taxing, it is evident that the regulatory framework that will be chosen will have immense effects on innovation and the fate of the data-driven economy,Footnote 175 as well as on fundamental rights beyond the province of the economy, such as the protection of citizens’ privacy. Despite the importance and the urgency of finding appropriate governance solutions, global trade law has not undergone a radical overhaul so far and legal adaptation has been slow and patchy, as this chapter showed. PTAs have become the preferred venue, where digital trade rules have been adopted – on the one hand, so as to compensate for the lack of progress under the umbrella of the WTO and on the other hand, and more importantly, so as to create new rules that address new trade barriers, such as data localization measures; new and pressing concerns, such as the acute need to interface trade and personal data protection mechanisms, and overall, to provide a regulatory environment that is conducive to the practical reality of digital trade and that provides a level of legal certainty for all actors involved. It has been the chapter’s objective to provide a better understanding of this newly emerged governance landscape by tracing broader developments and trends, by looking in particular at the data-related rules across PTAs and analyzing more closely the most sophisticated templates of e-commerce chapters so far, as found in the CPTPP and the USMCA.
The understanding of the existing rules on digital trade and their evolution over time is absolutely essential for future attempts of individual states and of the international community to grapple with the digital challenge. It may be important also for other governance actors, such as companies, think tanks, non-governmental organizations and even individual citizens who wish to more actively engage in the rule-making processes in trade agreements, which by definition tend to be behind closed doors and with little to none stakeholder involvement.Footnote 176 The experience gathered in PTAs may also be invaluable for the ongoing reinvigorated efforts in the WTO to reach an agreement on electronic commerce, as well as in new bolder deals that go beyond existing commitments and look at a range of emerging issues, such as digital identity, AI, electronic invoicing and open data, such as those covered under the DEPA.
As a final thought, one may stress that the data economy has placed higher demands on regulatory cooperation.Footnote 177 As the complexity of the data-driven society rises, enhanced regulatory cooperation seems indispensable for moving forward, since data issues cannot be covered by the mere ‘lower tariffs, more commitments’ stance in trade negotiations but entail the need for reconciling different interests and the need for oversight. In this context, while the paths for engaging in and advancing regulatory cooperation would ideally be followed in the multilateral forum,Footnote 178 preferential trade venues can serve as governance laboratories. The way forward may be truly bright but remains highly (and perhaps unfortunately so) dependent on the role that the key players, the United States, the EU and China, are willing to assume.
A Introduction
Innovation in information and communication technology (ICT) has been one of the key drivers of economic globalization. As a result, the volume of goods and services and, therefore, cross-border data flows have been increasing at an exceptional speed. The World Trade Organization (WTO) and its members have early on realized the importance of establishing global rules for guiding these processes. Already at its Second Ministerial Conference in 1998, the WTO adopted the Declaration on Global Electronic Commerce and called for the establishment of a work programme on e-commerce. The work programme has been implemented by four of the WTO’s bodies which have regularly reported on the developments,Footnote 1 and the General Council has periodically reviewed the progress of the programme. Based on the minutes of the meetings of the General Council, Figure 2.1 maps the number of interventions by WTO members related to the topic of e-commerce. The data shows important variation in terms of attention given to the topic over time. After a substantial interest on e-commerce–related issues in the late 1990s and the early 2000s, the preoccupation with the topic dropped dramatically from 2003 until around 2011. Overall attention has only picked up again in the past few years. In preparation for the Eleventh Ministerial Conference (MC11) in Buenos Aires in December 2017, e-commerce was back on the table and the subject of many of the interventions made in the General Council.

Figure 2.1. Interventions on e-commerce in the WTO General Council, 1995–2018
Following intensified discussions, seventy-six WTO members issued a joint statement on e-commerce during the World Economic Forum meeting in Davos in January 2019 in which they ‘confirm [their] intention to commence WTO negotiations on trade-related aspects of electronic commerce’, ‘seek to achieve a high standard outcome that builds on existing WTO agreements and frameworks with the participation of as many WTO Members as possible’ and ‘continue to encourage all WTO Members to participate in order to further enhance the benefits of electronic commerce for businesses, consumers and the global economy’.Footnote 2
Notwithstanding the newly found interest in e-commerce topics at the multilateral level, we observe that the WTO has been rather passive in its approach to address the data-related changes in the world economy. If regulatory solutions have been promoted, it was mostly driven by unilateral or extraterritorial approaches by the main trading powers. Given the absence of progress in rule-making in the WTO for some time now and a growing set of unilateral policies, the negotiators of preferential trade agreements (PTAs) have themselves attempted to shape the rule book for the twenty-first-century world economy – rules that would address needs resulting from an ever more integrated and data-driven economy. The first PTA that had an electronic-commerce provision was the Jordan–US PTA in 2000 and the first data flow provisions go back to the Korea–US PTA concluded in 2007. So, these types of provisions are a rather recent phenomenon in trade agreements, but it clearly shows that WTO members have shifted the venue for rule-making from the WTO to the world of PTAs starting in the early 2000s.Footnote 3
This chapter focuses on data-related provisions in PTAs and explores trends and patterns over time. We attempt to map clusters and models that have emerged. Related to this, we also focus on who the ‘rule-makers’ are in this regulatory area. If PTAs are best understood as ‘laboratories’ for global rule-making, we investigate in this chapter which governments are pivotal in pushing regulatory ideas and templates.
The chapter is organized as follows: first, we provide a short discussion of the literature that provides the backbone and rationale for the data collection. We then present particular indicators aggregated from the data that attempt to capture various salient dimensions of data flow–related provisions in PTAs. This is followed by an enquiry into the trends over time using these indicators, exploring the rule-makers’ roles through both text-as-data analyses and manual coding of data-related design features. Finally, we graphically explore bivariate relationships that speak to potential explanations why we would expect to see variation in PTA design in this domain. The chapter concludes by outlining possible next research avenues in the area of digital trade governance.
B A Look at State of the Art
Various strands of literature in international relations and political economy provide the backbone for collecting and analyzing PTA design features – some of them address general debates regarding the move towards more law, the relationship between multilateralism and regionalism or on rule-making versus rule-taking, the role of diffusion and debates specific to data flows and regulatory responses. We have mapped some of these debates in this chapter.
The call for more fine-grained information on the content of international agreements has been around for quite a while. Both the legalization as well as the rational design literatures provide useful guidance for choosing the types of design features to focus on.Footnote 4 Both literatures develop indicators and propose measures to account for treaties’ scope, degree of obligation as well as flexibility features. In particular in the trade literature on PTAs, various indicators have been further developed – such as with regard to the depth of an agreement which captures the degree to which measures may lead to increased market integrationFootnote 5 or with regard to various types of flexibility tools which allow for legally imposing barriers, normally for a limited period of time.Footnote 6 These conceptualizations are also insightful when mapping data flow provisions as part of PTAs.
Another strand of literature to which this chapter speaks is the work on regime complexity, which is usually defined as a set of non-hierarchical overlapping institutions.Footnote 7 The universe of PTAs with over one thousand agreements, where all WTO members are participating actors, serves as an interesting laboratory of how regime complexity affects the behaviour of states both in collaborative and conflictive fashions. Linked to the concept of regime complexity is the emerging attention given to diffusion drivers and effects,Footnote 8 which asks the essential questions of why states sign PTAs; what the role of competition with other trading nations is; how learning and mimicking from neighbouring countries impact the decision to engage in PTAs, or whether PTA signature and the treaty commitments are a result of coercion by powerful states that aim to have their templates and models reflected in as many treaties as possible. Both, the regime complexity theories and diffusion theories, provide strong testimony to how international treaties are interdependent and serve as a cautionary note of analyzing single agreements in isolation of other treaties. Within the study of international institutions and international trade, additional debates have emerged, focusing on the groups of countries that promote their own rules (‘rule-makers’) and the ones that are on the receiving end of global regulation (‘rule-takers’). This chapter focuses on the conditions under which rules diffuse using a mix of methods, including textual analyses.Footnote 9
Finally, research on trade and data flows can build on the work that has zoomed in on the relationship between the promotion of liberalization and a government’s objective to protect public interests. While the early trade literature focused on various linkages, such as trade and human rights and trade and environment,Footnote 10 more recently the concept of optimal protection of individual rights related to data protection has become more central. Following the old idea of ‘embedded liberalism’,Footnote 11 we are interested in how liberalization in data flows related to trade and services goes hand in hand with governments’ demands for flexibility or escape instruments to protect citizens’ interests in terms of privacy, and therefore pursuing social goals.
C Design Dimensions and Related Concepts
In recent years, research on trade agreements has made substantial progress by unpacking the various design features in PTAs to explore variation across treaties.Footnote 12 We follow this work by zooming in on data-relevant provisions. The data presented below is based on seventy-four single variables focusing, on the one hand, on the electronic commerce chapters and, on the other hand, on data-relevant provisions in other PTA chapters, including services, intellectual property rights and specific rules on ICT, data localization and similar content. The data is then aggregated to produce a number of indicators measuring various key dimensions derived from the earlier literature discussion. In the following, we briefly describe the different concepts and the types of variables that we draw upon to construct these.
I Scope
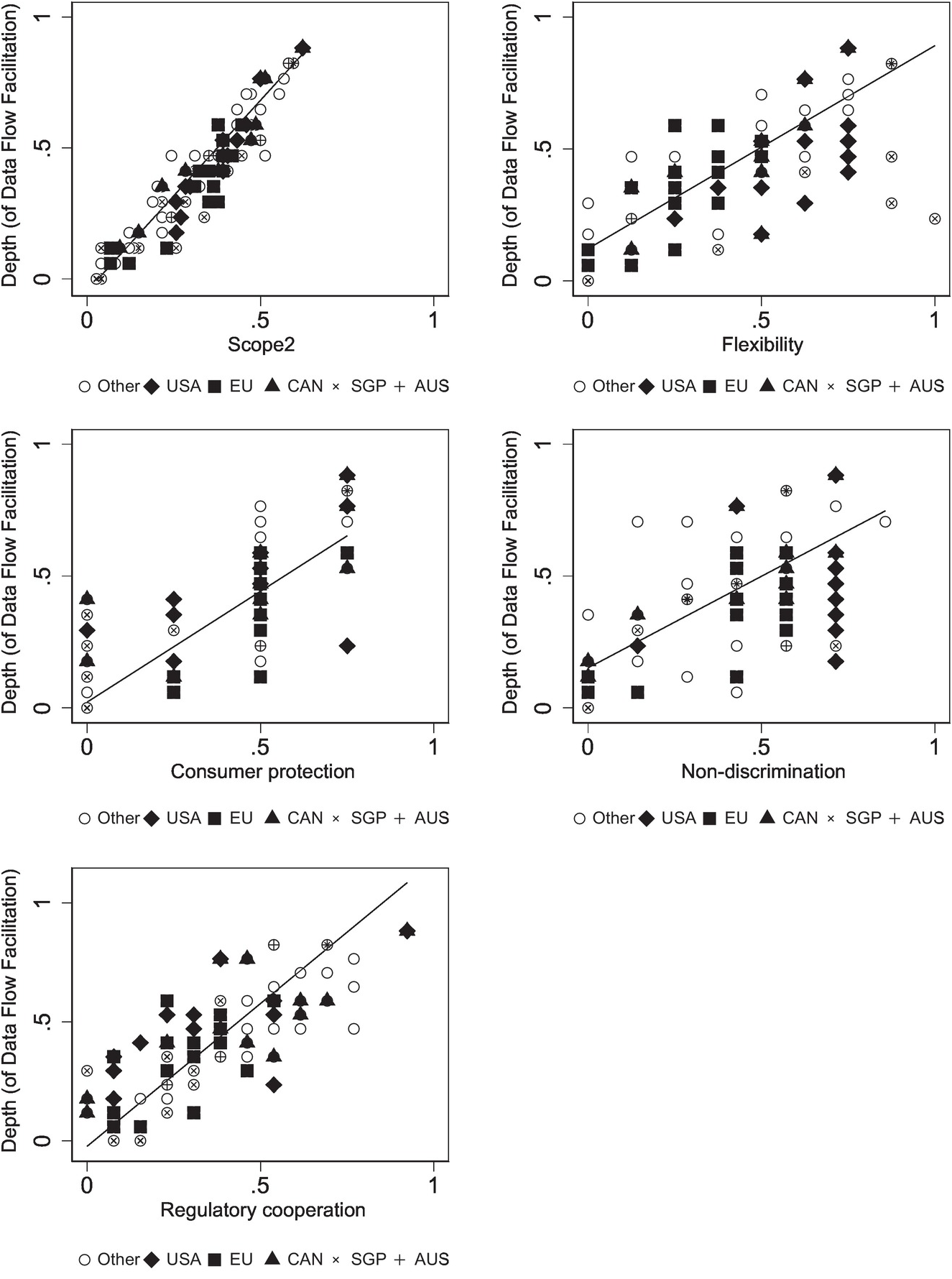
This concept measures the attention paid to data-related provisions. Scope is different from depth, as it does not capture the degree of obligation and commitment, but rather provides information about the extent to which the topic is covered within the agreement.Footnote 13 Therefore, we construct two different measures for scope or coverage: Scope 1 is the word count for the electronic commerce chapter; scope 2 is the number of total provisions found in the electronic commerce chapter. Scope 1 has a maximum of 3,206 words and the average value is 793. Scope 2 is an additive index which ranges from 0 to 74.
II Depth of Data Flow Facilitation
This measure comes closest to what is in the literature described as the depth of the agreement.Footnote 14 In this case, depth is thought of in relation to commitments, which tend to make trading easier when data transfer is involved. Here we create an additive index of seventeen variables that include rules for facilitating trade and providing for a regulatory environment to foster trade in data – these range from free movement of data commitments, promoting paperless trading and electronic signatures, and advocating self-regulation of the private sector to abstain from data localization measures. This additive indicator ranges from 0 to 17.
III Flexibility
As the literature on international institutions suggests that deeper commitments are also more flexible,Footnote 15 we constructed one indicator that focuses on eight escape and flexibility measures that we detected in the agreements’ texts. These include both general and specific exceptions to commitments as well as reservations. The flexibility indicator ranges from 0 to 8.
IV Consumer Protection
An important and more specific flexibility instrument consists of explicitly foreseeing ways to protect consumer interests. This indicator ranges from 0 to 4 and includes elements of individual rights in relation to data protection, Internet Governance principles, data localization measures or addressing spam.
V Non-discrimination
This indicator measures how much attention treaty drafters have directed to general principles related to non-discrimination, such as treating domestic and foreign actors equally as well as following the most favoured nation (MFN) clause. On top, we add references to the WTO commitments and the need for technology neutrality. The higher the indicator, the more negotiators embed trade agreements within the multilateral trading system aiming for more consistency across treaties.Footnote 16 The indicator ranges from 0 to 7.
VI Regulatory Cooperation
The final indicator measures the degree to which treaty drafters advocate various forms of regulatory cooperation. We compile commitments that call for cooperation on transparency, international alignment in regulatory fora or working together on cybersecurity issues. In addition, we explore whether the treaty mentions working groups or committees to implement the electronic commerce commitments. This indicator is a proxy for how much regulatory cooperation is foreseen in the treaty text. The indicator ranges from 0 to 13.
