Crossref Citations
This article has been cited by the following publications. This list is generated based on data provided by
Crossref.
Shang, Yilun
2013.
The Limit Behavior of a Stochastic Logistic Model with Individual Time-Dependent Rates.
Journal of Mathematics,
Vol. 2013,
Issue. ,
p.
1.
Wu, Qingchu
and
Chen, Shufang
2015.
Threshold analysis for epidemic models with high-risk immunization on networks.
International Journal of Biomathematics,
Vol. 08,
Issue. 03,
p.
1550031.
Siri, Zailan
Hasan, Siti Norfarahin
and
Ibrahim, Rose Irnawaty
2018.
Chaos of Double Diffusive Convection in the Presence of Feedback Control Strategy.
International Journal of Applied Physics and Mathematics,
Vol. 8,
Issue. 2,
p.
10.
Yang, Lu-Xing
Zhang, Tianrui
Yang, Xiaofan
Wu, Yingbo
and
Yan Tang, Yuan
2018.
Effectiveness analysis of a mixed rumor-quelling strategy.
Journal of the Franklin Institute,
Vol. 355,
Issue. 16,
p.
8079.
Souravlas, Stavros
2019.
ProMo: A Probabilistic Model for Dynamic Load-Balanced Scheduling of Data Flows in Cloud Systems.
Electronics,
Vol. 8,
Issue. 9,
p.
990.
Namadchian, Ali
Ramezani, Mehdi
and
Yan, Xinggang
2019.
Pseudo-spectral optimal control of stochastic processes using Fokker Planck equation.
Cogent Engineering,
Vol. 6,
Issue. 1,
Akman Yıldız, Tuğba
2019.
Optimal Control Problem of a Non-integer Order Waterborne Pathogen Model in Case of Environmental Stressors.
Frontiers in Physics,
Vol. 7,
Issue. ,
Vita, Vasiliki
Lazarou, Stavros
Christodoulou, Christos A.
and
Seritan, George
2019.
On the Determination of Meshed Distribution Networks Operational Points after Reinforcement.
Applied Sciences,
Vol. 9,
Issue. 17,
p.
3501.
San Juan, Jayne Lois G.
Aviso, Kathleen B.
Tan, Raymond R.
and
Sy, Charlle L.
2019.
A Multi-Objective Optimization Model for the Design of Biomass Co-Firing Networks Integrating Feedstock Quality Considerations.
Energies,
Vol. 12,
Issue. 12,
p.
2252.
Treanţă, Savin
2019.
On Locally and Globally Optimal Solutions in Scalar Variational Control Problems.
Mathematics,
Vol. 7,
Issue. 9,
p.
829.
Tang, Chao
and
Hou, Rong
2021.
Pseudo Almost Automorphic Solutions for Stochastic Differential Equations Driven by Lévy Noise and Its Optimal Control.
Symmetry,
Vol. 13,
Issue. 9,
p.
1674.
Garain, Koushik
Kumar, Udai
and
Mandal, Partha Sarathi
2021.
Global Dynamics in a Beddington–DeAngelis Prey–Predator Model with Density Dependent Death Rate of Predator.
Differential Equations and Dynamical Systems,
Vol. 29,
Issue. 1,
p.
265.
Nadimi-Shahraki, Mohammad H.
Banaie-Dezfouli, Mahdis
Zamani, Hoda
Taghian, Shokooh
and
Mirjalili, Seyedali
2021.
B-MFO: A Binary Moth-Flame Optimization for Feature Selection from Medical Datasets.
Computers,
Vol. 10,
Issue. 11,
p.
136.
Azimi, Vahid
Sharifi, Mojtaba
Fakoorian, Seyed
Nguyen, Thang
and
Van Huynh, Van
2022.
State estimation-based robust optimal control of influenza epidemics in an interactive human society.
Information Sciences,
Vol. 592,
Issue. ,
p.
340.
Balakrishnan, Ganesh Priya
Chinnathambi, Rajivganthi
and
Rihan, Fathalla A.
2023.
A fractional-order control model for diabetes with restraining and time-delay.
Journal of Applied Mathematics and Computing,
Vol. 69,
Issue. 4,
p.
3403.
Fierro, Raúl
2023.
Cumulative damage for multi-type epidemics and an application to infectious diseases.
Journal of Mathematical Biology,
Vol. 86,
Issue. 3,
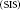 $\left( \text{SIS} \right)$ epidemic model with time-varying transmission rate and recovery rate. The infection of computers is subject to direct attack as well as propagation among hosts. Based on optimal control theory, optimal attack strategies are provided by minimizing the cost (equivalently maximizing the profit) of the attacker. We present a threshold function of the fraction of infectious hosts, which captures the dynamically evolving strategies of the attacker and reflects the persistence of virus spreading. Moreover, our results indicate that if the infectivity of a computer worm is low and the computers are installed with antivirus software with high reliability, the intensity of attacks incurred will likely be low. This agrees with our intuition.
$\left( \text{SIS} \right)$ epidemic model with time-varying transmission rate and recovery rate. The infection of computers is subject to direct attack as well as propagation among hosts. Based on optimal control theory, optimal attack strategies are provided by minimizing the cost (equivalently maximizing the profit) of the attacker. We present a threshold function of the fraction of infectious hosts, which captures the dynamically evolving strategies of the attacker and reflects the persistence of virus spreading. Moreover, our results indicate that if the infectivity of a computer worm is low and the computers are installed with antivirus software with high reliability, the intensity of attacks incurred will likely be low. This agrees with our intuition.