D Describing Trends and Patterns in Digital Trade Governance
In this section we discuss briefly the evolution of PTAs over time. We provide some descriptive statistics based on the indicators developed earlier, derive a better idea about who the rule-makers are and explore a number of bivariate relations which are suggestive about potential interdependence between design features, but also between treaty content and domestic practice.
The first agreement referring to electronic commerce was signed in 2000. Therefore, we deal with a rather novel issue area for trade regulation. There are no observations prior to 2000 while discussions within the WTO had been going on for a while. This is suggestive to the possibility that governments have prioritized the multilateral arena while then slowly turning to PTAs either because of lack of progress in the WTO (see Figure 2.1), or because of learning effects and development of various government strategies and potentially implicit models. Figure 2.2 shows the steady increase of e-commerce provisions, e-commerce chapters and provisions on free data flow both in absolute numbers and relative to the number of PTAs signed per year.

In total, we have identified ninety-nine PTAs that have at least one data-related provision. Table 2.1 provides the summary statistics for the different indicators outlined earlier and confirms the notion of considerable heterogeneity among PTAs.
Table 2.1. Summary statistics on the indicators
| Variable | Obs | Mean | Std. Dev. | Min | Max |
|---|---|---|---|---|---|
| Scope 1 | 99 | 793.2 | 669.2 | 17 | 3,209 |
| Scope 2 | 99 | 22.9 | 10.5 | 2 | 46 |
| Depth | 99 | 6.5 | 3.5 | 0 | 15 |
| Flexibility | 99 | 3.3 | 2.1 | 0 | 8 |
| Consumer protection | 99 | 1.6 | 0.8 | 0 | 3 |
| Non-discrimination | 99 | 3.0 | 1.7 | 0 | 6 |
| Regulatory cooperation | 99 | 4.3 | 2.7 | 0 | 12 |
In the following figures, we zoom into a selection of indicators and illustrate their evolution over time. Figure 2.3 shows the Scope1 indicator, which captures the number of words related to the regulation of e-commerce and data flows. The median and range of the count of words varies considerably over time. We also observe a number of outliers, including Jordan–Singapore 2004, the Central European Free Trade Agreement (CEFTA) in 2006 and Australia–Japan 2015. The latter one is an outlier for that year but is following an upward trend. We also observe large variation in the years 2016–2018.

Figure 2.3. The Scope 1 indicator, 2000–2018.
In Figure 2.4 we show the second scope indicator, based on the number of provisions related to the regulation of e-commerce and data flows. Again, we observe that scope increases; however, this does not occur gradually. In most years, we notice a considerable range of provisions as well as a number of outliers. Compared to other PTAs signed in 2006, CEFTA has only few provisions related to the regulations of e-commerce and data flows. In 2007, the same is true for the PTA between Japan and Thailand. In contrast, the Panama–US PTA in 2007 includes a rather large number of provisions on this topic. The PTA between Colombia and Costa Rica presents the top outlier in 2013, the PTA between Central America and the European Free Trade Association (EFTA) the bottom outlier. Malaysia–Turkey and Canada–Ukraine present the two outliers in 2014 and 2016, respectively.

Figure 2.4. The Scope 2 indicator, 2000–2018.
Over time, we also detect an increase in the depth (Data Flow Facilitation) indicator (Figure 2.5). Following the above trend, the 2006 CEFTA agreement and the 2007 Japan–Thailand PTA indicate substantially shallower commitments than other agreements in these respective years. The outlier PTAs having substantially deeper commitments in 2013 than other agreements signed in that year are Colombia–Costa Rica as well as Colombia–Panama, most likely inspired by their commitments in one of their recent trade agreements with a rule-maker. In 2015, we observe in Mongolia’s first ever PTA with Japan also deeper commitments in terms of data flow facilitation.

Figure 2.5. The depth indicator, 2000–2018.
Turning to our flexibility indicator (Figure 2.6), we observe that already between 2004 and 2008 PTAs included higher levels of flexibility. Again, CEFTA presents the outlier in 2006, which is not surprising as it also scored low on scope and depth. The bottom outlier in 2015 is the PTA between Canada and Ukraine, which might be explained by the low trade flows in goods and services with substantial data content between the two countries. The top outlier in the same year is the PTA between Australia and Singapore, which could be a result of two countries with usually deep agreements.
E Of Rule-Makers and Central Actors
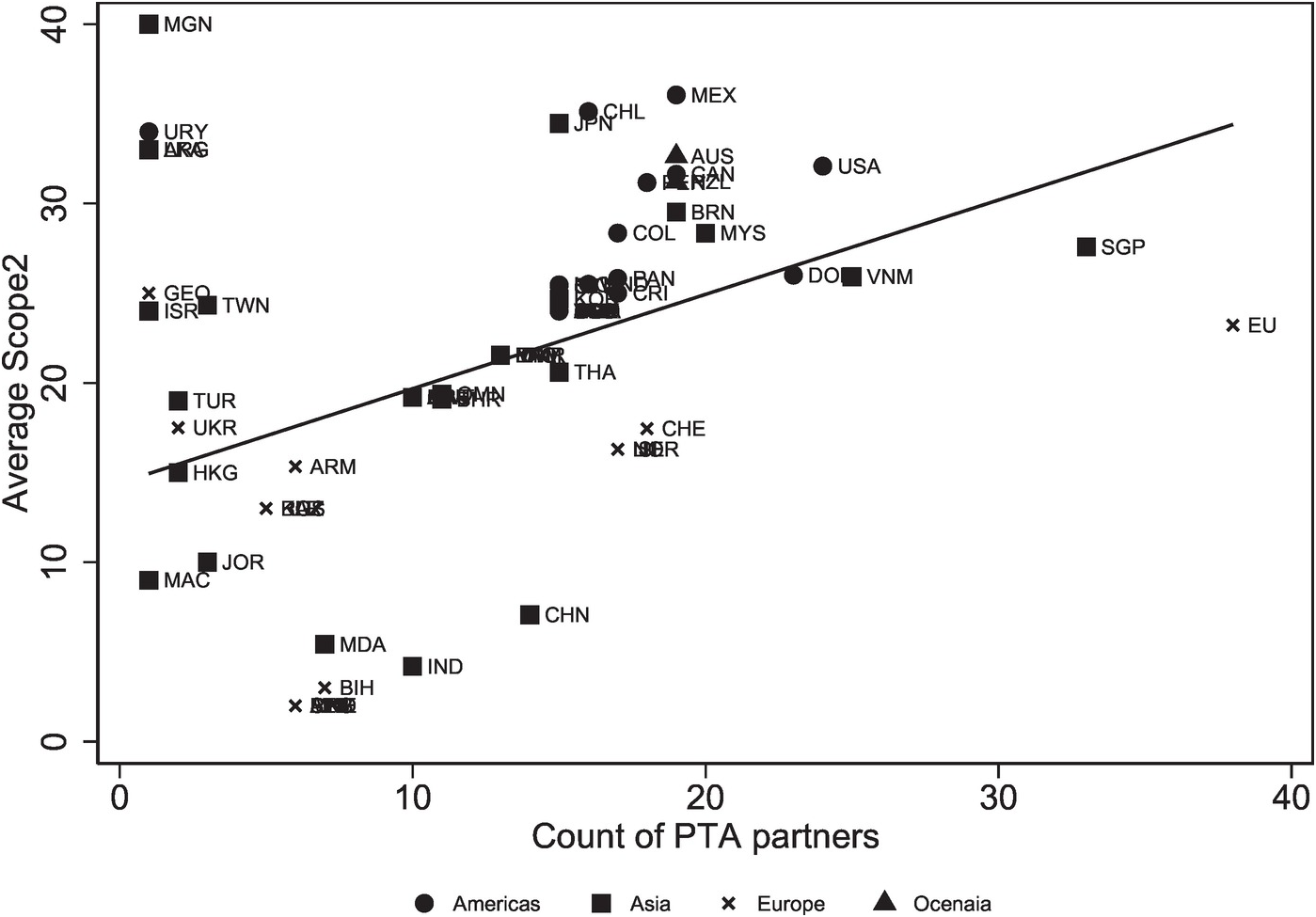
The previous sections discussed the various indicators and illustrated their variation over time. In this section, we take a closer look at the signatory countries. In total, eighty-two countries (counting the EU as one actor) are involved in the ninety-nine PTAs which have data flow–related provisions since 2000. As illustrated in Figure 2.7, there is considerable heterogeneity in terms of the number of PTA partners by signatory and the degree of scope measured by the number of provisions. Since 2000, the EU has signed eighteen PTAs with thirty-eight partner countries and, on average, included twenty-three provisions on e-commerce and data flows. Mongolia (MGN) has only signed one PTA (with Japan). In this PTA, however, there are forty provisions on e-commerce and data flows. The United States has signed fewer agreements than the EU, but on average their scope is substantially higher. We also observe that the average scope of agreements with European countries is significantly lower than treaties with countries of the Americas. Oceania is also above average in terms of scope. Finally, African signatories of PTAs are not yet addressing data flow–related provisions. This is surprising given the potential of e-commerce for developing countries.
To illustrate this network of PTAs, we combine the average Scope 2 indicator and the count of PTA partner countries for each signatory country and represent this in Figure 2.8 using instruments of network analysis. In this network, the size of each country is proportional to its weighted centrality. That is, the size of each country is proportional to the product of the number of PTA partners and the average number of provisions on e-commerce and data flows included in all its PTAs. The width of the links is proportional to the number of e-commerce and data flow provisions in a given PTA. Figure 2.8 highlights that there are some countries that are central to this PTA network and therefore potentially influential in diffusing certain regulatory models on e-commerce and data flows. The European Union, the United States and Singapore stand out, but also other countries, such as Australia, Canada or Mexico, are pictured as central actors.
To investigate the patterns that can be graphically observed in the earlier network, we zoom into the subset of PTAs that have not only at least one provision on e-commerce and data flows but a full chapter. Out of the ninety-nine PTAs signed since 2000, seventy-two have a chapter related to e-commerce and data flows. Seven of these PTAs are signed between Latin American countries and only available in Spanish, leaving us with sixty-three PTAs that are available in the English language. Since Singapore and Australia renewed their 2003 PTA in 2016, we only include the latter PTA in this analysis – leaving us with a subset of sixty-two PTAs.
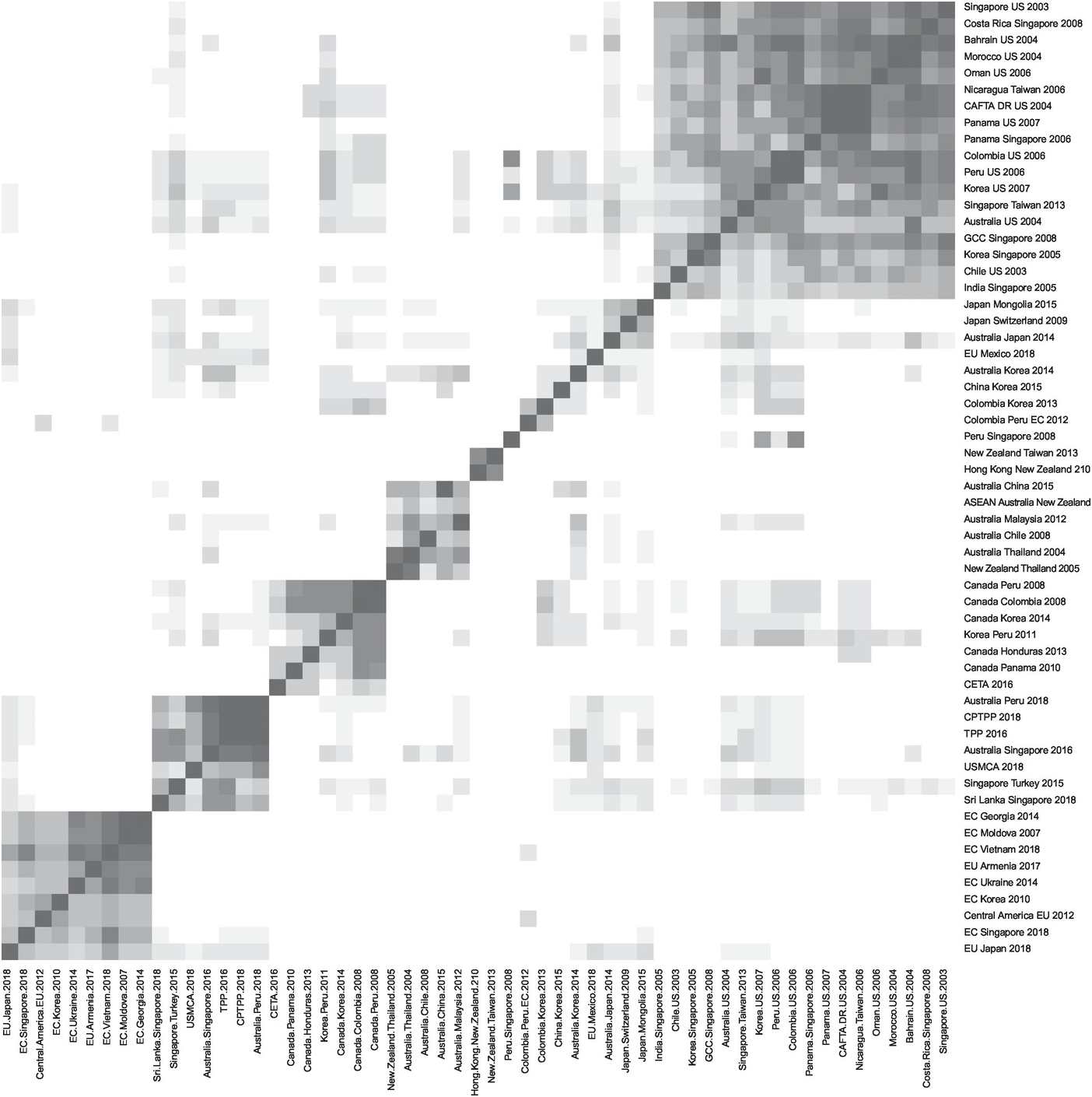
Relying on text-as-data analysis, we compare these sixty-two PTA chapters in the English language to detect potential patterns, more precisely, by employing the plagiarism software WCopyfind to measure the textual overlap between the PTA chapters. The programme allows for a number of refinements. We follow the convention to use a minimum of six consecutive identical words for a match.Footnote 17 All punctuation, outer punctuation, numbers, letter case and non-words are ignored. It should be pointed out that WCopyfind only reports the PTAs that have a minimum of matches between PTAs. In our case, the PTAs between Jordan and Singapore (2004), Canada and Jordan (2009), the Eurasian Economic Union (EAEU) and Vietnam (2015) and between Canada, and the Ukraine (2016) appear to have too little overlap with the other PTAs and were consequently dropped by the programme.
The heat map (Figure 2.9) provides a number of interesting insights. In terms of interpretation, the map colours the squares darker, the higher the textual overlap between the e-commerce and data flow chapters of two respective PTAs is. In Figure 2.9, the PTA chapters are hierarchically clustered, meaning PTAs are grouped together into clusters. The clusters and their PTAs are fairly distinct from each other and the PTAs within a cluster are broadly similar to each other. Figure 2.9 suggests that there are five main clusters. The top right cluster indicates that the United States and Singapore take similar approaches when designing their e-commerce chapters. This is likely to be the case because they have signed a PTA with one another in 2003. Out of the eighteen PTAs that are identified to be in this cluster, the United States and Singapore have signed eleven and seven, respectively. Interestingly, their PTA partners overlap only partly. While the United States and Singapore both have PTAs with South Korea and Panama, the other PTA partners are distinct. It is also interesting to note that Singapore already signed its PTAs with South Korea and Panama in 2005 and 2006 respectively, while the United States only signed its agreements with the two countries in 2007. The second PTA cluster can be found in the centre of Figure 2.9. These six PTAs appear to be following the Australian approach. Indeed, Australia is a signatory of five of these PTAs; the sixth PTA is between New Zealand and Thailand in 2004. Down and to the left is the third distinct cluster of PTAs. Out of the seven PTAs identified to be in this cluster, Canada has signed six. Somewhat surprisingly, the 2011 PTA between South Korea and Peru seems to follow a similar approach to the Canadian PTAs in this cluster. Figure 2.9 also shows that the Comprehensive Economic and Trade Agreement (CETA) between the Canada and the EU is closer to previous Canadian agreements than to EU agreements (the cluster at the bottom left). The second last cluster includes the Trans-Pacific Partnership Agreement (TPP, 2016) and the Comprehensive and Progressive Agreement for Trans-Pacific Partnership (CPTPP, 2018), as well as a number of other agreements that the (CP)TPP members have signed. Interestingly, the e-commerce chapter of the recently negotiated agreement between the United States, Mexico and Canada (USMCA, 2018) is also found to be very close to the (CP)TPP. The last cluster in the bottom left corner of Figure 2.9 includes recent agreements by the EU. Overall, the text-as-data analysis presented helps detect the small group of countries which seem to be the rule-makers in the area of digital trade.
F Zooming in on the Rule-Makers
In this section we compare these rule-makers by focusing on the number of provisions (Scope 2) and differentiate these provisions in terms of their legal language and overall ‘bindingness’. The legal language provides clues as to whether we expect more or less obligation based on words such as ‘should’, ‘shall’, or ‘may’. We differentiate between high and low obligation. Figure 2.10 provides an overview for five identified rule-makers (United States, EU, Australia, Canada and Singapore). The figure shows the average and maximum count of total provisions, as well as the average and maximum count of that have a high level of bindingness. The maximum scores might be more intuitive to interpret as countries potentially do not negotiate in their future agreements commitments below the ones already agreed upon.

Figure 2.10. Dot plots for the indicators.
Note: In the figure on non-discrimination provisions, High(max) is equal to All(max) for Australia, the EU, Singapore, the United States and others, which is why only the All(max) indicator is shown.
For scope and depth, we observe that for the so-called rule-maker group, roughly half of all commitments are phrased in legal terms that suggest high obligation. In terms of the average and maximum values for scope and depth, the EU scores lower than the other rule-makers as well as other countries. We observe a similar pattern for the flexibility indicator. Of the rule-makers, it is in particular Singapore which includes a considerable number of flexibility-related provisions. For the indicator related to consumer protection, we in particular detect that Singapore and Australia agree on legal language that signals higher obligation and therefore allows for stronger rights to protect individuals. The non-discrimination provisions are overwhelmingly commitments which come with high obligation based on the reading of the legal language. By contrast, when we turn to regulatory cooperation, we observe that the legal wording signals rather low levels of obligation, therefore these features of the treaties are practically not enforceable in case of disagreement among PTA members.
G Exploring Explanations for Treaty Design
In this section we provide graphical descriptions of a number of bivariate relations to address potential explanations for variation in PTA design. The first group of graphs (Figure 2.11) addresses the question as to whether PTA design is largely endogenous; in other words, many of the design features are related to each other, as suggested by some authors. We focus on the depth variable and explore how this is correlated with other indicators. First, we see that scope and depth are highly correlated, which is not surprising. PTAs that are paying more attention to data-related issues are also deeper. Second, deeper agreements are also going hand in hand with PTAs that advocate regulatory cooperation. This could also be interpreted as negotiators are forward-looking, promising to engage in regulatory discussion to accompany the rapidly changing regulatory environment. Deeper agreements are also more flexible, and provide for more consumer protection rights and non-discrimination clauses.
Another set of explanations can be situated at the domestic level and relates to a different set of questions: To what degree are domestic policies mirrored in international law commitments? Are countries using international law as a commitment device to bring about domestic regulatory change or are we rather witnessing a screening effect in which commitments largely reflect domestic practice suggesting some cheap talk in relation to signing agreements?Footnote 18
To address such questions, we discuss how PTA design relates to domestic digital policies. We rely on the recently published Digital Trade Restrictiveness Index (DTRI) by the European Centre for International Political Economy (ECIPE). The DTRI covers a range of fiscal, establishment, data and trading restrictions related to digital trade for sixty-four economies worldwide. The index ranges between zero and one, where zero indicates a fully open digital economy and one indicates a virtually closed digital economy. Between the TAPED database and the DTRI, we have an overlap of thirty-one countries.Footnote 19 Figure 2.12 illustrates how our main indicators relate to the DTRI. All indicators are negatively correlated with the DTRI.Footnote 20 As for those indicators that are about scope, depth and various obligations, a negative correlation casts doubts about prima facie evidence that a commitment story is at play here. More interesting are downward trends for flexibility and consumer protection; countries with lower restrictions aim for more flexibility. This would rather suggest that these countries aim to keep policy space in this area, whereas countries with higher restrictions paradoxically demand less flexibility providing some support for the idea of a commitment device. Overall, we also observe that the rule-makers, with the exception of the EU, are substantially above the trend lines.
H Conclusion
Data flow provisions have entered the universe of PTAs in the past fifteen years, although, only a third of all PTAs have commitments related to this area. This chapter presented a number of indicators related to PTA design and has mapped the design evolution over time. Letting the data speak, we discovered a number of leading actors (rule-makers) and sets of overlapping models of treaties based on textual analysis. However, we seem to be at the beginning of a period where data-relevant provisions will only increase in importance as many classic trade and trade-related provisions, such as tariffs, become relatively less important.
What are the next steps in understanding design and design variation in the domain of digital trade? First, research may explore explanations to account for variation in design based on political economy models and arguments rooted in the international relations literature; for instance, what roles do commitment concerns or power asymmetry play in agreeing upon new rules? Which interest groups are pivotal for pushing new rules? How does the competition between exporter interests and consumer protection interests define government positions entering into PTA negotiations? Second, research should pay more attention to the evolving competition among models that are being developed, in particular starting with the CPTPP and how this will affect the creation and promotion of other models, such as that of the EU. Are these models complementary or are they creating regulatory barriers? Related to this, it can be asked how leading promoters of models use PTAs to diffuse their preferred models and what the impacts on non-PTA members are when they negotiate PTAs. It would be also pertinent to explore to what degree new domestic initiatives, such as the EU General Data Protection Regulation, impact on PTA design and push for updating existing PTAs.Footnote 21
Finally, the following questions need to be raised: What is the impact of these commitments on state behaviour? How do they assist in creating new domestic policies and laws on the role of data in trade and how do they inhibit government action to restrict trade in light of consumer protection concerns? Also, more generally, how do these commitments directly or indirectly impact trade flows in goods and services and investment-location decisions for firms with large data components in their business models?
A Introduction
Movement of data across borders is central to today’s economy: it enables people to instantly connect with each other, companies to do business smoothly and governments to offer new, more efficient services to their citizens. The Internet has fundamentally changed what, with whom and how trade is conducted, and today virtually all cross-border transactions make use of the Internet or some digital component.Footnote 1 The exponential growth in data being exchanged cross-border is not set to slow down.Footnote 2 Yet, cross-border data flows are also raising both economic and political concerns related to the concentration of data, data sovereignty, privacy, law enforcement, and national security. This has posed the question of whether countries should insist that companies process data within their jurisdictions, and already many countries have enacted restrictions on the transfer of data across borders.Footnote 3
The enactment of these measures has been a topic of hot discussions across the world. On the one hand, there are actors arguing that data should flow freely and that any restriction creates unnecessary costs for businesses and the economy while also limiting the freedom of expression of people online.Footnote 4 On the other hand, certain stakeholders argue that these measures are legitimate to protect important policy objectives, such as privacy and security.Footnote 5
These discussions are not new. In fact, already in the 1980s, some companies started to worry about the potential trade-restrictive impact of new policy measures affecting the use and transfers of data justified under the rationale of national security and privacy. Yet, the debate is still open today with claims by the business community that restrictions on the transfer and use of data (both personal and non-personal) are put in place without a proper analysis of the trade-inhibiting effects and with little guarantee that security and privacy concerns are actually addressed.Footnote 6
The discussions on the trade-restrictive impact of data policies have intensified in the past years with the increasing importance of data flows for trade. As stated by the Swedish National Board of Trade, today ‘trade cannot happen without data being transferred from one location to another’.Footnote 7 Restrictions on the movement of data in practice affect not only firms in the digital sector, but in virtually any sector of the economy.Footnote 8 In fact, firms of all sizes and across all sectors use data.Footnote 9 This is even more the case considering that data per se does not have much intrinsic value, but rather acquires it when processed (often along with other data) and used to offer services, improve business efficiency or take management decisions. Therefore, it does not surprise that restrictions on data flows are perceived by companies as trade restrictions.Footnote 10 Former European Trade Commissioner Malmstrӧm also notably stated that ‘restrictions on cross-border data flows inhibit trade of all kinds: digital and nondigital, products and services. We cannot just pretend that this doesn’t exist, or that data has nothing to do with global trade’.Footnote 11
While companies have advocated the removal of data policies and the free flow of data across borders, it is yet not clear how different types of data policies impact trade, and some governments have also argued that certain policies would rather support trade by enhancing consumers’ confidence.Footnote 12 This chapter addresses the question by looking at whether data policies create a distortion on trade in services. It does so by providing a summary of the main empirical evidence on the costs of restrictions on cross-border transfers of data and domestic restrictions on the use of data. The latter category is also included in the analysis because domestic restrictions on the use of data could have an indirect impact on trade as a result of lower productivity for local firms and limited access to innovation.
The first category of restrictions on cross-border transfer of data deals with all measures that raise the cost of conducting business across borders. These measures either mandate companies to keep data within a certain border or impose additional requirements for data to be transferred abroad. More specifically, these measures include bans to transfer data abroad, local processing requirements, local storage requirements, and conditional flow regimes.Footnote 13 The common feature of these measures is that they create ‘thick’ digital borders between countries. The second group of data policies relates to the use of data domestically and includes all measures that impose certain requirements for firms to access, store, process, or more generally make any commercial use of data within a certain jurisdiction. These measures apply to both local and foreign firms alike and include data retention requirements, administrative requirements, such as the need to prepare a Data Privacy Impact Assessment (DPIA) and to hire a Data Protection Officer (DPO), data breach notifications to government authorities, and the requirement to provide government with direct access to personal data.
B Countries That Impose Stricter Data Policies
Before exploring the empirical evidence on the costs of data protectionism, this section gives a brief introduction on the level of data restrictions imposed all over the world. The indicator used in the analysis is the Data Restrictiveness Index developed in Ferracane et al.,Footnote 14 which is based on the information available in the Digital Trade Estimates (DTE) database of the European Center for International Political Economy (ECIPE).Footnote 15
The Data Restrictiveness Index summarizes the level of restrictiveness on data policies in over sixty economies and varies between zero (completely open) and one (virtually restricted) with higher levels indicating increasing levels of data restrictiveness.Footnote 16 In the analysis, data policies are defined as those regulatory measures that restrict the commercial use of electronic data. The study is limited to those measures implemented at the national or supranational level (such as in the European Union), while other restrictions imposed by local public entities are not taken into account. Data policies are divided into two main categories: (i) cross-border data policies and (ii) domestic data policies, as defined earlier. The data policies implemented in the countries are analysed and aggregated in the Data Restrictiveness Index through a detailed methodology, presented in Section E. The types of measures included in the analysis are listed in Table 3.1, with the respective weights assigned in the analysis, which are estimated based on experts’ input.
Table 3.1. Categories covered in the Data Restrictiveness Index and their weights
| Categories | Types of measures | Weights | |
|---|---|---|---|
| 1 | Cross-border flow measures | 0.5 | |
| 1.1 | Ban on transfer or local processing requirement | 0.5 | |
| 1.2 | Local storage requirement | 0.25 | |
| 1.3 | Conditional flow regime | 0.25 | |
| 2 | Domestic regulatory measures | 0.5 | |
| 2.1 | Data retention | 0.15 | |
| 2.1.1 | Minimum period | 0.7 | |
| 2.1.2 | Maximum period | 0.3 | |
| 2.2 | Subject rights on data privacy | 0.1 | |
| 2.2.1 | Burdensome consent requirement | 0.5 | |
| 2.2.2 | Right to be forgotten | 0.5 | |
| 2.3 | Administrative requirements on data privacy | 0.15 | |
| 2.3.1 | Data protection impact assessment (DPIA) | 0.3 | |
| 2.3.2 | Data protection officer (DPO) | 0.3 | |
| 2.3.3 | Data breach notification | 0.1 | |
| 2.3.4 | Government access to personal data | 0.3 | |
| 2.4 | Sanctions for non-compliance | 0.05 | |
| 2.4.1 | Monetary fine above 250,000 EUR or set as a percentage of revenue | 0.5 | |
| 2.4.2 | Jail time | 0.5 | |
| 2.5 | Other restrictive practices related to data policies | 0.05 | |
| 2.5.1 | Other restrictive practices related to data policies | 1 |
The index shows a clear trend of increasing data restrictiveness globally, driven both by raising restrictions on domestic use of data and on transfers of data (Figure 3.1).
The index shows that Russia, China, and Turkey are the most restrictive countries when it comes to the regulatory environment for using and transferring electronic data (Figure 3.2). These countries are followed by two major European economies, France and Germany, which also show high levels of restrictions on data policies.Footnote 17 Interestingly, on the one hand, all five countries are relatively large, often with a strong manufacturing base compared to their services activities. On the other hand, small services-oriented economies are found to have a more open regime on data policies.

Figure 3.2. Data Restrictiveness Index, by country (2017).
The analysis only focuses on costs of using and transferring data, while it does not take into account regulatory policies that can support data-intensive activities, such as the existence of a basic framework of data protection and consumer protection for online transactions. Future analyses should take into account these policies to have a full perspective on the ease of using and transferring data in different countries. Nevertheless, the Data Restrictiveness Index is an important step forward in the analysis of the national regimes on data policies and the development of much-needed empirical evidence on the costs of protectionism.
C Empirical Evidence on the Cost of Data Protectionism
The economic literature that discusses the cost of data policies from a trade perspective is scarce.Footnote 18 This is probably due to the fact that the topic is relatively new. Yet, the lack of in-depth empirical analysis is surprising given the extent to which trade in services today relies on data flows and considering the sizable portion of all trade in services being traded over the Internet. There are two main streams of research on data flows: one looks at the costs of data policies on local companies (mainly in terms of productivity); the other looks at the costs of these policies on foreign companies, and therefore more directly on trade.
The following section presents the empirical evidence on the costs of data protectionism on local companies in terms of jobs, productivity, and Gross Domestic Product (GDP). If data restrictions on the use and transfer of data lead to higher costs for conducting data-intense activities, then they would be detrimental for the development of local companies, impacting their productivity and, in turn, creating trade distortions. The subsequent section presents the empirical evidence on data protectionism and services trade, and therefore on whether data restrictions could create a trade barrier for foreign companies.
I Foregone Gains for Local Companies
A first set of empirical research looks at the costs of data restrictions on local firms. While it has been argued that data policies could support the development of a local information technology (IT) industry by shielding local incumbents from competition, there is no empirical evidence supporting this claim.Footnote 19 Instead data policies are found to have a negative impact on productivity and GDP.
Some studies look at the impact of data policies on jobs. While strict data policies might lead to the creation of data centres in the country imposing them, the construction of data centres is not expected to create a significant number of jobs. In most cases, data centres contain expensive high-tech equipment that is often imported and creates construction work only in the short term while employing relatively few full-time staff. In fact, the number of jobs associated with data centres has been decreasing sharply, as data centres become more automated.Footnote 20 A 2008 report found that Yahoo, Ask.com, Intuit, and Microsoft hired a total of 180 workers for their facilities – an average of 45 workers per facility.Footnote 21 Other media reports from 2011 showed that a massive USD 1 billion data centre Apple built to help power its cloud computing products created only 50 new full-time jobs.Footnote 22 In 2015, the media reported that Apple’s USD 2 billion global command centre in Mesa, Arizona, would employ 150 full-time personnel, and create between 300 and 500 construction and trade jobs.
Another study looks specifically at one policy framework regarding data, the General Data Protection Regulation (GDPR) of the European Union, and its impact on jobs. Christensen et al. use calibration techniques to evaluate the impact of the GDPR proposal on small- and medium-sized enterprises (SMEs) and conclude that SMEs that use data rather intensively are likely to incur substantial costs in complying with these new rules.Footnote 23 The authors compute these results using a simulated dynamic stochastic general equilibrium model and show that up to 100,000 jobs could disappear in the short run and more than 300,000 in the long term.
Therefore, the establishment of local data centres does not appear to lead to new jobs created in the country. Certain local companies providing data processing services would nevertheless benefit from such measures as they could leverage on a larger pool of data to process.Footnote 24 Yet, the empirical evidence suggests that the higher costs for processing data locally and the consequent loss of productivity in the overall economy would outweigh the benefits accrued to a small set of actors.Footnote 25 When data restrictions apply, local companies are not free to use the most convenient data processing provider globally and have to pay for more expensive or even duplicate services when they transfer data needed for day-to-day activities, for example, for human resources management. The higher costs of data processing are widespread and affect all businesses and consumers that are denied access to certain innovative services. The additional costs have a trickle-down impact on the macroeconomic performance of those countries implementing such rules.Footnote 26
A study by the Leviathan Security Group finds that in many countries, which are considering or have considered restrictions on cross-border transfer of data, local companies would be required to pay 30–60 per cent more for their computing needs than if they used services located outside the country’s borders.Footnote 27 The methodology used by the Leviathan Security Group compares the prices offered by local providers with the cheapest secure alternative option offered worldwide. In Brazil, for example, at the low end for 1-GB-equivalent servers, Microsoft’s price in 2015 was USD 0.024 per hour. The lowest worldwide price for 1-GB-equivalent servers – USD 0.015 per hour – would save Brazilian customers 37.5 per cent on their server costs when compared to a Brazil-exclusive solution. For a 2-GB-equivalent server, a Brazil-located solution would cost USD 0.08 per hour, and the cheapest price globally would be USD 0.03 per hour – a saving of 62.5 per cent. Averaged across the types of servers, a customer located in Brazil would pay 54.6 per cent less by using cloud servers outside Brazil instead of Brazil-located cloud computing resources.Footnote 28 Therefore, it emerges that, while certain local companies would benefit from offering their services to other local companies, overall a vast majority of local companies would incur higher costs for data processing, leading to lower productivity for the economy.
Another set of studies looks at the impact of data policies on productivity of local firms. A study by Bauer et al.Footnote 29 is the first to explore how regulatory policies related to electronic data affect total factor productivity (TFP), albeit at an industry level.Footnote 30 The authors make a first attempt at analysing this linkage econometrically by setting up a data regulatory index using existing indices of services regulation. They look at different types of policies relating to both the use and the transfer of data. The authors calculate the costs of data policies for domestic firms by establishing a link between regulation in data services and TFP at the industry-level in downstream sectors across a small set of countries. They find that stricter data policies tend to have a stronger negative impact on the downstream performance of industries that are more data intense.
A more rigorous assessment of the empirical relationship between data policies and productivity is provided by Ferracane et al.Footnote 31 The authors use firm-level TFP data across a set of developed countries and the Data Restrictiveness Index presented in the previous section. TFP is considered the most important factor for long-run GDP growth and it represents the part of economic output accounted for by efficiency and technology. The results confirm that restrictive data policies significantly harm the productivity of firms active in data-intense sectors, especially for local companies in industries and services sectors more reliant on data.
Ferracane et al.Footnote 32 is also the first empirical study to analyse cross-border and domestic data policies separately. Both types of restrictions are found to have a significant negative impact on productivity. Yet, restrictions on the domestic use of data have a marginally stronger impact on productivity compared to policies on the cross-border movement of data. Therefore, measures implemented at the domestic level with the objective to raise trust of consumers on digital services are not found to have any positive impact on productivity of firms and are rather expected to lead to a loss of productivity of local firms. On average, the study predicts that lifting data restrictions would generate a positive impact on the productivity performance of local firms with a TFP increase of about 4.5 per cent across countries (Figure 3.3), with stronger benefits in data-intensive sectors such as retail and information services.Footnote 33

Figure 3.3. Firm productivity gains from lifting data restrictions, by country.
To contextualise the magnitude of this gain in productivity, we can compare the results with a study by Iootty and others,Footnote 34 who explored the potential impact of policy reform in services using a similar approach. The predicted TFP gains that these authors obtained from lowering services restrictions are around 3 per cent. The higher gains from reforming data restrictions can be explained by the important role of intangible assets in today’s economy.
Finally, some studies look at the impact of data policies on GDP. Bauer et al.Footnote 35 employ the econometric results on TFP presented earlier in a general equilibrium analysis using the Global Trade Analysis Project (GTAP) to estimate the wider macroeconomic impact. The study measures the impact of data policies on exports, GDP, and lost consumption owing to higher prices and displaced domestic demand. The impact of proposed or enacted data restrictions on GDP is found to be substantial in all seven countries analysed in the study: Brazil (−0.2 per cent), China (−1.1 per cent), EU (−0.4 per cent), India (−0.1 per cent), Indonesia (−0.5 per cent), the Republic of Korea (−0.4 per cent), and Vietnam (−1.7 per cent). If these countries also introduced economy-wide data localisation requirements, GDP losses would be even higher: Brazil (−0.8 per cent), the EU (−1.1 per cent), India (−0.8 per cent), Indonesia (−0.7 per cent), and the Republic of Korea (−1.1 per cent). Yet, from this study it remains unclear whether the effect can be assigned to the cross-border or the domestic component of data policies.Footnote 36
Another study from Manyika et al. of 2016 looks at the contribution of cross-border data flows to GDP and finds that it has overtaken that of flows in goods in the current wave of globalisation.Footnote 37 The study states that data flows today account for USD 2.8 trillion of the total increased world GDP over the last decade, thereby exerting a larger impact on growth than traditional goods trade. Interestingly, this work does not dedicate special attention to the interlinkages that exist between data flows and trade in services but takes the former as being a separate channel that impacts the economy independent from services.
From this analysis, it emerges that data policies are not expected to create new jobs in the local economy nor to develop the local industry in data-intense sectors. On the contrary, it appears that these policies tend to lower the level of productivity of local companies and, in particular, domestic restrictions on the use of data are expected to have a stronger impact on productivity. This is not to say that local governments should remove any domestic restrictions on the use of data. These measures might be necessary for important policy objectives, such as privacy and security. Yet, the governments need to take into account the costs of these measures on local companies when designing and implementing them.
II The Foregone Gains for Foreign Companies
Turning to the impact of data policies on foreign companies and trade in services, the evidence is even more scarce. A study conducted in 2014 by the US International Trade Commission (USITC) looks at a set of restrictions on trade including restrictions on data flows. The study estimates that removing foreign barriers on digital trade would lead to an increase in US GDP of up to USD 41.4 billion.Footnote 38 The econometric model used in the analysis relies on surveys of US firms to identify restrictions to digital trade and to rank countries that enact these restrictions in order to estimate the impact that removing these measures would have on certain sectors and the overall US economy.Footnote 39 Yet, this study looks at a broader set of restrictions than data policies, including policies on platforms and content access.
Earlier work from Freund and Weinhold points to the facilitating role of the Internet on trade in services.Footnote 40 The authors state that an increase in Internet penetration by 10 per cent has the effect of increasing the growth of services trade by 1.1 percentage point for imports and 1.7 percentage point for exports. These conclusions are closely related to the question of whether data flows influence trade in services to the extent that restrictions on data can constitute a restriction on the use of the Internet.
In addition to these studies, some scholars have focused more generally on the link between data flows and trade in services. Recent work by Goldfarb and Trefler discusses the potential theoretical implications of data policies on international trade and how these policies relate to the existing models of international trade. Although this discussion is put in a wider context of artificial intelligence (AI), the authors make clear that an expanded AI industry, in which data flows are an important factor, would have clear implications for services trade.Footnote 41 Similarly, Goldfarb and Tucker point out that privacy regulations may harm innovative activities, particularly in services.Footnote 42 They present the results of previous case studies they undertook with respect to two services sectors, namely health services and online advertising. In short, both studies show that there are strong linkages between the effective sourcing and deployment of data, the services economy, and trade in services.
Mattoo and MeltzerFootnote 43 provide anecdotal evidence on the cost of GDPR on Indian firms presenting a survey by NASSCOM-DSCI in 2013.Footnote 44 The survey finds that the requirements for cross-border transfer of personal data lead to a significant loss of business opportunities for Indian firms, with nearly two-fifths of the surveyed services exporters claiming lost commercial opportunities of more than USD 10 million and another third estimating a loss between USD 1 million and 10 million.
Ferracane and van der Marel is the first empirical study that investigates more directly the impact of data policies on trade in services and confirms the findings from the NASSCOM-DSCI survey.Footnote 45 The authors investigate whether stricter data policies on use and transfers of data inhibit trade in services. The study analyses econometrically whether data policies reduce the imports of services, and in particular whether data-intense services, such as computer services, technical services, intellectual property (IP) rights, and research and development (R&D) services, are affected. For the analysis, the authors rely on the Data Restrictiveness Index presented earlier and a methodology adapted from Ferracane et al.Footnote 46 Restrictions on the cross-border movement of data are found to significantly reduce imports of services, while no statistically significant evidence is found regarding domestic data policies. This is unsurprising, as generally restrictions at the border have a direct impact on trade, while domestic restrictions only indirectly impact trade. The analysis predicts that if countries lifted their restrictions on the cross-border flow of data, the imports of services would rise on average by 5 per cent across all countries, with obvious benefits for local companies and consumers, who could access cheaper and better online services from abroad (Figure 3.4).Footnote 47 Moreover, if the two most restricted countries – Russia and China – were to remove restrictions on the cross-border movement of data, they would experience a staggering increase of services imports by more than 50 per cent.Footnote 48
These numbers amount to a substantial size of foregone gains from trade by putting in place restrictive data policies. To compare, total commercial services exports increased by around 7 per cent in 2017.Footnote 49 Most of these trade gains would be seen in data-intense sectors, such as computer services, financial and insurance services, as well as telecom and R&D services.
D Data Protectionism and the World Trade Organization
The empirical evidence presented in this chapter shows that data policies do restrict trade in services. Restrictions that apply to the cross-border movement of data have a more direct inhibiting effect on trade in services, while they also create trade distortions by impacting the productivity of local companies and industries, although to a marginally lower extent than policies related to the domestic use of data. On the other hand, domestic data policies are associated with lower productivity for local firms, and therefore impact trade only indirectly.
Yet, the evidence available is still scarce, especially in relation to the impact of data policies on trade. Ferracane and van der MarelFootnote 50 is the first study to delve in-depth into the impact of data policies on trade in services and the findings are in line with the expectation of businesses that indeed these measures reduce imports of services. The analysis predicts that, if countries lifted their restrictions on data (in particular restrictions on cross-border data flows), the imports of services would rise on average by 5 per cent.
Given the relevance of data policies for trade, it is not unlikely that a country could bring a claim before the World Trade Organization (WTO) to challenge certain data restrictions. The debate on whether data restrictions represent a trade barrier that could potentially be challenged at the WTO is, however, still in its infancy.Footnote 51 It is urgent to undertake further empirical analyses to assess the costs of these measures. This analysis should also focus on identifying which types of data policies are mostly responsible for restricting trade and also investigate whether and how restrictive data policies affect developing countries and their growth potential in the long run.
A WTO dispute could have a profound impact on the way in which the Internet develops and eventually on our society. If a dispute were to arise, the analysis could not prescind from an informed discussion on the necessity of the measures to achieve important policy objectives. While certain data policies might be necessary to protect the privacy of citizens and national security, more research is needed to assess which measures enable countries to best protect these important non-economic policy priorities and which instead create unnecessary costs on the domestic economy and on foreign companies.
The policy implications to take into account when regulating data flows are complex and include, on top of trade aspects, also technical issues related to the Internet architecture and Internet governance, human rights including data privacy and freedom of expression, development issues connected to data sovereignty as well as potentially public order issues connected to the suppression of political dissidents.Footnote 52 However, it is not yet clear how data policies contribute to achieving any of these policy objectives and these restrictions risk creating unnecessary fragmentation of the Internet.
The plurilateral discussions currently on-going at the WTO under the Joint Statement on Electronic Commerce Initiative (JSI) might offer a fertile ground for informed discussions that could engage Internet governance institutions and other stakeholders for a better understanding not only of the costs of data policies on trade in services but also on the technical effectiveness of these policies to achieve their desired objective. If anything, countries should be in a position to carefully weigh the negative impact of certain measures in order to strike the right balance between different policy priorities, without creating excessive costs for firms and, eventually, consumers.
The WTO could provide a much-needed arena for a transparent and informed dialogue on data policies, their costs and their effectiveness in achieving certain policy objectives. As stated by Selby, there is a need to ‘distinguish rhetorical claims from underlying realpolitik as to identify potential reasons why it is such a contested policy issue’.Footnote 53 Engaging the relevant stakeholders is indispensable for such an informed discussion to take place, and more empirical research is needed both in relation to the costs of data policies for the economy and on the actual effectiveness of these measures in achieving the desired policy objective. Failure to do so could lead to a fragmentation of rules on data, with consequences that go well beyond trade.Footnote 54
E Annex
The data policy index covers those data policies considered to impose a restriction on the cross-border movement and the domestic use of data. The methodology to build on the measures is listed in the Digital Trade Estimates (DTE) database, which is available on the ECIPE website (https://ecipe.org/dte/database/). Starting from the DTE database, these policies are aggregated into an index using a detailed weighting scheme, which looks at the trend of data policies for the years 2006–2016. The database and index are updated with new regulatory measures found in certain countries.
While certain policies on data flows can be legitimate and necessary to protect the privacy of the individual or to ensure national security, these policies nevertheless create a cost for trade and are therefore included in the analysis. The criteria for listing a certain policy measure in the DTE database are the following: (i) it creates a more restrictive regime for online versus offline users of data; (ii) it implies a different treatment between domestic and foreign users of data; and (iii) it is applied in a manner considered disproportionately burdensome to achieve a certain policy objective. Each policy measure identified in any of the categories receives a score that varies between zero (completely open) and one (virtually closed), reflecting their scope and level of restrictiveness. A higher score represents a higher level of restrictiveness in data policies. The data policy index also varies between zero (completely open) and one (virtually closed). The higher the index, the stricter the data policies implemented in the country.
The index is composed of two sub-indexes that cover two main types of policy measures: one sub-index covers policies on the cross-border movement of data and one sub-index covers policies on the domestic use of data. Analysing these two sub-indexes separately provides additional information on whether the impact of data policies on services trade varies depending on the nature of the policies. The full data policy index is measured as the sum of these two sub-indexes. This annex presents in detail the composition of the two sub-indexes. It shows which policy measures are found in each of the sub-indexes and the scheme applied to weigh and score each measure.
The list of measures included in the two sub-indexes is summarised in Table 3.1 presented earlier. As shown in the table, the sub-indexes are measured as a weighted average of different types of measures. The weights are intended to reflect the level of restrictiveness of the types of measures in terms of costs for digital trade. The first sub-index on cross-border data flows covers three types of measures, namely (i) a ban on data transfer or a local processing requirement for data; (ii) a local storage requirement, and (iii) a conditional flow regime. The second sub-index covers policies affecting the domestic use of data, divided in the following subcategories: (i) data retention requirements, (ii) subject rights on data privacy, (iii) administrative requirements on data privacy, (iv) sanctions for non-compliance, and finally, (v) other restrictive practices related to data policies.
The main sources used to create the database are national data protection legislations. Otherwise, information is obtained from legal analyses on data policies and regulations from high-profile law firms and from Stone et al.Footnote 55 Occasionally corporate blogs and business reports were also taken into consideration, as they can have useful information on the de facto regime faced by the company when it comes to the movement of data. All sources for each of the measures are listed in the ECIPE DTE database.
I Sub-index on Cross-Border Data Flows
The first sub-index covers those policy measures restricting cross-border data flows. Restrictions on cross-border data flows are divided in three groups: (i) ban on data transfer or a local processing requirement for data; (ii) local storage requirement; and (iii) conditional flow regime. As shown in Table 3.1, the category of bans on data transfer and local processing requirements has a score of 0.5, while the other two categories have a score of 0.25 each. The sum of the scores of these categories can go from 0 up to 1, which reflects a situation of virtually closed regime on cross-border data flows. This score is multiplied by 0.5 to create the final sub-index on cross-border data flows. The sub-index therefore goes from 0 (completely open) to 0.5 (virtually closed).
The scoring of these measures follows the scope in terms of sectoral and geographical coverage as well as the type of data affected. If a ban on transfer or a local processing requirement applies to a specific subset of data (for instance, when it applies to health records or accounting data only), this measure receives a score of 0.5. A similar score is also assigned when the restriction only applies to specific countries (for instance, when data cannot be sent for processing only to a specific country). On the other hand, when the measure applies to all personal data or data of an entire sector (such as financial services or telecommunication sector), then a score of 1 is given. Measures targeting personal data also receive the highest score because it is often hard to disentangle personal information versus non-personal information, and therefore measures targeting personal data often end up covering the vast majority of data in the economy.
If there are two measures scoring 0.5, the score is 1. If there are more additional measures, the score for this category still remains 1. This score is then weighted by 0.5 which is the weight assigned to the category of bans on data transfer and local processing requirements. For the category of local storage requirements, a similar methodology applies. When data storage is only for specific data as defined earlier, this measure receives a score of 0.5, whereas when the data storage applies to personal data or to an entire sector, it receives a score of 1. As mentioned before, the score goes up to 1 maximum and is then weighted by 0.25, which is the weight assigned to the category of local storage requirements.
For the conditional flow regimes, the measures receive a score of 0.5 in cases in which they apply to specific data, but they receive a score of 1 in case conditions that apply to personal data or an entire sector. The final score is then weighted by 0.25, which is the weight assigned to the category of conditional flow regimes.
II Sub-index on Domestic Use of Data
The sub-index on domestic use of data index covers a series of subcategories of policies affecting the domestic use of data. These are (i) data retention requirements, (ii) subject rights on data privacy, (iii) administrative requirements on data privacy, (iv) sanctions for non-compliance, and finally, (v) other restrictive practices related to data policies. Given that each of these sub-categories contains, in turn, additional subcategories, they will be presented separately. For the calculation of the sub-index, the weights assigned to the categories are shown in Table 3.1.
The categories with the highest weights (and therefore those which are considered to create higher costs for digital trade) are data retention and administrative requirements on data privacy, which are assigned a weight of 0.15 each. The category of subject rights on data privacy is assigned a score of 0.1, while the other two categories of sanctions for non-compliance and other restrictive practices are assigned a score of 0.05.
The sum of the scores of these categories can go up to 0.5, which reflect a situation of virtually closed regime on domestic use of data. The sub-index therefore goes from 0 (completely open) to 0.5 (virtually closed). As mentioned earlier, the data policy index is measured as the sum of the two sub-indexes and therefore the score for the final data policy index goes from 0 to 1.
1 Data Retention
The first category belonging to the sub-index on domestic use of data deals with measures related to data retention, which are measures regulating how and for how long a company should keep certain data within its premises. Data retention measures can define a minimum period of retention or a maximum period of retention. In the first case, the companies (often telecommunication companies) are required to retain a set of data of their users for a certain period, which can go up to two years or more in some cases. These measures can be quite costly for the companies and they are assigned a weight of 0.7. On the other hand, the measures imposing a maximum period of retention are somewhat less restrictive and prescribe the company not to retain certain data when it is not needed anymore for providing their services. They are therefore given a weight of 0.3. The country receives a score of 1 in each of the two subcategories when there is one or more measures implemented, while 0 is assigned in case of absence of these measures. Therefore, if a country implements one or more data retention requirements for a minimum period of time and no data retention requirements for a maximum period of time, the score will be 0.7. Alternatively, if the country only implements one requirement of maximum period of data retention, the score will be 0.3.
2 Subject Rights on Data Privacy
The second category belonging to the sub-index on domestic use of data covers measures related to subject rights on data privacy. The rights of the data subject are often a legitimate goal in itself, but they can nonetheless represent a cost for the firm when they are implemented disproportionately or in a discriminatory manner. This is the reason why they are covered in the index. However, they only form a smaller part of the sub-index with a weight of 0.1 as their cost on businesses is significantly low compared with other measures. Two categories of measures are identified regarding data subject rights, which are (i) a burdensome consent for the collection and use of data (with a weight of 0.5) and (ii) the right to be forgotten (with also a weight of 0.5).
If one of the measures applies, a score of 1 is given whereas a score of 0 is assigned otherwise. Regarding the first measure on the consent for the collection and use of data, a score of 1 is given only when the process for requesting consent is considered as disproportionately burdensome. This is the case when the consent has to be always written and explicit or when consent is required not only for the collection of data, but also for any transfer of data outside the collecting company. If this is not the case, then a score of 0 is assigned. Additionally, if the consent is required only in case of transfer across borders, this measure is instead reported in the first sub-index under conditional flow regime and scored accordingly.
3 Administrative Requirements on Data Privacy
The third category belonging to the sub-index on domestic use of data covers administrative requirements on data privacy. Measures included in this category are (i) the requirement to perform a data privacy impact assessment (DPIA) (with a weight of 0.3); (ii) the requirement to appoint a data protection officer (DPO) (with as well a weight of 0.3); (iii), the requirement to notify the data protection authority in case of a data breach (with a weight of 0.1); and finally (iv) the requirement to allow the government to access the personal data that is collected (with also a weight of 0.3).
For the scoring, the first three measures receive a score of 1 when a measure applies and 0 otherwise. In the case of the fourth measure, which is the requirement to allow government to access collected personal data, a full score of 1 is assigned only when the government has an open access to data stored by companies in at least one sector of the economy. However, if a government has only access to escrow or encryption keys, but still notifies access to the data, an intermediate score of 0.7 is assigned. Government direct access to data handled by the company or the use of escrow keys may, in fact, create remarkable consumer dissatisfaction that may lead to the user’s termination of service demand. Finally, if the government has to follow the same procedure that it would follow for offline access to data – that is, the presence of a court decision or a warrant, or when the request follows a judicial investigation process – then the score is 0.
4 Sanctions for Non-compliance
The fourth category of the sub-index on domestic use of data covers measures which impose a sanction for non-compliance. These measures cover both pecuniary and penal sanctions with a weight of 0.5 for each of them. The pecuniary sanctions are not considered a restriction per se, but they are accounted for in the sub-index when (i) they are above 250,000 EUR; (ii) companies have explicitly complained about disproportionately high fines or discriminatory enforcement of sanctions; and (iii) they are expressed as a percentage of a company’s domestic or global turnover. In fact, in all these cases, the sanctions have the capacity of putting a company out of business and might play an important role in the economic calculation of a company. We also list under this section those instances in which the infringement of data privacy rules can be sanctioned by closing down the business. The application of penal sanctions, such as jailtime as a result of infringement of data privacy rules, is included as a restriction. Instances in which penal sanctions are assigned as a result of identity theft and similar illegal actions are obviously not included. If any of these measures applies, then the score is 1.
A Introduction
The tension between protecting free data flows and protecting goals such as privacy and cybersecurity is vexing Internet and trade policymakers. Laws and regulations hindering data flows across borders (‘data restrictive measures’ or ‘data restrictions’) are often trade restrictive,Footnote 1 and some of these measures can violate World Trade Organization (WTO) and Preferential Trade Agreements (PTAs) obligations.Footnote 2 However, countries can justify these measures under exceptions in international trade agreements that allow governments to implement measures necessary to achieve their domestic policy objectives,Footnote 3 arguably including policies for the stability and security of the domestic Internet.Footnote 4 Nonetheless, the inherent contradiction between the globality of the Internet and the (often) inward-looking data restrictive measures creates uncertainties for data-driven sectors.Footnote 5
Modern-day digital services, such as cloud computing services, play an important role in facilitating businesses across the global supply chain, particularly by enabling them to expeditiously and efficiently move data across countries.Footnote 6 Some experts have even argued that data should be included as a ‘fifth item to the traditional list of issues addressed by trade policy: movement of goods, persons, services, capital, and data’.Footnote 7 Yet, a contradictory narrative exists, emphasising the importance of legal checks on cross-border data flows, especially the regulatory advantages of data territoriality, to inter alia ensure privacy, security and ethical use of data.Footnote 8
This article adopts a holistic perspective on the relevance of international trade law to data flows by (i) exploring the different regulatory issues pertaining to data flows that directly relate to international trade law; and (ii) recommending a framework in WTO law incorporating legal obligations on cross-border data flows alongside other relevant disciplines that enhance trust in the Internet ecosystem. Many contemporary electronic commerce issues are covered in recent PTAs; however, these PTAs often take different approaches, for example, on issues of cross-border data flows and data protection.Footnote 9 In the long run, such varied approaches may lead to fragmented rules on trade in digital services.Footnote 10 In contrast, the WTO being the only multilateral trade institution in the world, with a membership of 164 countries, is better suited to develop coherent, balanced and representative rules for a data-driven economy, as discussed further in this article. Moreover, electronic commerce–related issues are now more prominent at the WTO, including under the joint statement initiative, providing a timely opportunity to WTO members to develop new and relevant rules on data flows.Footnote 11
This article explores various elements required within the WTO framework to address the policy ramifications of data restrictive measures, focusing on General Agreement on Trade in Services (GATS). However, we acknowledge that our research query is cross-cutting and other issues might be relevant including the alignment of GATS with General Agreement on Tariffs and Trade 1994 (GATT 1994),Footnote 12 Agreement on Technical Barriers to Trade (TBT)Footnote 13 and Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS).Footnote 14 Further, where relevant, we also refer to applicable electronic commerce rules in different PTAs.
The first section explores the multilayered policy framework governing data flows and cross-border data flows identifying various policy goals typically associated with data restrictions. The following section then explains the trade-related aspects of data flow regulation by focusing on two interconnected topics: (i) the special nature of digital trade and trade in data that makes it harder to apply existing GATS provisions to digital services and (ii) those aspects of data flows that are trade related and, thus, should be addressed in a trade law framework. Finally, the last section proposes a novel WTO framework on data flows by identifying the foundational principles for data regulation and the legal provisions necessary to enable security, predictability and certainty in data flows. This section also discusses the feasibility of implementing this proposal at the WTO.
The article concludes that the WTO framework can and should evolve to accommodate the policy challenges of a data-driven economy, including adoption of binding provisions on free cross-border data flows; prohibition on data localisation; and introducing relevant provisions facilitating business and consumer trust in the digital ecosystem such as online consumer protection, privacy and cybersecurity. This framework should also include provisions centred on the specific needs of developing countries, such as providing them with technical assistance and capacity-building support, as well as facilitating digital inclusion and development. We, however, acknowledge various political constraints in adopting our proposal wholesale at the WTO, given the political sensitivity of the issues involved, and the policy preference of various countries to use PTAs to negotiate rules on data flows. Nonetheless, we believe that the existing WTO framework remains better suited and more relevant in achieving greater balance, coherence and consistency in trade rules on data flows, and that sufficient incentives exist for WTO members to meaningfully engage in reforming WTO rules to make them more relevant to the data-driven economy.
B Regulating Data Flows: A Multilayered Policy Framework
Notwithstanding the economic benefits of free data flows, countries restrict data flows to address various policy concerns. This section first discusses the most common rationales for imposing data restrictive measures, such as privacy and cybersecurity protection.Footnote 15 It then covers other aspects of data transfer that concern governments, such as illegal and unauthorised data access by foreign countries, trade secrets theft, and consumer risks in electronic transactions. Finally, the section discusses how data restrictive measures can relate to achieving domestic economic development.
I Privacy and Cross-Border Data Flows
With increasing digitalisation of services, privacy concerns have become significant.Footnote 16 Fifty-eight percent of all countries have now adopted or are in the process of adopting data protection laws.Footnote 17 Many of these laws contain provisions affecting cross-border data flows. Perhaps, the most prominent example is the European Union (EU) General Data Protection Regulation (GDPR).Footnote 18 The GDPR sets various conditions for cross-border transfer of data; for example, routine data transfers are only allowed to those countries having an equivalent level of data protection as the EU. Further, the GDPR provides for mechanisms, such as Standard Contractual Clauses and Binding Corporate Rules, prescribing additional mechanisms for individual companies to transfer personal data outside the EU,Footnote 19 and a right to be forgotten, allowing individuals to demand Internet platforms to delink their data to make it untraceable online.Footnote 20 The intended aim of these restrictions is preventing circumvention of EU’s data protection laws and increasing individuals’ control over personal data processing. Other countries, such as RussiaFootnote 21 and China,Footnote 22 have introduced explicit data localisation laws to protect privacy.
No international consensus exists on the best means to achieve online privacy, owing to the distinct socio-cultural perspectives on privacy across countries.Footnote 23 For example, the EU strongly advocates privacy as a fundamental human right,Footnote 24 including arguing for a blanket exemption for privacy laws in trade agreements.Footnote 25 EU’s domestic framework has been emulated by other non-EU countries, including India.Footnote 26 However, not all countries share a similar perspective on privacy. For instance, in China (which has adopted GDPR-like provisions), privacy is viewed as a matter of information security.Footnote 27 To the contrary, in the United States (US) and broadly, under the Asia-Pacific Economic Cooperation (APEC) Privacy Framework,Footnote 28 privacy is protected as a consumer right.Footnote 29 Finally, several developing countries are yet to implement a privacy or data protection law; thus, data management is solely the prerogative of digital service suppliers in these countries.
II Cybersecurity and Cross-Border Data Flows
The relationship between cybersecurity and data restrictions is a relatively underexplored area,Footnote 30 although one-third of new trade-related concerns relate to cybersecurity.Footnote 31 The predominant motive behind cybersecurity measures is shielding a country’s citizens and infrastructure against potential risks arising from poor cybersecurity practices. These risks may relate to consumer risks, such as compromising personal data through unauthorised hacking or cyberattacks; risks threatening public order (but not creating a war-like situation) resulting from security failures in ubiquitous technologies such as Internet of Things (IoT) and cloud computing; network attacks on the domain name system; and finally, national security risks arising from attacks on a country’s critical infrastructure including a cyberwar-like situation.Footnote 32 For example, both the Chinese and Vietnamese cybersecurity law, which inter alia mandate data localisation, equate cybersecurity to different national interests in cyberspace, covering issue-areas varying from data security to ensuring control over domestic data flows.Footnote 33
Several experts argue that ensuring security through data restrictive measures is largely ineffective. First, divergent cybersecurity laws (including technical standard requirements) across countries make it harder for suppliers of digital products to adopt best-in-class standards and practices in security.Footnote 34 For example, indigenous cybersecurity standards (particularly those that are not interoperable with globally recognised standards) hamper the ability of companies to ‘reduce network latency and maintain redundancy for critical data’,Footnote 35 and detect potential cyber risks.Footnote 36 Similarly, data localisation on grounds of security increases costs for companies in replicating their systems across different countries.Footnote 37 Second, data flow restrictions eventually increase concentration of data in specific servers, making targeting in cyberattacks much easier.Footnote 38 Finally, as long as countries remain connected to the global network, data (whether stored locally or otherwise) remains vulnerable to cyberattacks (such as distributed denial of service attacks). In restricting data storage/processing to specific jurisdictions, these risks cannot be eliminated.Footnote 39
III Protecting Consumer Rights through Data Restrictions
The discussion of the relationship between cross-border data transfers and protecting consumer rights is often subsumed under privacy-related discussions such as obtaining informed user consent for data use/processing and data interoperability across different digital media. However, protecting consumers also relates to other issues such as reliability of data analytics and prohibiting discriminatory treatment of certain consumer groups.Footnote 40 For example, the increased use of artificial intelligence (AI) raises concerns regarding exclusion of minority groups through biased algorithms.Footnote 41 Another online consumer-protection related issue is ensuring integrity and authenticity of electronic commerce transactions.Footnote 42
Regulatory frameworks addressing online consumer protection at an international/transnational level are absent because rights and remedies available to consumers are largely addressed through contracts and domestic laws.Footnote 43 The growth of digital trade, however, necessitates a coherent international framework rather than isolated domestic laws to address disputes related to cross-border e-commerce transactions.Footnote 44 Cross-border aspects of online consumer protection include issues such as failed delivery of services or inadequate quality, misuse of consumer data, and misinformation regarding specific digital products and services.Footnote 45 Since these issues can relate to cross-border activities of both service suppliers and consumers, incompatible or weak domestic frameworks often pose a hindrance to protecting consumer rights transnationally.
Governments have so far not explicitly adopted data restrictions based on consumer protection laws (e.g. to ensure a higher standard of data ethics or protection of consumers in one-sided digital service contracts). However, certain domestic laws like the GDPR incorporate elements of consumer protection such as restricting data-based consumer profiling.Footnote 46 Further, the e-Privacy Directive in the EU imposes requirements for cookies that can obstruct the free cross-border flow of data.Footnote 47 Poor cybersecurity practices of digital service providers can also pose a challenge to online consumer protection. For example, certain countries prescribe technical standards for cloud service providers in order to ensure adequate quality of cloud services for Internet users within the country.Footnote 48 Such measures, however, inhibit global business models/practices of cloud service providers, thereby restricting the free flow of data and significantly increasing compliance costs for foreign companies, in turn raising prices and reducing choice for consumers.Footnote 49
IV Access to Data for Law Enforcement
Governments consider ready access to data a priority as the Internet is critical for carrying out different human activities, including criminal ones. However, the legal position on access to extraterritorial digital data is unsettled.Footnote 50 Consequently, different governments have adopted measures to increase regulatory control over data including data localisation laws. For example, the Indian government announced that payment service providers offering services in India must localise their data operations so as to ensure regulatory oversight over all financial transactions.Footnote 51 Additionally, certain governments have tried to exercise greater control over encryption in order to obtain access to data.Footnote 52 Selby has argued that data restrictive measures are primarily driven by the competition between governments to achieve more intelligence by controlling data flows, especially given the monopoly of American technology companies.Footnote 53
The dispute involving Microsoft and the US government is an example of the difficulties associated with accessing data located outside one’s borders.Footnote 54 In this dispute, the US government issued a warrant for data located on Irish servers for domestic law enforcement activities, which Microsoft refused to comply with because the warrant related to data located outside the United States.Footnote 55 One of the key issues highlighted through this dispute was the ineffectiveness of Mutual Legal Assistance Treaties (MLATs) or letters rogatory to obtain legal access to extraterritorial data. While MLATs are time consuming and only exist between specific countries, letters rogatory are discretionary and thus unreliable.Footnote 56 This case was finally resolved by the adoption of the Clarifying Lawful Overseas Use of Data (CLOUD) Act containing a procedure for obtaining extraterritorial data based on principles of comity through executive action.Footnote 57
V Digital Industrial Policy in Developing Countries
The use of data restrictive measures as digital industrial policy is becoming popular in certain countries in Africa and India.Footnote 58 The main argument is that most developing countries are unable to benefit from global digital value chains as the intellectual property (IP) and critical data resources are largely owned by companies in developed countries.Footnote 59 In other words, public ownership of data is considered vital to achieve domestic economic interests.Footnote 60 Thus, developing countries have argued that they should be able to adopt digital industrial policies, including data localisation and content filtering measures.Footnote 61 UNCTAD has further supported this approach, including advocating that developing countries should not be compelled to support the moratorium on customs duties on electronic transmissions (which is a fundamental requirement for free flow of data), as it would cause significant tariff losses.Footnote 62 India and Africa have expressed public support for UNCTAD’s position on digital industrial policy at the WTO on numerous occasions,Footnote 63 although certain studies indicate that these policies are unlikely to be effective.Footnote 64 Unsurprisingly, certain developing countries, including Nigeria and Indonesia, have adopted data restrictive measures to create opportunities for domestic players.Footnote 65
C Trade-Related Aspects of Data Governance
The discussion in the previous section indicates the complex, multilayered nature of data governance, and the need for a holistic and multidimensional trade framework on cross-border data flows. While not all governance issues related to data transfers are trade related, certain issues including online consumer protection, cybersecurity and privacy, as discussed later, are necessary to ensure a stable regulatory framework for digital trade. Being atypical of trade agreements, these issues are not explicitly covered in WTO agreements, such as the GATS.
I Applying WTO Disciplines to Data Restrictive Measures
Several scholars have examined how GATS applies to data restrictive measures and this section does not replicate such efforts.Footnote 66 For example, if a dispute were to arise on a data restrictive measure, legal obligations on national treatment and domestic regulation would be relevant if the measure favoured domestic services and service suppliers or imposed unreasonable compliance requirements on foreign services and service suppliers.Footnote 67 Similarly, restricting or banning cross-border data flows in sectors where members have made explicit GATS commitments could violate market access obligation.Footnote 68 GATS also encourages transparency of regulations.Footnote 69 Lastly, the general exceptions in Article XIV GATS can be relevant in distinguishing blatantly protectionist data restrictive measures (which are impermissible) from legitimate policy measures (falling within the scope of these exceptions). Thus, theoretically, the principles underlying GATS support an open environment for data flows without restraining WTO members from regulating the Internet for legitimate reasons.Footnote 70
However, applying the pre-Internet era GATS disciplines to data-related disputes is challenging. Wu terms this as the ‘problem of interpretative technological translation’,Footnote 71 i.e. applying GATS to technologies not envisioned at the time these rules were framed.Footnote 72 First, cross-border data flows relate to not only trade in services but also trade in goods.Footnote 73 Segregating the goods-related and services-related aspect of measures can be challenging when services form an integral part of a good (e.g. IoT). Second, interpreting whether a member’s commitments in its GATS Schedule on national treatment and market access cover data flows in a certain sector is tough due to the cross-cutting nature of digital services.Footnote 74 Third, the proximity of service suppliers and consumers in the digital supply chain leads to highly intrusive (and sometimes, inefficient) data restrictive measures that are also trade inhibiting.Footnote 75
II Trade-Related Aspects of Data Flows
Given that GATS is not sufficiently adaptable to a data-driven economy, we delve deeper into aspects of data regulation that are trade related but remain inadequately addressed in GATS.
1 Privacy Protection and GATS
As discussed earlier, privacy protection is the most common rationale for imposing data restrictions. Arguably, GATS acknowledges the importance of privacy protection under the exceptions contained in Article XIV(c)(ii) GATS:
(N)othing in this Agreement shall be construed to prevent the adoption or enforcement by any Member of measures:
(c) necessary to secure compliance with laws or regulations which are not inconsistent with the provisions of this Agreement including those relating to:
(ii) the protection of the privacy of individuals in relation to the processing and dissemination of personal data and the protection of confidentiality of individual records and accounts.Footnote 76
Further, paragraph 5(d) of GATS Telecommunications Annex states:
[A] Member may take such measures as are necessary to ensure the security and confidentiality of messages, subject to the requirement that such measures are not applied in a manner which would constitute a means of arbitrary or unjustifiable discrimination or a disguised restriction on trade in services.Footnote 77
The exceptions for ‘protection of privacy of individuals’ in Article XIV(c)(ii) GATS and ‘ensuring security and confidentiality of messages’ in the Telecommunications Annex indicate that WTO members were aware of and recognised the fundamental importance of privacy as a policy objective and, therefore, considered them permissible even if they violated trade obligations of a WTO member. Further, Article XIV(c)(ii) GATS does not prevent members from choosing a specific standard of privacy/data protection, but rather requires examination of whether the adopted measure/standard on data protection is indeed necessary to achieve compliance with domestic privacy/data protection laws.
However, Article XIV(c)(ii) GATS cannot ensure that all WTO members adopt a sound and robust framework on data protection/privacy, but only protects their right to impose restrictions/measures to safeguard privacy of individuals and/or protect confidentiality and security of electronic transmissions. Online privacy is a fundamental precondition for open, transparent and secure flows of data across borders.Footnote 78 For example, consumers are likely to engage in digital trade only when they trust that the digital service suppliers adequately prevent unauthorised access or misuse of their data. Similarly, GATS does not address trade barriers resulting from variations in privacy frameworks across countries, as it does not specifically mandate WTO members to develop mutually compatible frameworks on privacy. For example, the mechanism available under Article VII GATS for mutual recognition of ‘standards or criteria for the authorization, licensing or certification of services suppliers’ has never been utilised for ensuring compatibility of privacy/data protection frameworks of WTO members.Footnote 79
2 Cybersecurity and GATS
Another common rationale for imposing data restrictions is protecting security of data or the cyber networks within a country. This rationale is also related to broader national security requirements.Footnote 80 Like privacy protection, cybersecurity may be covered under Article XIV GATS, although cybersecurity is obviously not explicitly mentioned.Footnote 81 However, the exception could apply if a cybersecurity measure is necessary to maintain public order (Article XIV(a) GATS).Footnote 82 For example, certain studies suggest that the entire public utility network of a country (e.g. electricity supply) can be brought down by malware attacks by targeting smart devices used at home.Footnote 83 Another issue (particularly in trade in goods) is restrictions on encryption or forced adoption of specific encryption standards and its adverse impact on foreign suppliers.Footnote 84 Such measures are detrimental to enhancing trust of Internet users and are likely to render digital products more vulnerable to cyber intrusions.Footnote 85
Further, Article XIV(c)(ii) GATS could be interpreted to cover certain data/Internet security measures:
(N)othing in this Agreement shall be construed to prevent the adoption or enforcement by any Member of measures:
(c) necessary to secure compliance with laws or regulations which are not inconsistent with the provisions of this Agreement including those relating to:
(i) the prevention of deceptive and fraudulent practices or to deal with the effects of a default on services contracts;
(iii) safety.Footnote 86
Domestic laws related to ‘deceptive and fraudulent practices’, ‘default on services contracts’ and ‘safety’ in Article XIV(c) GATS can be creatively and flexibly interpreted to cover both cybersecurity and consumer protection–related measures. For example, a government can ban insecure and unencrypted services or impose data flow restrictions on foreign companies (particularly in sensitive sectors) to ensure that consumer data is not wrongfully used abroad. Further, since Article XIV(c) GATS is not exhaustive, a member may argue that its data restrictive measure is necessary to ensure compliance with domestic cybersecurity laws.
Like online privacy, cybersecurity is an essential component of ensuring free and open environment for global digital trade. However, the earlier mentioned exceptions do not require WTO members to adopt regulatory frameworks or enhance international cooperation on cybersecurity. While certain discussions at the WTO have centred on ensuring that technical compliance requirements for digital products are in conformity with international technical standards (such as under the TBT agreement),Footnote 87 similar requirements have not been explicitly included in GATS.
3 Online Consumer Protection and Digital Trade
In addition to privacy protection and cybersecurity, online consumer protection is also important to ensure an open, transparent and secure environment for digital trade and data flows.Footnote 88 For example, when buying online, consumers directly interact with service suppliers, and thus may be more vulnerable to one-sided contracts. Further, protecting Internet users from fraudulent transactions, breaches, spam and malware attacks, and data misuse by service providers and third-party advertising services is important for digital trade.Footnote 89 In case of divergent consumer protection laws across countries (e.g. rules related to enforcement and authentication of electronic contracts), businesses and consumers both face legal uncertainty when transacting online.Footnote 90 While multinational companies such as Amazon can tailor consumer contracts on a country-by-country basis and even build local servers (where such laws exist), smaller companies cannot do so.
GATS does not set any requirements for countries to adopt consumer protection laws in order to ensure adequate quality or security of services and arguably only provides for an exception under Article XIV(c)(ii) GATS to restrict data flows in consumer interests. For achieving liberalisation of digital trade, adopting internationally recognised models of consumer protection and active international cooperation on online consumer protection among WTO members is more beneficial and effective than unilateral domestic restrictions. However, to date, these questions have not been addressed at the WTO.
4 GATS Compatibility of Digital Industrial Policy
Certain countries, as discussed earlier, impose data restrictions as a tool of industrial policy. GATS prohibits members from imposing data restrictive measures in those sectors where they have made explicit commitments on national treatment and market access,Footnote 91 and also prohibits arbitrary and discriminatory measures that are unconnected to domestic regulatory objectives.Footnote 92 However, given the importance of protecting developing countries’ interests at the WTO, especially their meaningful integration into the global economy,Footnote 93 WTO members can consider if certain data restrictive measures are beneficial to developing countries and least-developed countries (LDCs). For example, some developing countries/LDCs may argue that they need more time to open specific sectors to global competition. However, a necessary part of bridging the digital divide between developed and developing countries involves improving domestic access to high-quality and competitively priced digital services and platforms.Footnote 94 Data restrictive measures reduce consumer access to competitive digital services and could backfire in the long run and inhibit the growth of developing countries. Thus, investigating the necessity of data restrictive measures to enable digital development of developing countries is important.Footnote 95
5 Data-Related Issues Outside the Scope of WTO Law
Certain aspects of data regulation cannot be addressed by WTO law even if they have a trade-restrictive impact. For example, in examining whether a measure is necessary to protect public morals under Article XIV(a) GATS, WTO panels and the Appellate Body have taken a deferential stance towards online censorship, as in China – Publications and Audiovisual Products.Footnote 96 Thus, WTO members are largely free to adopt measures censoring content online provided they comply with Article XIV(a) GATS. Given that the evaluation of the data content is based on the specific socio-cultural circumstances of each country, leaving out such issues from the ambit of trade agreements is judicious. However, further dialogues in the Internet policy and international human rights community on the necessity and the most appropriate tools for online censorship might better inform the application of Article XIV(a) GATS. WTO law also cannot address the international cooperation framework for accessing extraterritorial data as it is better addressed by international treaties such as MLATs or other initiatives, such as the CLOUD Act, as mentioned earlier.
D Devising a WTO Framework on Data Flows
An ideal digital trade framework should facilitate free data flows, digital innovation, and healthy competition in the global digital market without interfering with a country’s right to legitimately regulate the Internet.Footnote 97 In this section, we propose a WTO framework on data regulation addressing various trade-related aspects of data flows that fits better into such an ideal digital trade framework. The suggested framework is similar to certain recent PTAs but with specific modifications that adapt to the diversity of the WTO membership. The following first section discusses the foundational principles of data regulation in international trade law, while the subsequent section advances our proposals for reform in WTO law.
I Foundational Principles of Data Regulation in International Trade Law
1 Fostering Digital Trust at a Domestic and Transnational Level
WTO disciplines should enable ‘digital trust’, which in turn requires preserving user privacy, protecting consumers against spam, fraudulent transactions and cybersecurity attacks, and facilitating business trust, for example, providing adequate IP protection and a competitive environment for digital innovation.Footnote 98 To contribute to digital trust, the WTO framework should (i) facilitate increased transnational dialogues and international regulatory coordination and cooperation on relevant issues, such as data flows, cybersecurity and privacy; and (ii) safeguard policy space necessary for countries to enable and maintain Internet trust in domestic cyberspace, provided they meet the requirements of reasonableness (e.g. under Article VI GATS) and are not disguised protectionist measures (e.g. evaluation under Article XIV GATS). In our view, this two-fold approach to enable digital trust will promote ‘trustworthy information relationships’ in the global ecosystem for cross-border data transfers.Footnote 99 However, we do not argue that WTO rules are alone sufficient to ensure digital trust but rather that they could contribute to the global framework for data regulation.Footnote 100
2 Ensuring Interoperability and Transparency to Facilitate Free Flow of Data
WTO disciplines should ensure interoperability and transparency of Internet regulations/regulatory frameworks to facilitate data flows and greater accountability in digital networks. These twin objectives are particularly important for highly beneficial but risky technologies such as AI and IoT.Footnote 101
Article VII GATS provides for mutual recognition of ‘standards or criteria for the authorization, licensing or certification of services suppliers’. Although non-binding, Article VII:5 GATS recognises the need for more international coordination between WTO members on domestic regulations pertaining to licensing, certification or authorisation of service suppliers:
Wherever appropriate, recognition should be based on multilaterally agreed criteria. In appropriate cases, members shall work in cooperation with relevant intergovernmental and non-governmental organisations towards the establishment and adoption of common international standards and criteria for recognition and common international standards for the practice of relevant services trades and professions.
Varying standards of privacy and security across countries create impediments to cross-border data flows. While harmonising privacy and cybersecurity laws can be difficult and perhaps impossible due to the divergence of views/practices across different systems, cooperation and interoperability between different regulatory systems is achievable.Footnote 102 The WTO can learn from the experience of other international institutions such as United Nations Commission on International Trade Law (UNCITRAL) and the International Institute for the Unification of Private Law (UNIDROIT) that have used similar techniques in various areas of public and private international law respectively to obtain interface between different regulatory frameworks.Footnote 103 Further, developing new rules under Article VI:5 GATS relating to ‘qualification requirements and procedures, technical standards and licensing requirements’ on data flows can incentivise greater recognition of regulatory frameworks among WTO members.Footnote 104
Another fundamental requirement that must be addressed in WTO law is transparency of data regulations. Despite a binding legal mechanism under Article III GATS, several WTO members adopt ambiguously worded data restrictive measures, causing considerable uncertainty for businesses and consumers alike. More mechanisms should be devised to increase governmental accountability at the WTO for their data regulations, including effective use of the Trade Policy Review mechanisms and discussions in various WTO committee meetings. Through such informal and open dialogues, members may be able to build international cooperation on relevant issues, thereby automatically reducing the tendency to adopt opaque data regulations.
3 Exploring New Regulatory Approaches in WTO Law
The third fundamental component necessary to adapt WTO law to the data-driven economy is to explore innovative and inclusive approaches in digital trade and data regulation that consider the multi-stakeholder nature of the Internet governance regime, particularly the central role of private sector in ensuring openness and security of data flows.Footnote 105 Different experts have argued that the regulatory framework for data flows requires a more sophisticated approach than traditional multilateral processes. For instance, Shackelford and others argue that majority of privacy and security issues related to digital technologies require poly-centric governance, including a self-regulatory approach in highly technical areas.Footnote 106 Kuner emphasises the significance of private sector instruments (including codes of practice and contractual clauses) in regulating cross-border data flows,Footnote 107 and argues that regulation of data flows is ‘a form of legal pluralism’, with no single authoritative framework.Footnote 108 Segura-Serrano argues that data regulation requires a hybrid approach involving a mixture of prescriptive and self-regulatory approaches.Footnote 109
Adopting a co-regulatory or hybrid regulatory approach (involving the private sector and multi-stakeholder organisations) at the WTO can be challenging. For example, the WTO has not traditionally liaised with multi-stakeholder institutions, such as those prevalent in Internet policy community. Similarly, WTO rules do not refer to private standards or industry best practices although they may be commonplace in the digital world.Footnote 110 However, the WTO can liaise with multilateral institutions in relevant areas. For instance, under GATT, various mechanisms are established for consultation with the International Monetary Fund (IMF) for areas related to currency valuation and exchange.Footnote 111 Similarly, regarding applying WTO disciplines to environmental issues, WTO members have undertaken various commitments to engage with multilateral environmental institutions.Footnote 112 There is no reason why a similar approach cannot be followed in the area of Internet and data regulation where multi-stakeholder institutions and private sector play a key role, for example, in technical standard-setting.
More specifically, some form of regulatory innovation is essential at the WTO to respond to the needs of data-driven sectors. For example, in certain cases, multi-stakeholder discussions involving Internet experts can enable a more balanced evaluation of cyber risks in digital services and the necessity of certain trade restrictive measures to address these cyber risks. This approach might be more effective than imposing unilateral data restrictions, which are not only highly trade restrictive but also have limited impact on ensuring digital trust and innovation.Footnote 113
II Reforms in the WTO Framework for Data Regulation
The next section discusses various rules that we think should be included in a new WTO framework governing data flows. Many of the proposed rules in our framework somewhat resemble the rules in certain recent PTAs, such as the United States–Mexico–Canada Agreement (USMCA) and Comprehensive and Progressive Agreement for Trans-Pacific Partnership (CPTPP). However, we incorporate additional suggestions and modifications to make these rules more balanced and representative of interests of developing countries, as well as address fundamental public policy challenges in data regulation, including protecting regulatory autonomy of WTO members, as and when necessary.
1 Horizontal Obligation on Cross-Border Data Flows and Data Localisation
WTO law should incorporate horizontal obligations on ensuring free flow of data for the purposes of conducting regular business transactions and to prohibit forced data localisation. Data flows are fundamental for the growth of the digital economy and are required for both services and manufacturing sectors. In the age of cloud computing, when companies manage data resources in real time based on server capacities and real-time demands on server space, prohibitions on cross-border data flows and geographical restrictions on data storage can be a significant trade barrier. Thus, we recommend a horizontal obligation for enabling cross-border data flows for purposes of conducting businesses and prohibition on data localisation measures.
Provisions on data flows can be found in recent PTAs, such as Peru–Australia Free Trade Agreement (PAFTA),Footnote 114 USMCA, CPTPP, etc.Footnote 115 We discuss the CPTPP later as successive PTAs contain similar provisions. Article 14.11(2) CPTPP states: ‘Each Party shall allow the cross-border transfer of information by electronic means, including personal information, when this activity is for the conduct of the business of a covered person.’ Further, CPPTPP Article 14.13(2) provides,: ‘No Party shall require a covered person to use or locate computing facilities in that Party’s territory as a condition for conducting business in that territory.’
Both these provisions are, however, rightly subject to an exception in Article 14.11(3) and Article 14.13(3) CPTPP, respectively to ‘adop[t] or maintai[n] measures’ inconsistent with Article 14.11(2) and Article 14.13(2) in order to achieve a ‘legitimate public policy objective’, provided that such measure is ‘not applied in a manner which would constitute a means of arbitrary or unjustifiable discrimination or disguised restriction on trade’ and ‘does not impose restrictions on transfers of information/the use or location of computing facilities, greater than required to achieve the objective’. We recommend a similar provision within the WTO framework.
Although Article 14.11(3) and 14.13(3) CPTPP are similar to Article XIV GATS and Article XX GATT, clarifying the scope of ‘legitimate public policy objective’ with an illustrative list will be helpful. For example, the list should specify that cybersecurity, privacy, online consumer protection and protecting public order qualify as ‘legitimate public policy objectives’. Further, the exceptions available under Article XIV and Article XIVbis GATS should clearly remain applicable for examination of data restrictive measures. For example, a WTO member should remain free to restrict data flows or require data localisation if it is necessary for achieving compliance with domestic laws, for protecting public morals or maintaining public order, or to protect essential security interests.
Given the delicate issues involved in data regulation, clarity in obligations and exceptions on data flows ensures that policy space of WTO members remains untouched. For example, in the Financial Services Chapter of the USMCA, a provision clearly acknowledges the data access to regulators should not be prohibited by data localisation measures. Article 17.20(1) states in this regard:
No Party shall require a covered person to use or locate computing facilities in the Party’s territory as a condition for conducting business in that territory, so long as the Party’s financial regulatory authorities, for regulatory and supervisory purposes, have immediate, direct, complete, and ongoing access to information processed or stored on computing facilities that the covered person uses or locates outside the Party’s territory.
This provision is extremely helpful in clarifying both that (i) regulatory and supervisory authorities should have access to data for authorised and legal purposes; and that (ii) data localisation is not essential to ensure access to data.
2 Enabling International Cooperation on Cybersecurity Issues
Provisions related to relevant trade-related aspects of cybersecurity should be included in WTO law to facilitate an open and secure environment for cross-border data flows. However, we do not recommend that such rules prescribe any specific standards for cybersecurity.
First, WTO members should consider a mandatory requirement for international cooperation on cybersecurity issues.Footnote 116 This is not entirely new to the WTO; for instance, WTO members have taken concrete action to ensure greater international cooperation on trade-related environmental issues.Footnote 117 Further, given the unique role of private sector in devising and implementing cybersecurity standards, WTO rules should also provide for international cooperation between its members and non-state organisations that play a key role in international governance (including multi-stakeholder bodies).Footnote 118 For example, relevant institutions should be consulted at the stage of developing these rules and, later, if trade dispute related to a cybersecurity measure were to arise.Footnote 119 Although a little unconventional, recent years have seen WTO being more open to liaise with non-state entities, especially on digital issues. For example, in 2017, a new initiative was launched by WTO and two private sector–led multi-stakeholder institutions, World Economic Forum and Electronic World Trade Platform (e-WTP) entitled ‘Enabling Electronic Commerce’ to facilitate public–private dialogues on electronic commerce issues.Footnote 120
Second, rather than enforcing domestic cybersecurity standards, WTO members should be encouraged to give preference to internationally recognised standards and best practices in cybersecurity over indigenous cybersecurity standards. Such provisions are atypical of trade agreements, especially for trade in services.Footnote 121 Recent PTAs, such as the USMCA, recognise the importance of adopting internationally recognised cybersecurity standard. Article 19.15(2) states that:
Given the evolving nature of cybersecurity threats, the Parties recognize that risk-based approaches may be more effective than prescriptive regulation in addressing those threats. Accordingly, each Party shall endeavor to employ, and encourage enterprises within its jurisdiction to use, risk-based approaches that rely on consensus-based standards and risk management best practices to identify and protect against cybersecurity risks and to detect, respond to, and recover from cybersecurity events.Footnote 122
However, adopting a similar provision in the WTO framework will be much tougher and is not recommended because of lack of consensus on whether a risk-based approach is most appropriate to address cyber risks.
Finally, all WTO members should be required to adopt a basic level of cybersecurity regulation to prevent countries from becoming havens for criminal or illegal use of digital services and data. This requirement should not prevent members from adopting stricter regulations on cybersecurity as long it is not arbitrary, discriminatory or unreasonable.
3 Requiring Privacy Frameworks and Promoting Mutual Recognition Mechanisms
Requiring all WTO members to adopt a basic regulatory framework for protection of personal information or privacy protection is fundamental for ensuring free flow of data. Meltzer and Mattoo argue that the privacy exception available under Article XIV(c)(ii) GATS is insufficient as it pressurises WTO panels to adjudicate on sensitive privacy issues, which is particularly difficult given that ‘data-source countries’ are unlikely to ‘accept one-sided limits on their right to protect privacy’.Footnote 123 To deal with this uncertainty and distrust in other members’ privacy frameworks, many countries introduce stringent privacy measures that decrease competitiveness and efficiency of both foreign and domestic digital businesses. Mattoo and Meltzer argue that increasingly more countries are likely to seek bilateral arrangements, such as the data transfer agreement between the EU and the United States (EU–US Privacy Shield) to enable cross-border data flows while ensuring privacy remains protected abroad.Footnote 124 They also argue that international recognised standards and guidelines, such as the OECD Privacy Framework, provide a basis for aligning privacy laws across countries.Footnote 125 However, we see more widespread benefits if, under the ongoing plurilateral negotiations, WTO members considered a provision requiring adoption of a basic domestic privacy framework in line with internationally recognised standards and guidelines.
Recent PTAs contain rules on privacy/data protection, although two different approaches can be seen in EU-led PTAs and US-led PTAs.Footnote 126 For example, the USMCA contains the following provision (building on a similar provision in CPTPP):
To this end, each Party shall adopt or maintain a legal framework that provides for the protection of the personal information of the users of digital trade. In the development of its legal framework for the protection of personal information, each Party should take into account principles and guidelines of relevant international bodies, such as the APEC Privacy Framework and the OECD Recommendation of the Council concerning Guidelines governing the Protection of Privacy and Transborder Flows of Personal Data (2013).Footnote 127
The specification of OECD and APEC privacy principles as benchmarks could be controversial in a multilateral context, given that they are considered lenient in comparison to the GDPR and similar frameworks. To the contrary, EU FTAs are generally cautious in specifying appropriate rules on data protection, although they require full compatibility with international standards, in the sense that ‘the Parties agree that the development of electronic commerce must be fully compatible with the international standards of data protection, in order to ensure the confidence of users of electronic commerce’.Footnote 128
The EU has advocated an even stronger provision on privacy protection in a recent proposal on data flows: ‘Each Party may adopt and maintain the safeguards it deems appropriate to ensure the protection of personal data and privacy, including through the adoption and application of rules for the cross-border transfer of personal data. Nothing in this agreement shall affect the protection of personal data and privacy afforded by the Parties’ respective safeguards.’Footnote 129
This provision provides a carte blanche for countries to adopt a privacy framework, irrespective of their trade commitments. We recommend a more balanced provision in WTO law, somewhere in between the lenient provision in USMCA and the provision proposed by EU, which could also increase disguised protectionist measures. The PAFTA offers an example of a more balanced framework on privacy that accommodates varying perspectives. It provides in Article 13.8(2): ‘To this end, each Party shall adopt or maintain a legal framework that provides for the protection of the personal information of the users of electronic commerce. In the development of its legal framework for the protection of personal information, each Party should take into account principles and guidelines of relevant international bodies.’
Such a provision will provide ample opportunity for WTO members to discuss appropriate principles and guidelines in relevant institutions as well as accommodate evolving norms in this field.Footnote 130 Further, such a provision does not inhibit members from undertaking institutional innovations to protect privacy beyond the basic requirements, provided they are not arbitrary or discriminatory in nature.Footnote 131
Additionally, WTO members should be encouraged to use the mechanism available under Article VII GATS to develop mutual recognition schemes for privacy certifications of different members to ensure greater interoperability within the multilateral system. However, in the short run, they are likely to be bilateral or regional initiatives between like-minded members till greater consensus evolves on privacy issues. Finally, WTO could liaise with institutions dealing with international cooperation for development of privacy rules/standards and cross-jurisdictional privacy enforcement, such as International Conference of Data Protection and Privacy Commissioners.
4 Incorporating Consumer Trust Enhancing Measures
Consumer trust is a fundamental requirement for digital trade. This requires not only strong domestic laws but also persistent international cooperation and engagement across relevant stakeholders, such as private companies, consumer advocacy organisations and consumer protection agencies. Further, the types of risks faced by consumers is also changing in a digital world and includes dangerous cybercrimes, such as distributed denial of service attacks, phishing attacks, hacking, identity theft and cyberstalking.Footnote 132 Dealing with these issues requires WTO’s engagement with other relevant institutions, such as the International Consumer Protection Enforcement Network, UNCITRAL and other regional bodies with expertise on consumer protection issues, such as the OECD.
WTO rules do not address online consumer protection issues directly and, hence, we recommend new rules to integrate this dimension in WTO framework. First, all WTO members should be required to adopt a basic regulatory framework on online consumer protection, including providing sufficient remedies to e-commerce users and ensuring that businesses provide adequate quality of digital products. The UNCITRAL Model Law on Electronic Commerce could be incorporated by reference in WTO law. Second, WTO members should adopt a mandatory cooperation mechanism for addressing the transnational aspects of online consumer protection, including information sharing and providing assistance for cross-border enforcement of consumer protection laws.Footnote 133 Implementing such provisions might require systematic changes to domestic laws of several developing countries and, therefore, they might need technical assistance, as earlier noted.
Several PTAs already contain provisions on online consumer protection, although many of them are non-binding.Footnote 134 Further, these provisions are loosely worded and do not incentivise countries to develop meaningful cooperation on online consumer protection issues. Being a multilateral institution, the WTO is better placed to facilitate increased dialogue between consumer protection (and other relevant) regulators to ensure effective international cooperation in the field.
5 Enabling Digital Innovation and Promoting Business Trust
WTO rules should also incorporate mechanisms to improve business trust to support a data-driven economy. For example, interoperable and transparent standards in data regulation can facilitate business trust. To achieve this, WTO members could consider adoption of TBT-like disciplines in context of trade in services. For instance, all members should be required to adopt only such technical standards in their digital services that are consistent with internationally recognised standards.Footnote 135 Further, unreasonable standards constituting unnecessary barriers to trade and more burdensome than necessary to achieve a policy objective such as ensuring privacy or security should be prohibited.Footnote 136 Such provisions could reduce the use of indigenous domestic standards that disrupt data flows.
WTO members could also be required to consider/use only internationally recognised standards in framing domestic regulations, including imposing standards for data security and privacy.Footnote 137 This obligation could be difficult to implement in practice because multi-stakeholder and private sector–driven standards are prominently used in data operations but have little recognition in WTO law. For example, the data routing architecture of the Internet is largely based on protocols established by the Internet Engineering Task Force (IETF), a multi-stakeholder organisation developing voluntary Internet standards. Similarly, cybersecurity standards are largely developed by private sector. In fact, experts argue that Internet-related standards function better when they are open and driven by market competition rather than unilateral measures.Footnote 138 To address this gap, an arrangement similar to the TBT Code of Good Practice could be adopted in context of GATS.Footnote 139 This would provide an opportunity for private or multi-stakeholder standards to gain greater recognition at the WTO while ensuring that these standards are being formulated with transparency, participation and accountability.Footnote 140 For example, the International Organization for Standardization (ISO), a private standard-setting organisation, has a strong partnership with WTO and plays an instrumental role in harmonising standards in goods through contributions to the WTO committee meetings and providing reports to WTO members.Footnote 141
Additionally, certain PTAs, such as the CPTPP and USMCA, include provisions to enhance business trust in the context of digital services by protecting the source code and vital digital assets of foreign companies from unauthorised disclosure.Footnote 142 In the USMCA, this provision is extremely broad and prohibits governments from requiring access to both source code and algorithms as a condition of market access.Footnote 143 However, similarly worded provisions can pose problems in the multilateral context because (i) many developing countries consider technology transfer as an important prerequisite for bridging the existing digital divide between developing and developed countries (an issue requiring further debate and negotiations);Footnote 144 and (ii) certain countries fear that algorithms and technical codes underlying digital services may be discriminatory, insecure or allow unauthorised data access to certain countries or groups, and therefore, should be scrutinised further.Footnote 145
To address the above concerns, we recommend a provision in WTO law that would prohibit forced disclosure of source code and algorithm, but subject to an exception allowing governments to access this information for regulatory purposes, such as checking for discriminatory algorithms, auditing security of digital services and for judicial proceedings or governmental investigations.Footnote 146 Article 19.16(2) USMCA is a good example as it has been carefully constructed to ensure that governments can access source code and algorithms for regulatory purposes, such as checking for discriminatory algorithms, for patent applications/disputes,Footnote 147 for criminal investigations, and auditing security standards of digital services as part of domestic investigations or inspections. However, it does not specify that parties could be required to modify the source code, for example, when an investigation reveals that a company has violated domestic laws or if the security standards are below par, or where the algorithms are discriminatory.
6 Relevance of Special and Differential Treatment for Developing Countries and LDCs
Certain developing countries have claimed that data restrictive measures are necessary to develop their domestic digital sector and protect their economic and social interests, for instance preventing tariff losses resulting from the moratorium on customs duties on electronic transmissions. The WTO is an excellent forum for developing countries to present evidence on the benefits of data restrictive measures in the short run vis-à-vis the losses to their domestic consumers and businesses as well as other measures necessary to promote greater digital inclusion. However, where exceptions are made for developing countries and LDCs to impose data restrictive measures, such as through special and differential treatment, they should be evidence-based and time-bound.
Certain developing countries and LDCs may have inadequate capacity to enforce a framework for data regulation due to insufficient expertise on privacy and cybersecurity. Such members should be provided additional time to make a binding commitment on data flows. For instance, the Trade Facilitation Agreement allows for staggered implementation of obligations, so as to provide more time to developing countries and LDCs to initiate reforms in their domestic system before being fully bound.Footnote 148 Further, WTO members should also agree on mandatory technical assistance programmes and capacity-building support for developing countries and LDCs with inadequate regulatory capacity on relevant issues. None of the PTAs deal with development-related concerns in digital trade, particularly enforcing stronger obligations on developed partners to assist developing countries and LDCs. This deficiency can, however, be addressed better through the ongoing WTO plurilateral initiative, which also brings together several developing countries and LDCs (e.g. under the Friends of E-commerce for Development.)
III The Path Ahead for Rules on Data Flows at the WTO
WTO members are currently considering two separate mechanisms to reform WTO rules on electronic commerce. First, GATS itself could be reformed using existing mechanisms. For example, under Article XVIII GATS, members could adopt additional commitments on data flows, akin to the Telecommunications Reference Paper.Footnote 149 WTO members could also consider adopting dedicated domestic regulations on electronic commerce under Article VI GATS. Certain members have argued for expanding existing GATS commitments on digital services, particularly for computer and related services, where commitments should be made at a two-digit level to increase the scope of commitments.Footnote 150 Second, under the joint statement initiative initiated in the last WTO Ministerial Conference and the follow-up negotiations launched at the Davos conference, members are considering a plurilateral agreement on electronic commerce covering different digital trade issues, including data flows and data localisation. The more likely outcome is the adoption of a plurilateral agreement containing electronic commerce–specific rules, like the electronic commerce/digital trade chapters in certain recent PTAs, such as the USMCA and CPTPP.
Despite WTO members making various proposals for reform under the joint statement initiative (including some reforms that we propose in this article), constraints exist in achieving these reforms in practice. First, as regards regulating data, WTO members have varied views; as discussed earlier, while some members support the incorporation of provisions on the free flow of data, others have refrained from this approach to safeguard policy objectives, such as privacy protection, Internet sovereignty and cybersecurity. Aaronson and Leblond argue that the varying approaches to data regulation has resulted in three different ‘data realms’, reflecting the policy orientation of the United States, China and EU.Footnote 151 Implementing a horizontal provision on cross-border data flows and prohibition on data localisation may therefore be difficult to achieve in practice, at least in the short run. The divided approach in data regulation could be one of the key reasons why countries prefer to address data-related rules in PTAs rather than at the WTO, as PTAs provide them greater flexibility in devising rules consistent with their domestic regulatory objectives.
Second, the deficiency of binding international frameworks on cybersecurity, online consumer and data/privacy protection poses a major challenge in facilitating cross-border data flows, and may further breed mistrust among countries. Therefore, even if reformed WTO rules required all members to adopt basic frameworks on privacy protection, online consumer protection, and cybersecurity consistent with international standards, legal uncertainty will arise with regard to the appropriate international standard(s) in these areas of regulation. As it is outside the scope of the WTO to set standards or norms in these areas, the success of the proposed rules on privacy, cybersecurity and other related areas is contingent on the development of robust approaches in non-trade fora, including relevant regional, transnational and multistakeholder bodies.
Third, the emerging voice of developing countries and LDCs, especially with regard to special and differential treatment in implementing trade commitments on electronic commerce, might face some opposition at the WTO. Given the political backlash against certain countries misusing their ‘developing country’ status, some members might object to introducing a development dimension in provisions on data flows. However, as indicated in our proposal, further studies are necessary to understand the development implications of data-driven growth, including the regulatory capacity of developing countries/LDCs to respond to these challenges and introduce relevant provisions accordingly.
Finally, the extent to which the existing architecture of GATS can accommodate new rules on data flows is unclear. For example, if a new plurilateral agreement were to be designed, WTO members would have to determine the legal relationship between this agreement and GATS, including whether the existing GATS commitments would apply.Footnote 152 Similarly, given the uncertainty in applying the general exceptions in the context of data restrictive measures,Footnote 153 further dialogue is necessary among the WTO members to clarify on the scope/applicability of the exceptions applicable to data restrictive measures.
Despite these constraints, we propose that the WTO can and should play a central role in devising trade rules for the digital age. Although the electronic commerce chapters in PTAs can fill gaps in WTO rules on digital trade in the short run, they are likely to divide the global framework for data regulation, as is already evident in the divergent approaches taken by countries on data flows and data protection in their PTAs. Further, certain areas of reform proposed in this article require a high level of international regulatory cooperation. The WTO, with its widespread worldwide membership, is much better suited to act as a site for facilitating such international regulatory cooperation as compared to regional bodies.Footnote 154 Further, as suggested by the increased vigour of negotiations under the joint statement initiative, WTO members have shared interests in promoting digital trade. Given the central role of data flows in the digital economy, sufficient incentives therefore exist for WTO members to engage in negotiating rules on cross-border data flows and related issues. Therefore, we believe that despite certain pragmatic and political constraints, our proposed WTO framework on data flows remains both relevant and timely.
E Conclusion
The future of trade in digital services and data entails complex and uncertain policy challenges.Footnote 155 Thus, balancing different regulatory concerns is fundamental to ensure a coherent and sustainable regulatory framework for data flows. Being the leading multilateral trade institution, the WTO is well placed to undertake several of the required reforms to bring about better balance between promoting free flow of data while protecting a secure and stable regulatory environment for data and addressing commercial interests of consumers and businesses. However, the WTO cannot deal with all pertinent issues related to data transfer, or act on its own. Instead, the WTO needs to reframe its policy approach to engage with more relevant international and multi-stakeholder institutions and develop disciplines that address relevant dimensions of data regulation.
In this article, we recommend a comprehensive framework on data flows that covers a large range of areas that is atypical of most existing international trade agreements. Our recommendations are more comprehensive than the disciplines incorporated in the USMCA and CPTPP. However, as digital trade continues to grow, WTO law will need to respond to new policy challenges arising with increased data flows. In order to do so, WTO members must consider a comprehensive and balanced regulatory framework, where provisions for free cross-border data flows and prohibition on data localisation are complemented with relevant disciplines on online consumer protection, privacy and cybersecurity. Such an approach would facilitate openness as well as business and consumer trust in digital trade. This framework should also include rules addressing the specific needs of developing countries and LDCs to enable their inclusion into the digital economy. Although such a comprehensive framework will require increased participation, goodwill and commitment of countries, particularly under the ongoing joint statement initiative at the WTO, we believe it can eventually be more meaningful and sustainable.